Internet Of Things And Your Privacy
There is a not-so-new buzzword floating around, you may have heard it. The Internet of Things. This shadow Internet has been slowly growing in the background of our lives and has reached massive proportions. Unlike the Internet, the regular Internet that is, populated by people, the Internet of Things is populated by the machines and gadgets of every day life. It is a movement to put computer chips into every thing in our lives in order for them to have “connectivity”. Connectivity means they can share and receive data, hopefully for the purpose of enhancing our lives. Connectivity is a good thing when it allows our devices to function more efficiently, it can be a bad thing though when it means your every move is being tracked.
The Internet of Things is all the devices, vehicles, buildings, machines, clothing and gadgets with onboard technology enabling them to collect and exchange data. It has been labeled the “infrastructure” of the information age with applications far beyond the mere exchange of data. True IoT means that devices can be accessed and operated across an existing framework in a manner that improves efficiency in cyber and real world scenarios. Taken to the fullest extent IoT utilizes sensors and other inputs along with wireless technologies and micro-electromechanical systems to control the very environment in which we live our lives.
The term was coined in 1999 with the rise of the Tech Bubble. The incredible advance in technologies led British innovator Kevin Ashton to envision a world where advanced levels of connectivity led to automation in every field and in every aspect of life. Applications for IoT range from smart homes and self driving vehicles to automated traffic control lights in a smart city, and even heart pace makers that send and receive information, and can be adjusted remotely per patient need. Needless to say the potential for hacking, malware or loss of privacy in this connected world is without bound.
One side effect, and target for attack, of the IoT is the massive amount of data being generated, transferred and stored. Each time one device connects to another, or reaches out to a website for information, the risk of loss and hacking is present. Protecting personal information can be a challenge but there are solutions.
Security And The Internet Of Things
For the individual the home network is the center of the Internet of Things. As it grows and new devices and functionality is added, the need for linking grows. For the most part this means internal linking within the local area network, but in many cases outward access is also required. Some devices will need to access information from a website, or you as the individual will want to remotely access and manipulate your home from the office or other location. Regardless of the need this access is a target for hackers and malware.
Address Resolution Protocol (ARP) is only one of many methods that can be used by malicious third parties to access your home network. ARP is a common protocol used by IoT devices for mapping network addresses to physical addresses and can be easily fooled by a technique called spoofing. Hackers can act as intermediaries between the home network and an outside server by duplicating automated responses and tricking the system. The spoofer is then able to intercept any data being transferred from your home network and can even launch denial of service or other attacks.
Spoofing attacks are not limited to Internet of Things and smart homes. They have been used for years as a means of infiltrating private networks of all kinds by imitating the networks own router. Network tapping is one of those innocent sounding cyber words with a darker more sinister side. At face value any device or software with the ability to access your network is network tapping, nothing to see here. When used for malicious purposes however, things look quite different. If your wireless network is left unprotected, it can be accessed by anyone. Any device with a wireless chip can be used to access your network which makes it a target and, once compromised these chips can then be used to locate the network and launch an attack on you at any time in the future.
The attraction of unprotected networks, home or business, is just too alluring for hackers to leave alone. Some go so far as to drive around in their cars using modified gaming and other mobile devices to locate and map out the locations of unprotected networks. There are even websites like Wigle.com that show maps of vulnerable networks around the world ready and waiting for someone to come access them. And if this isn’t enough there are other concerns with IoT safety as well. Take for instance used IoT devices. It may seem like a good idea to buy less expensive used devices but they can be used to access your entire network or introduce malware if previously compromised.
Here’s an example of just how vulnerable the IoT is, and how much damage can be done if the wrong network is hacked. A team of student researchers at the University of Michigan School of Computer Science and Engineering showed in 2014 how a local traffic light network was vulnerable to attack. They worked alongside local authorities to breach a network controlling 100 traffic lights and were eventually able to turn lights on and off at will. Their work revealed a number of flaws in the system, the primary one being connectivity between the traffic lights and the controller.
