It’s National Cyber Security Awareness Month once again, do you know where your security weaknesses are? Read on to find out how you can stop the leaks and block the freaks.
Internet Security, A Game You Can Not Afford To Lose
October is National Cyber Security Awareness Month (NCSAM) which means it is once again time to review your own Internet security and any changes in IT security needs you may have experienced over the past 12 months. NCSAM is the work of the National Cyber Security Alliance and StaySafeOnline.org, a non-profit organization whose purpose is to raise awareness about cyber-security and how to keep your business, yourself, your family and your homes cybersecure. This year theme for NCSAM is “Our Shared Responsibility”, highlighting the need for cooperative effort to ensure online safety for all.
- What is cyber security? Cyber security is a list of best practices for using computers and devices that connect to a local network or the Internet at large. Their purpose is to protect the safety, data and devices of Internet consumers including individuals, business, organizations and governments.

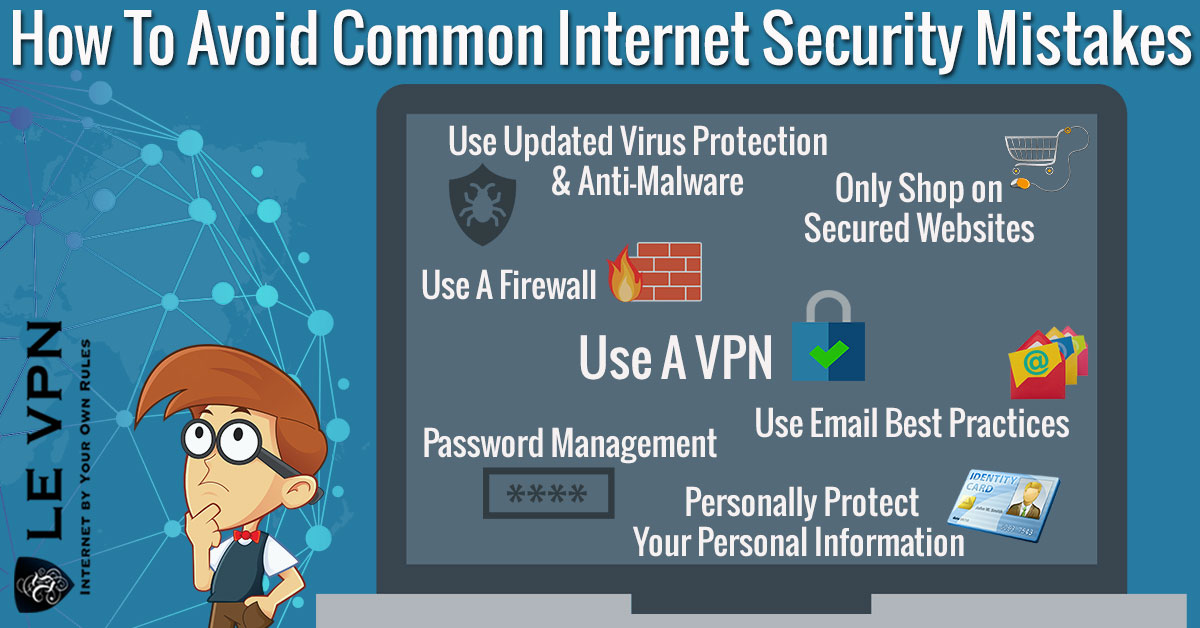
- Keep A Clean Machine – Keeping your computers free of malware, viruses and other unwanted software is crucial to personal computer security.
- Protect Your Personal Information – Loss of personal data including SSN’s, bank/credit account numbers, passwords and other important private personal data is the number one risk faced by individual consumers of the Internet.
- Connect With Care – Internet connections are where and when loss of data is most likely to occur, and where malware, viruses and hackers like to attack. Knowing how you connect and who you connect with as well as the different types of connections available is the cornerstone of information security.
- Be Web Wise – The web is in many ways a wild west of nearly unrestricted activity, both good and bad. Understanding that fact, knowing how to verify information and recognize fraud can prevent many of today’s most common abuses of the Internet.
- Be A Good Online Citizen – The Internet is a community of individuals and organizations and like any community can be abused or nurtured. Good online citizens help build a safe environment in which the community grows and shepherd others as yet unaware of the dangers of Internet use.
- Own Your Online Presence – Like Smokey The Bear says, “only you can prevent forest fires” and only you can be responsible for you online security. This doesn’t mean you have to be a techie, just that you need to be aware of the dangers involved in the Internet and actively work to protect yourself, your devices and your network security.
