Although we can all agree that the title of this technology and its application forces us to immediately assume surveillance and police work, we have to at least start wondering about its use and whether in part, or as a whole concept, it invades our rights and privacy.
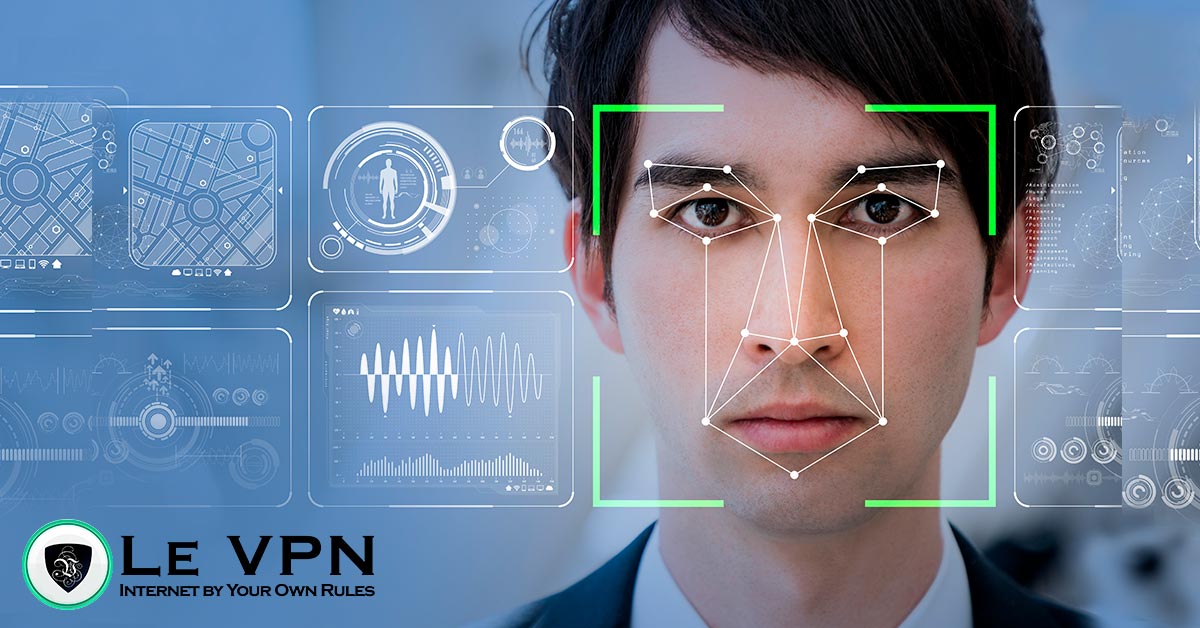
To start with, at the very baseline and initial application, the traditional use of face recognition resorted to the use of algorithms in order to identify facial features (analyzing the position, size, and shape of the eyes, nose, cheekbones etc..), while in the early stages of its development the initial approach was done through the use of template matching techniques resulting in compressed face representation.
We can divide basic or so-called traditional approach to two distinct ones:
– Geometric, focused on distinguishing features;
– Photometric, resorting to statistical approach, where the image is broken down into values and compared the values associated with already existing templates to eliminate discrepancies.
Before we even begin to contemplate about risks and benefits of this technology, let us agree that most of the people on the very mention of face recognition either think of a police state or are immediately concerned what the next step could be. How did it come to this?
Before face recognition was even possible and available for larger use then just by state agencies and airports, some people suggest that just like we all have very distinct fingerprints and that the same line of thought could be attributed to our facial features.
The scary thing about face recognition is related to a simple fact that it does not require permission nor cooperation of the individual it has been applied to. We certainly know and are aware of face recognition systems at airports and various other places that can easily identify an individual in a crowd of people, without the rest even being aware of it. This is different to regular network security, but there are some ways to protect yourself.
Nobody suggested or indicated that they are working perfectly and in terms of reliability, there are numerous factors that can affect the performance of said systems (illumination, expressions, pose and noise during face capture) thus the rejection and acceptance rates in terms of its success vary.
Of course, the privacy issue is one of the biggest concerns especially pertaining to companies storing biometrics data, as it poses a risk of unlawfully obtained.
As far as other techniques are concerned, few seem to stand out when it comes to basic concept and approach. Three-dimensional face recognition technique uses 3D sensors to capture information about the shape of a face. This information is then used to identify distinctive features on the surface of a face, such as the contour of the eye sockets, nose, and chin.