Even the most innocuous of devices is at risk. In January, also 2014, investigators were tracking an attack of global proportions; not against the devices but from them. The source of the attack was eventually tracked to a mini-refrigerator, IoT of course, that sent out more than 750,000 spam emails through a network of over 100,000 connected devices. While spam is not that big a deal in most cases this serves as an example of the vulnerability and potential for loss of privacy and security that exists within the IoT framework. Next time it might be something a little more sinister.
Malicious intent isn’t limited to the “black hat” hackers who are out to steal your credit card data or insert malware into your network. The very makers of the devices which comprise the Internet of Things have their own agendas and can not be assumed to have the best interest of the end user in mind. They collect data on how the device works, they track its use and they collect data on the users. This data may be used to enhance your experience but could just as easily be sold to a third party, accidentally leaked or stolen. Making things worse, the apps that drive the devices are known to access multiple domains in the course of their operation and each time open the user to loss of data or worse.
Believe it or not, lovers of Internet privacy and security are not fans of IoT. Sure, there are many, and I mean thousands if not millions, of good uses for connectivity and the IoT but in the end, do you really need your shirt to tell your watch your heart rate and then send the information to your fridge so it can decide what food you need to buy and order it online from an automated network in Walmart? Not really, especially if your data is leaked along the way. It’s nice to know you can control your home’s thermostat or audio/visual system from your laptop, or that warehouse inventories are being kept up to date instantly, but there is a limit to how connected we really need to be.
The real danger lies in the sheer volume of devices that are going to be connected, in our lives and in our businesses, and it only takes one to allow a major catastrophe to happen. Each one that connects to your network is a potential threat, they know intimate information about you and are potential access points for intruders, malware and loss of information. The least that could happen is your contacts are compromised and spam originates from your devices, at worst you suffer a complete loss of data or control of your network, devices and machines.
- BlueTooth – Bluetooth is a wireless technology standard used for exchanging data over short distances. It uses short wave UHF radio frequencies in place of data cable to create small personal-area-networks and to connect devices in close proximity to each other. The Bluetooth enabled feature will include a radio antenna that is used to send and receive signals from other enabled devices. One of the many positive features of Bluetooth is that one can connect multiple devices together at once and eliminates problems with synchronization found with other networking methods. A very common use for Bluetooth, for example, is connecting your smartphone to the car you are in and playing the music from your phone on the car’s speakers. In terms of IoT, Bluetooth is one of the communications protocols that make it work. The Bluetooth standard is maintained by a group known as The Bluetooth Special Interest Group which ensures that manufacturers using the Bluetooth logo meet requirements. The technology uses a number of security features to ensure that connections between devices are secure but they are not fool-proof. Several flaws have been found over the years including a cracker which has been shown to penetrate the PIN system.
