Not to sound all gloom and doom, internet security issues have not seen 2017 as a good year. With multiple hacks, ransomware getting rampant and several major hardware manufacturers reporting flaws in the security microcoding of their products, 2018 is bound to be a year of significant changes in the world of cyber-security.
This doesn’t mean that we should forsake all technology and go live in the forest, but some precautions should be made and sensible users will try to protect their information in whatever way it is possible. Those with companies working with sensitive data should consider, if they haven’t already, taking in a dedicated in-house security expert to assist them in creating a more resilient system, and home users should consider keeping their most treasured data on a separate flash drive, and always using a VPN (Virtual Private Network) service when browsing, even on trusted websites.
The amount of security should match the value of data you are storing on your drives or in the cloud. This is not only applicable to your desktops and laptops but also your phones, tablets and other devices. Installing a VPN on all of your devices will ensure that you will be harder to find and thus your data will not be able to be sniped by malicious persons or software.
Top 10 Internet Security Trends In 2018
1. Careful patching and AppTesting improvements
When talking about internet security, most people still imagine malicious websites that are accessed over the laptop or desktop, even though most of our internet browsing is now done over the phone. Mobile applications have become the bread and butter of all modern hackers and even the most accredited of apps have become victims of hacking in the last year.
While the original software is usually safe and tested, not much is done when testing patches and updates, and even less when testing third-party additions or alterations. While the mantra of most coders is ‘’don’t fix what is not broken”, many applications work fine only on the outside, while on the inside they have multiple security issues and backdoors.
For those who only wish to use their phones and other smart devices safely, there is a number of measures that you can take to protect your smartphone or tablet. For those who are developers, the road is not as easy as they will need to invest much more in application testing of even the smallest patches. All software is created equal, meaning with bugs, and the developers need to be aware of the security risks and to deal with them on time, optimally before the app launches.
2. Ransomware and dealing with it
Ransomware is seen as a problem of big industry players and individuals with deep pockets, but in the future starting with 2018 this may cause wider concerns and even impact casual users worldwide.
Ransomware is a type of software that focuses more on stealing your private data in the terms of pictures, videos, and writings, than bank accounts. Most people have something embracing or sensitive on their phones that were meant for private eyes only, and are willing to pay to have access or to prevent the datanappers from sharing the material.
In creating ransomware, hackers usually focus on the operating systems like Windows, Android or iOS or proprietary software made for those platforms. In 2018 this will create major security concerns for millions of people, as it is common for people to use that software and have sensitive data on the same device.
The solution to this problem is to be proactive and to protect your information beforehand. When combating Zero-Day Vulnerabilities (flaws made in manufacturing) there is no way to be aware of illegal access while using the phone. That is why you should keep your most sensitive data separately whenever possible, be sure you have the most recent updates to your operating system and have anti-malware software installed on all of your devices. Using a VPN connection is also advisable, as it will prevent you from being singled out for specific information you might have. VPN alone is not enough to protect you, but it will make it impossible for people looking for your data in particular to find it.
3. IoT Home – Smart yet gullible
With more and more of our devices being connected to the internet and having smart capabilities, we are seeing a rise in device hacking. The ease of access for hackers and other people with malicious intent is not so much due to any faults in the devices themselves, but more often than not in human error. Once we have more than ten smart devices in our home we are prone to leave passwords and settings in default which makes even the rudimentary attempts of hacking easy.
In 2018 it is predicted that there will be a rise in botnets which will attempt to access your devices from multiple points with all basic passwords attempted, finally breaking devices that don’t have a higher security setting.
The only way to prevent this is to be careful and to install all of your devices properly; giving them personalized settings, username, and password. There is a very pedestrian way to remember all passwords on all devices, and that is by printing a sheet with all data, then clearing the temporary files on the printer.
While hacking has come a long way, there is still no way to hack a piece of paper in your desk drawer.
4. Child reputation protection
Children born in this century will never know the life as it was before the internet. While in many cases this is a good thing and will prevent a lot of paper cuts, in others it can pose a significant threat to their reputation, influencing mental health and adult life in the future.
As 2018 will see an increase in stickiness from the software and websites provided by a big corporation, we should be prepared to protect our children from the damages this massive data collection can have on their lives.