One advantage of 3D face recognition is that it is not affected by changes in lighting like other techniques. It can also identify a face from a range of viewing angles, including a profile view. But, as previously noted even 3D matching technique is not foolproof when it comes to expressions.
Applications go as far as skin texture analysis that uses the visual details of the skin, as captured and then uses mathematics to discern lines, patterns, and spots apparent in a person’s skin.
The last resort of technological companies was to combine all available techniques (traditional, 3D recognition and Skin Textual Analysis), in an effort to design a recognition system that would have more success.
A combined technique has an advantage as it appears to be more reliable when it comes to changes in expression, blinking, frowning or smiling and has the ability to compensate for mustache or beard growth and the appearance of eyeglasses. The system is also uniform with respect to race and gender.
Individual vs. the World: We are not Alone!
The presence and impact of social media platforms in 21st is enormous, and at times too difficult to bear, as it seems there is no escape from it.
From Looksery to SnapChat we are viewed through a lens and although from layman’s perspective that should be no problem, let’s pause for a second and just think of one word – the selfie! Add GPS location to your selfie and there are unlimited possibilities for things to go wrong. We did not even touch DeepFace, (facial recognition system that was created by a research group at Facebook), which enables identification of human face in a digital image.
Yes, we note the useful application when it comes to policing, national security, CCTV, satellite surveillance and all sorts of possible uses and benefits but rather then going into an obvious rationale behind it, lets venture briefly into the realm of controversies and/o privacy violations.
Civil rights right organizations and privacy campaigners worldwide have continuously advocates and battled against face recognition stating that our privacy is being compromised by the use of surveillance technologies. Total surveillance society argument can also be added to the list but isn’t it already so? Use of credit cards, mobile phones, and similar gadgets leaves you undoubtedly prone to monitoring and surveillance and those who say – if you have done nothing worn, you have nothing to fear, have successfully missed the topic completely.
The scary truth is revolving around the fact that face recognition can be used not just to identify an individual, but also to unearth other personal data (photos, blog posts, social networking profiles, Internet behavior, travel patterns, etc) but what is scarier then that is actually the fact we have no knowledge who is watching and when and why. Individuals have limited ability or no ability to avoid face recognition at any given point in time unless they cover their faces completely.
This fundamentally changes the dynamic of day-to-day privacy by enabling any government agency, or random stranger to secretly collect the identities and associated personal information of any individual captured by the face recognition system. On the same token, the same individuals then are not only unable to understand (or be aware of), what their data is being used for, which denies them the ability to consent to how their personal information is used or better said abused.
Needless to say, the biggest and certainly most important concern deals privacy. Facial recognition technologies used by large companies, such as Google or Apple, could be very well viewed as mass surveillance of the public. But what happens to the basic idea that goes along the lines that in general people do not wish to have their every action monitored, recorded or used. We believe and stand for living in a free society, we should be able to go out in public without the fear of being identified and monitored.
How does it Work and what can We Do About it?
The evolution of face recognition is an ongoing process. We also tend to laugh at old celebrity mug shots and police records but that seems to be ancient past. Although facial recognition software is no news, the widespread of its use creates far more than just potential issues. At the very start let’s touch base with its superb potential for data misuse, improved techniques for scammers and ultimately complete loss of privacy.
While there are ways to keep your face out of the system, such as staying anonymous at all times while on the internet and only connecting through VPN to the internet, this solution only works if you are isolated from the world. Reputable VPN providers like Le VPN will guard your devices from their cameras being hacked and used to survey you, but not even them can guard you from public CCTV cameras and satellites.
Artificial intelligence back in the day was subject of sci-fi novels and movies but nowadays it is literally everywhere and we need to do everything in our power, as individuals to make sure proper safeguards are in place and that AI is being used for good.
If we do it properly, thoroughly, the ethical and strictly regulated use to these types of technology can indeed improve security, but at the same token, it could be also used for fraudulent activities. The truth is that regardless of its futuristic attributes, technology isn’t foolproof and still needs human intervention.
As concerns arise, so does the legal regulation that is aimed at preventing large-scale abuse of personal information. In addition, we should be aware that the technology is evolving at a higher pace then legislation, thus we can predict some major concerns in the near future, such are corporate data gathering and government surveillance. Most IDs now have biometric data and this biometric technology is used to fuel face-recognition technology. Meaning, your DMV photo might be used to track your face.
We do remember Edward Snowden very well, (Government use of technology in terms of monitoring other countries and even their own citizens), so mass surveillance with the use of facial recognition is certainly not part of a fairy tale but deep in the reality of things.