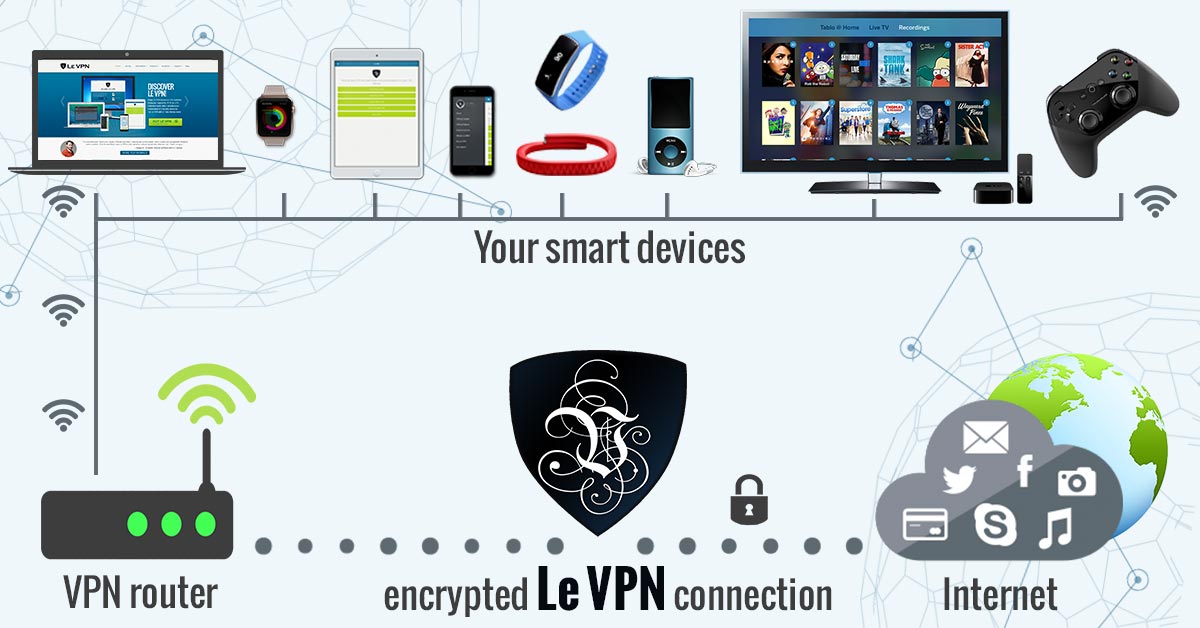
The only way to be sure your network isn’t being compromised is with encryption. Some devices come with this feature embedded but you would be surprised at the number that do not. To avoid this hassle simply set up your personal use devices and routers using a VPN for IoT. VPN, virtual private network, uses several different protocols including top level encryption to provide a seamless secure connection from point to point. They also mask you IP address by rerouting your traffic through a network of dedicated servers so that your location, data and privacy are safe from attack. Le VPN is the leading VPN provider today with solutions for all levels of IoT networks and compatible with the majority of routers, smartTVs, game consoles and other smart devices.
Here’s Our List Of Suggestions To Help You Stay Safe While Using The Internet Of Things:
- Always use screen lock and/or password protection for your internet connected devices. This will help prevent unauthorized casual access.
- Never, ever use the same password more than once. Always use a hard to guess combination of upper and lower case letters, numbers and special characters whenever possible. Using different passwords at every site compartmentalizes your information so that when one site or password is compromised the others remains safe.
- Always turn BlueTooth off when not in use. You never know what IoT enabled device may try to connect with you, harmless or not, or when you may unknowingly leak data.
- Be sure to read the privacy policy of any device or software you connect. Pay close attention to how they store data and how it is used. Also read the policies of any websites or devices with which your information may be shared with.
- Share as little data as possible with any device, website or software you encounter. The best method of protecting your information is for it not to be on the Internet at all, short of that make sure it is in as few places as possible.
- Think twice before allowing a website or device to share information with social media. Social media sites are notorious data miners and can, and will, collect any information they can about you, your devices, your web-surfing habits, purchases and anything else they can access. Something as simple as checking in at a pub while on vacation can let the wrong people know you are away from home/office and increases the chance your network is targeted by hackers.
- Most IoT devices are able to use geo-location, GPS or other technology to pinpoint your location and the location of your networks. Be sure to limit this whenever possible by disallowing these features.
- Always update apps, firmware and operating systems. It can be a chore, I know, it seems like some apps are getting updated every day but there is a reason. Updates can improve the functionality of the service, and they can improve existing security and plug any gaps found in earlier versions. If you get hacked or infected with malware because you did not update your software there is no one to blame but yourself.
- Is it possible to add a security solution to your device, sensor or network? If so do it. Every layer of security you can add is one more to help stop data leaks and impede malware.
- If your device can use encryption technology there is no reason not to do it. This is the last barrier between your privacy and the world wide web. If all else fails, and you do suffer data loss, encryption means whoever ends up with your information will never be able to read it, let alone use it.