Parents should be vigilant and prevent their children from browsing through websites without supervision. We must make sure that all of our devices are protected and that even the devices our children use have anti-malware and VPN services installed. Posting pictures of your children should always come with a second thought whether the website you are posting the picture is safe, can the picture be downloaded, and would this picture, video or any other material be shameful or disrespectful towards your child once it is an adult.
From the technical side, always be sure that you have provided protection from malware, spyware and even cookies. From the ethical side be mindful when posting pictures of yourself and other people online, even if those other people are your children.
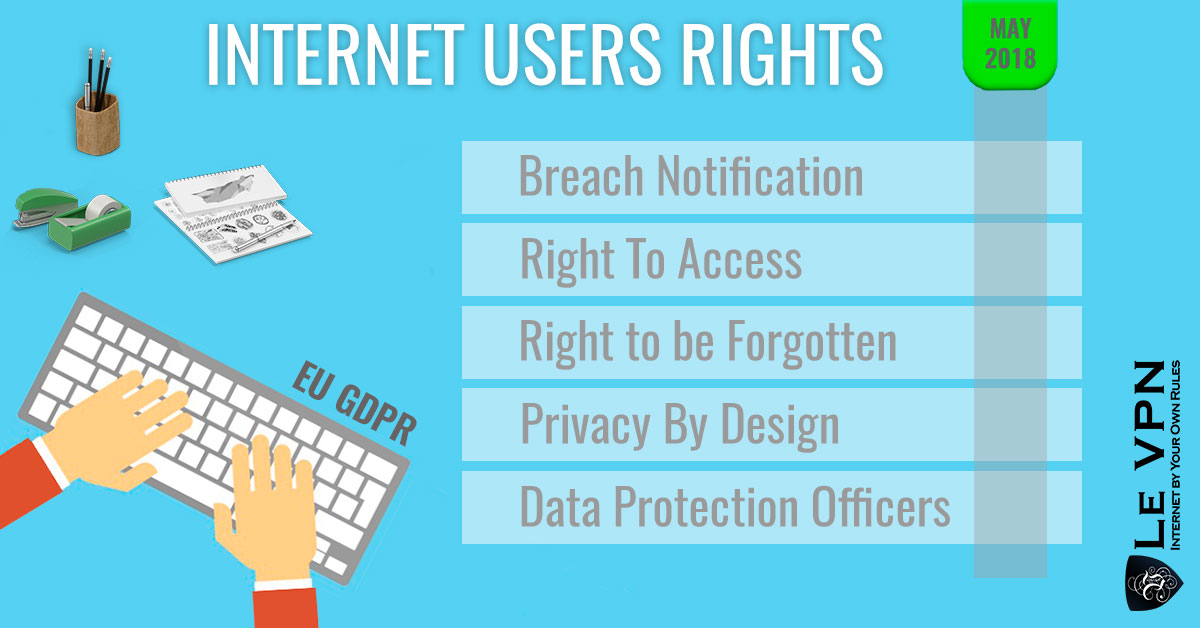
5. General Data Protection Regulation (GDPR)
What you may think about the GDPR depends on which side of the aisle you are sitting. For companies and developers, the introduction of Europe-wide safety measures for personal information may create a hurdle, and if those measures are not implemented by the 25th of May 2018, companies may be fined a considerable amount of up to 4% of global annual turnover. While implementing these features is not as difficult, companies struggling to stay in the black will see this as an obstacle to doing their job.
If you are a European consumer, this will be seen as a good use of your tax-euros (for once) and a great help to your overall internet security and personal information protection.
With this regulation, there will be a systemized European law that will regulate how companies and institutions in all EU member states must collect, store and distribute personal information. Also, all legal entities will need to fully disclose how, where and why are they keeping your private information.
Once this regulation is in power, EU residents will have a legal cure against identity theft if it is due to a lack of protection from a specific company. It will also be illegal for marketers to keep your information without your direct consent, which you can withdraw at any moment.
6. Serverless apps and protectionless devices
Using apps that don’t require a server has become very popular in the last few years with services such as WhatsApp and Viber providing direct peer-to-peer (P2P) connections with inbuilt encryption. While this does reduce the cost of application maintenance and give all kinds of utility benefits, it is very open to various forms of attack.