President Barrack Obama endorsed the creation of NCSAM in 2015 in this statement issued by the White House:
“In our increasingly connected digital world, we have the power to innovate in unprecedented ways. With the advent of new and improved technologies, we must also keep pace with safeguarding our critical infrastructure networks that, although empowering, create previously unforeseen vulnerabilities. During National Cybersecurity Awareness Month, we recognize the importance of remaining vigilant against any and all cyber threats, while recommitting to ensuring our people can use new digital tools and resources fearlessly, skillfully, and responsibly.”
Some common threats faced by today’s Internet user
- ID Theft – ID Theft, the loss of personally identifying information including SSN’s, license numbers, bank accounts and access codes, is a multi-faceted problem. Not only is your data at risk while on your own devices and networks, it is at risk while being transmitted to other devices and networks, and once received is at risk while stored in a third party server. Internet users need to protect their information at home and limit where it is shared, sharing only with trusted and secure sites. Read more about the Top 10 data breaches of all time.
- CopyCat Attacks – When your devices try to connect with other devices and networks they often send out a digital ping, letting the other device a connection it desired. These pings can be intercepted by hackers who will reply to them, tricking your device into thinking it is connected to the host it was actually seeking. In these events hackers don’t have to steal your data or money because you give it to them directly.
- Virus/Worms/Malware – Viruses, worms and other malware are software designed to dig into your devices operating system and spread themselves throughout your network and the Internet at large. Some are innocent and only interrupt the smooth operation of your device, or send out thousands of emails, some are more malicious and can take down entire networks.
- Spyware – Spyware is software installed on your device without knowledge that intends to collect information about you. It could be innocent, like web browsing habits, but it could also be much more devious in nature.
- Censors/Blockages – Believe it or not but there are more censors out there than ever and they exist in all forms. They are out there suppressing the free flow of information, blocking their countrymen from connecting with the world and using the Internet to enforce Orwellian control of politics and nations.
Over the course of the month there will be four weekly themes focusing on important issues facing Internet security today.
Week 1 is Stop.Think.Connect. An initiative to help people become more aware of the online activity and the impact it can have on their lives. The basic idea is this; stop before you connect, think about what you are about to do and then connect responsibly. Are you just going on the Internet to surf for fun, are you going online to connect with social media, to your bank or are you maybe going to look at a website that, for whatever reason, may put you or your device at risk? Are you using the right security measures to ensure you and your data are protected? Are you using an open WiFi connection from a café/hotel/airport to connect to the Internet without protecting your connection with a VPN? What are the consequences should this connection be breached or lead to loss of information? All important questions that can affect how, where and even if you connect. Risks faced by average Internet consumers include identity theft, scams, breach of home networks/devices, child safety and loss of privacy, all of which can be avoided.
Week 2 is called From The Break Room To The Board Room and is focused on ways to help create a culture of cyber security that permeates all levels of business. Businesses today are at more risk than ever and any can experience a breach and loss of data. At the simplest level, businesses risk of losing our personal information or intellectual property key to their operations. At worse, we could experience a significant break down of society if the very foundations of infrastructure (utilities, communications, banking, government, medical) are attacked, breached or worse. This week focuses on training and educating the workforce, how to implement best practices and emphasize the importance of risk management.
Week 3 is labeled Recognizing and Combating Cyber Crime. Cyber crime to many means hackers trying to steal your information but it means far more than that. In today’s Internet world cyber crime is all too common and is at least as sophisticated as many of the top websites legitimately using the web for business. Fraud, stalking, harassment, exploitation, radicalization and even terror cell recruitment are happening across the Internet even as you read this article. Fighting cyber crime is the responsibility of all net citizens and requires the collective efforts of the community, law enforcement, government and private sector business.
Week 4 is Our Continuously Connected Lives; What’s Your Aptitude. The Internet has evolved from a simple way for people to connect to a way for people to connect to everything, and for everything to connect to each other and back to you. With it has come the age of the App or Application, short for computer application, and the tools with which we interact with and through the Internet. The Internet of Things is only one example of far advanced technology has come from the original ArpaNet and how necessary it is to be, at least a little, computer savvy to get by in today’s world. Now, with that in mind, imagine how much more advanced all this will be in a year from now, or 2 or 5 or 10? This week will focus on the role of technology and its future in society, specifically its role in safety, security and privacy.