- Install and activate a VPN on the router that shares WiFi with your IoT devices. By securing the Internet connection on your router, you are automatically protecting all the devices that connect to it.
VPN And The Internet Of Things: IoT Security
The opportunities for breach of network and loss of information associated with IoT security are too numerous to count. Needless to say I think it safe to say by now that there are many layers of security that need to be addressed ranging from the safety of your local private network to the safety of your connections when transferring information over the Internet at large. VPNs, virtual private networks, can’t solve all the security problems but they can address a couple of major issues faced by IoT networks.
VPNs in effect create a private network on the web through which your IoT connected devices can safely communicate amongst themselves as well as safely connect to the Internet. This is especially important in IoT devices because of one thing, low computing power. The average IoT device does not have massive amounts of computing power, they don’t need it to perform the limited tasks that most are required to perform. This means there is little room for onboard security features and bulky encryption software which means they are highly susceptible to hacking, and their data is at risk when traveling over the Internet. When your devices are connected through a VPN such as Le VPN all connection are encrypted and routed through a secure tunnel directly to the destination.
Some IoT devices like smartTVs and game consoles are compatible with a VPN and you can easily install a VPN connection on each of these devices, but this is a time-consuming endeavor. The easiest way to protect all your smart devices in your home is to set up a VPN on your home router. This way all the devices that connect to your home WiFi will be connecting to the Internet through a secure encrypted VPN tunnel, keeping all your smart devices protected at all times. Setting up VPN on routers is easy and you’ll only need to do it once to protect all the IoT devices of your home or office.
One of the many advantages of using a VPN is encryption. Encryption is a standard part of VPN services and ensures that even if your connection and/or information is ferreted out by hackers or malware it will not be readable. Another major benefit important for IoT networking is IP masking and geo-location. VPN’s mask IP addresses and geographical location from prying eyes, and can be set up to appear as if you are located somewhere you are not.
There are three types of VPN protocols available from Le VPN. The most basic is PPTP, Point To Point Tunneling Protocol. This is the least secure of the VPN protocols as it does not provide encryption on its own but is still useful for basic network security and those with low risk of hacking. L2TP, Layer 2 Tunneling Protocol, brings enhanced security to the VPN tunnel through multi-level authentication and encryption technologies. This type of VPN was designed specifically for the internet and ensures privacy along with a secure connection. OpenVPN is the highest level of VPN security available. It is an open source protocol that uses SSL, Secure Socket Layer, to create authenticated, encrypted connections to the internet.
The Internet of Things is here to stay. The benefits of a connected world just outweigh the risks. This does not mean that there are no risks, or that you should avoid them. Quite the contrary. In order to make the most of the IoT the risks must be faced, and they must be addressed with IoT security measures. This means implementing a full-scale security plan including a VPN on your smart devices or on your router. VPNs ensure encrypted, secure connections that offer a 100% protection of your network, so what are you waiting for? You know you have devices connected to the Internet right now, make them safe with Le VPN.
*Article updated on August 10th, 2018*
SUMMER SALE
First 3 years for $2.22/mo
NO LOGS
100+ LOCATIONS
P2P ALLOWED
Easy To Use
30-Day Money Back
Friendly Support
Bitcoin Accepted
Ultra High Speeds






Written by Vuk Mujović @VukMujovic
Vuk Mujović is the founder of MacTíre Consulting, an analyst, data management expert, and a long-term writer on all things business & tech. He authored blogs, articles, and opinion pieces aimed to help both companies and individuals achieve growth without compromising their security. Vuk is a regular guest author to Le VPN Blog since January 2018, where he gives his expert opinion on the topics related to cybersecurity, privacy, online freedom, and personal data protection. He also often shares his tips and best practices in relation to internet security and digital safety of private individuals and small businesses, including some additional applications of using a VPN service.