The primary way of breaking into a device that uses P2P apps is to exploit the dependencies in the device itself. If there is a flaw in the device and its security, a serverless app will be an open door for malicious attacks. Another problem is the potential attack on data transit throughout the network, as focused Denial of Service (DoS) attacks can overwhelm the system and disrupt any operations.
This is where using a VPN becomes a must-have and when you should learn how to make your VPN even more secure. Every time you use your IP address from an unsecured device in an unsecured network you are opening yourself for a direct takeover of both your device and your data. Using a VPN here will prevent almost all malicious attacks on your system and even help the VPN provider track down the origin of malicious attacks, making the internet safer for everyone.
7. AI Hackers
As technology progresses we are seeing more and more tasks being done by AI, it was just the matter of time hackers would employ AI to do their bidding. Although we are far from Skynet level of threat, the last two years have seen an incredible increase in AI made attacks. Machine learning is used by hackers to note, track and even predict vulnerabilities in systems. Malicious software assisted by AI has made DoS attacks much easier and cheaper to do, making the #6 on this list even more important.
Some may see this as a problem, and there is no question in whether you should keep your data and information protected and backed up just for this occasion, but in the long run this will prove to be the arms race that is developing AI capabilities even faster and to create new ways to protect our information even further.
The whole issue should just promote greater care about security for an average consumer, who should think about professional software from reputable companies to use as their protection. Staying protected, having the latest updates and using a VPN will mean that you will not have to welcome our robot overlords, yet.
8. Shortage of cyber-security experts
For those who are thinking about a career change, this is the way to go in 2018. Cybersecurity experts are few and far between as all companies who do anything with the internet now need some sort of internet protection and most don’t have the funds for an experienced in-house security expert. Even in larger companies, most cyber-security experts are consultants working on a retainer for impressive fees and are in charge for several companies at the same time.
If you plan on opening a company in 2018 you basically have two options; either scraping the money for a dedicated expert or using the online service of reputable protection companies that will give you the optimal security and support for a much reasonable fee. This includes good anti-malware software, anti-virus software and a reliable VPN provider. Most major corporations worldwide already use these services as consulted by their security expert, and there is no reason why shouldn’t smaller companies and even private persons.
9. Rush toward a common language
The same way vaccines, once most people have them, provide herd immunity, the same way a common internet security language provides a tighter net of security experts who can learn from each other and make significant advances in creating security software and protocols.
This push for a global approach to internet security has created a revolution of high-end protection services that are already available to most people, and should soon be available to everyone. Making a common language for all security experts worldwide will slightly assist the fact that there is so few of them, but as the number of experts rises and more people assist in making solutions we should see a much faster pace in security software development.
In the end, this will mean that if you are using services of one reliable and reputable internet security provider, you are most definitely using solutions that were created by the best minds on the whole planet.
10. Revenge of the DoS
If you have asked someone in 1988 what is DOS, they would tell you that it is an innovative and reliable operating system. Thirty years later in 2018, and DoS is the most dreaded way hackers and malicious software attacks applications, systems and websites, preventing people from accessing their data and, in most severe cases, making considerable losses on the parts of both companies and individuals.
All innovations made by people who want to steal your data and hurt your business has led to a golden age for DoS attacks and to a need for constant vigilance when handling our data.
DoS attacks are now even made by casting a wide net and not aiming for any website, company or person specifically. This means that you could be denied service from any application even though you have no sensitive information on the device. While this may not destroy your life in the same way an identity theft would, it will still create an inconvenience if you have not taken measures to protect your data and your device.
Summary: How to ensure your internet security
Internet security trends change every year, but every year the overarching message of those trends is: stay vigilant!
If you want to be sure that your devices are protected and that your information if safe both from hacker and malicious software and from people just wanting to sell junk to your children you should always take measures and be prepared. Even if you think that you are not a prime target for these attacks, that doesn’t mean that you will not be attacked regardless, or used as a testing ground for a bigger attack. If you make yourself a hard-hitting target hackers will usually not even bother, making you even safer overall.