Week 5‘s focus is Building Resilience In Critical Systems. This is the shortest day of the month, only 1 day, October 31st and segues NCSAM into November and Critical Infrastructure Security And Resilience Month. The point here is the need for security in our infrastructure systems and how the public can play a role. Water, electrical, traffic and air-control systems are only a few of the many that could help cripple or shut down a community, county, state, region or country. The most important thing the individual Internet consumer can do is keep themselves safe so that they don’t inadvertently attract hackers, malware or worse into the local networks they access.
Throughout the month the underlying them of “Our Shared Responsibility” is repeated again and again. The Internet is a resource shared by everyone and like all resources, is the responsibility of everyone to manage and nurture, and to secure. The one takeaway that all Internet users should get from NCSAM is that the safety of the Internet is important to each and every one of us and that our individual actions can have repercussions and consequences far beyond their own smart phone, lap-top, desk-top, home or work network. Think about it, between financial, retail, business, news, social media and smart devices nearly every person on the Earth is connected through the Internet. A nasty virus introduced by a malicious hacker could shut it all down.
From the NSCAM website:
“No individual, business or government entity is solely responsible for securing the Internet. Everyone has a role in securing their part of cyberspace, including the devices and networks they use. Individual actions have a collective impact and when we use the Internet safely, we make it more secure for everyone.”
Internet security with a Reliable and Secure VPN Connection
Le VPN, today’s leading provider of commercially available VPN technology, is a long time champion and supporter of NCSAM. VPNs have long been a cornerstone of Internet technology and have evolved along with it right from the very earliest days. Today’s secure VPN technology operates on several levels creating secure connections with data encryption and IP masking capabilities for use of different types. Le VPN’s PPTP, point-to-point tunneling protocol, is the most basic type and great for general internet surfing, unlocking geo-restricted TV programs and other non-sensitive Internet activity. The more advanced L2TP over IPSEC provides additional security with a multi-authentication process and top level encryption making it a better choice for businesses, organizations and individuals with more advanced security needs.
The security VPN provides is at the Internet level of your connections and provides safety for your data and devices from the point of origin (you) all the way through the destination network, device or website. Le VPN software is downloaded to your computer and operating from within the individual IP packets to encrypt the data, encapsulate it into a new packet with a new IP signature and then route it through a secure, private, connection to one of its dedicated VPN servers to its destination. At the destination the software, again running from inside the data packet itself, unpacks and decrypts the IP Payload which is whatever data was sent from your device ie log in details, password, a post to social media, a work report, whatever. The beauty of VPN is that it combines two different security protocols, encapsulation and encryption, which ensures that connections are as private as possible and that if your data is ever intercepted no one will be able to read it or follow it back to the source.
Le VPN’s protocols and servers can be used by Windows, Mac, Linux and other operating systems as well as by mobiles and tablets including iOS and Android. The applications are endless and include surfing the net on a public non-secure (internet cafe, airport) system, masking IP addresses to unlock geo-restricted content, protect your data from “innocent” data collection by every website on the internet, using a personal computer and/or remote location to log-in to a work or home network securely, accessing websites free from the prying eyes of watchdog organizations censors or unfriendly government agencies and so much more. Read more about the security advantages of using a VPN.
Using Le VPN is as easy as click and go. Once you sign up for the service, use your account credentials to log-in to the servers of one of 100+ locations around the world, listed by country and connection protocol, and your connection is set, secure and private. The cost is minimal, as little as $4.95 per month, and when compared to the risks presented by even the most casual surf across the web is well worth it. So why wait to do your part to make the Internet safer for everyone? Get your VPN now!
SUMMER SALE
First 3 years for $2.22/mo
NO LOGS
100+ LOCATIONS
P2P ALLOWED
Easy To Use
30-Day Money Back
Friendly Support
Bitcoin Accepted
Ultra High Speeds





Written by Vuk Mujović @VukMujovic
Vuk Mujović is the founder of MacTíre Consulting, an analyst, data management expert, and a long-term writer on all things business & tech. He authored blogs, articles, and opinion pieces aimed to help both companies and individuals achieve growth without compromising their security. Vuk is a regular guest author to Le VPN Blog since January 2018, where he gives his expert opinion on the topics related to cybersecurity, privacy, online freedom, and personal data protection. He also often shares his tips and best practices in relation to internet security and digital safety of private individuals and small businesses, including some additional applications of using a VPN service.