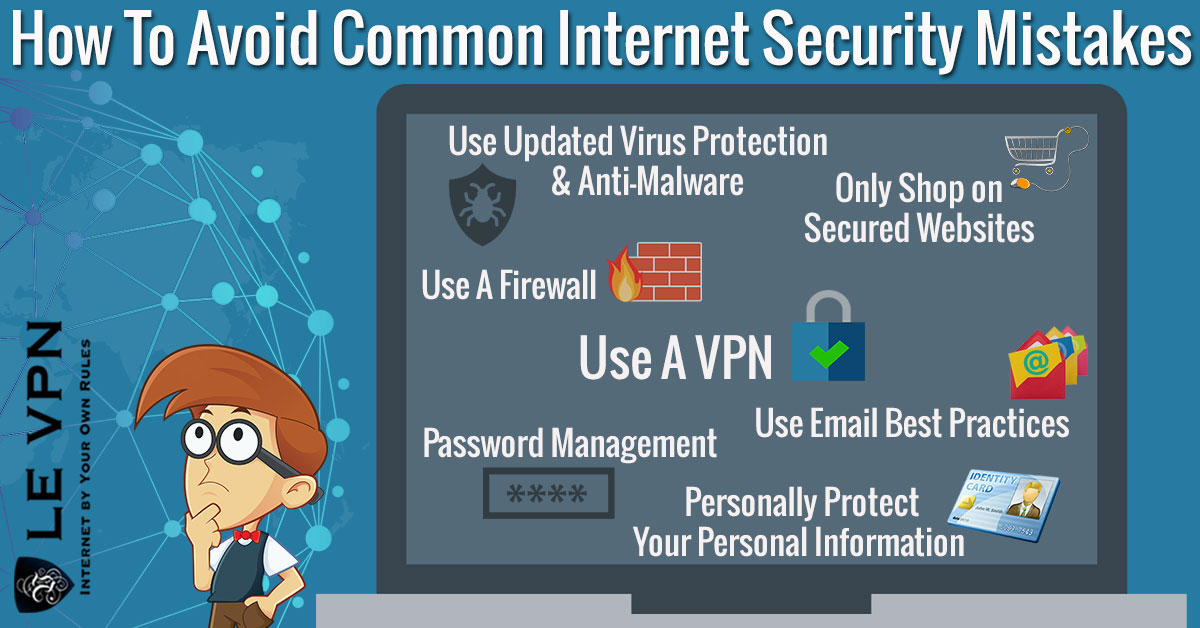
To conclude, there is a relatively simple list of things you need to do to make yourself safer:
- Read the fine print
Read all agreements and terms of service and be sure that you agree with them. It is only boring until it becomes painfully interesting. - Update, encrypt and password protect your devices
Redundancy is the mother of safety. Make sure you have all the measures before even using your device. - Backup your data
If it is important, it is not a problem to have it somewhere safe on a flash drive, just in case. - Install anti-malware
All of your devices need an anti-malware software, and all should have them. Updated, protected and from a reputable source. - Download only trusted applications
While some apps that are not from reliable sources may seem fun, if they were safe they would usually be in a trusted store. Tread lightly. - Don’t jailbreak your phone
You would know this if you have read the terms of service. If you can use your phone differently from intended, the same probably goes for people who want to hack your phone. - Turn off WiFi and Bluetooth when not in use
Both can be used to access your device remotely, and your devices will connect to networks without prompting you, meaning you wouldn’t know if you are under attack. - Use a VPN
You should use a reliable VPN provider whenever possible and from all devices that are connected to the internet. Having a VPN will give you considerable benefits for a very small dose of work.
Once through the chart, you can be reasonably sure that you are protected from almost all malicious attacks. Don’t forget to go through the same steps for every new device and for every new update.
Stay safe!
*Article Updated On December 21th, 2018.*
SUMMER SALE
First 3 years for $2.22/mo
NO LOGS
100+ LOCATIONS
P2P ALLOWED
Easy To Use
30-Day Money Back
Friendly Support
Bitcoin Accepted
Ultra High Speeds






Written by Vuk Mujović @VukMujovic
Vuk Mujović is the founder of MacTíre Consulting, an analyst, data management expert, and a long-term writer on all things business & tech. He authored blogs, articles, and opinion pieces aimed to help both companies and individuals achieve growth without compromising their security. Vuk is a regular guest author to Le VPN Blog since January 2018, where he gives his expert opinion on the topics related to cybersecurity, privacy, online freedom, and personal data protection. He also often shares his tips and best practices in relation to internet security and digital safety of private individuals and small businesses, including some additional applications of using a VPN service.
Comments (1)
Good article and excellent way to articulate, keep it up