An all known fact is that Facebook was the first social media platform website to introduce the idea of tagging someone in a photograph. This is where facial recognition came into play. This particular feature was labeled as just one of the means for Facebook to gather even more data on their users. Important to note, all members were auto-enrolled in this particular Facebook feature. The European Union even decided that Facebook’s facial recognition was an invasion of users’ privacy and blocked its expansion inside the EU.
Facebook isn’t the only company to experiment with facial recognition for photo organization and tagging. Most major photography software, including offerings from Apple and Google, also use facial recognition to group photos. The main difference between Facebook and the others is that Facebook determines the identity of the person in the photograph.
Businesses and advertisers have an incentive to capture as much data as possible about potential customers. The increasing availability of facial recognition software has made it affordable for them to start using it.
New technologies present governments, businesses, and advertisers the chance to further erode your privacy. They also represent technological advancement which, given the right circumstances, could benefit us all. Unlike social networks, there is very little control you can exert over the collection of your image. Governments and law enforcement agencies are likely protected under law to collect the data. Security at large events is usually going to be covered under the terms of entry to the event.
Off course attempts have already been made by villains of the virtual world (hackers) in an effort to trick facial recognition software but thankfully, it has proven to be harder to replicate then, for example, voice recognition or a fingerprint. It is not a question of hack and possibility for fraudulent activates as facial recognition is used as a security measure for a wide range of business and consumer applications so the main concern should be: is it really necessary and to what extent it intrudes in our daily lives.
When it comes to the aspect of data privacy, the data that is stored about your face could be subjected to an unauthorized access by third parties thus subjected and susceptible to misuse.
Where did My Face Go?
In most instances, face recognition system is being used, as previously noted by either law enforcement agencies or big companies who want to target potential customers. While most people would turn their head and walk away thinking nothing is wrong with that, some would loudly voice their concerns in terms of choice we made, had or did not have at all. Civil rights groups argue that we have a fundamental right to privacy and that wanting to be anonymous does not mean we have something to hide. We should have a choice to be identified or not at all.
But how will we know whether we’re being remotely identified or not? Sadly, even when confronted with such questions, most government agencies and private companies are unwilling to accept that they should always seek permission first before obtaining and using this type of data.
Then do we have any rights at all? Well, in Europe, companies have to seek your permission first before using facial recognition technology for commercial purposes. This is why Facebook has decided not to offer its photo-sharing app Moments in the region. Alas, merely two states in the US (Illinois and Texas), have embraced Europe’s approach. In the UK, the Data Protection Act stipulates that we have to be informed when we are under camera surveillance and by whom. We also have the right to request any recorded images we feature in.
That certainly did not solve privacy issues as it tends to be almost impossible to know when and how our images are being used and whether our right to privacy is being respected. The digital surveillance possibilities and many companies have less or no trust that regulators will ever be able to find a proper balance when it comes to legislation and implementations of such rules and guidelines.
Advantages and Disadvantages of Face Recognition Technology
In order to make a full circle and establish a proper and better understanding of this technology, we have to also recognize a few advantages and disadvantages when it comes to face recognition.
It is biometric software that is able to identify an individual from a digital image by using mathematic algorithms and mapping it in a similar way we would store the information from a fingerprint. This is done in three major steps of face recognition:
– Detecting a face;
– Scanning and creating targets;
– Matching and verifying.
Pros:
- Improved Security – A facial biometric security system could very well be perceived as an alleviated level of security. Every individual that approaches or is already in the designated (monitored area) is captured and by the same token, anybody who is not allowed to be there, is quickly and efficiently detected. It could very well be one of the reasons that can impact the total costs of security.
- High Accuracy – Combining all available techniques (traditional, 3D and Skin Textual Analysis) makes face recognition technology more accurate and more successful.
- Fully Automated – The facial recognition technology is now fully automated in terms of the whole recognition process, ensuring its accuracy at a very high rate.
Cons:
- Scarce Data Storage – Data storage requires space. This indicates that in order for facial recognition systems to be efficient, they only process about 10-25% of the data they collected. To combat this, many companies use many computers to process everything and to cut the time it takes to do so. Until technology significantly develops, this obstacle remains without a proper solution.
- Insufficient Camera Angle – The camera angle is one of the instances that has a major impact on whether or a not a face is processed. In order for a facial recognition system to completely identify a face, it needs multiple angles, including profile, frontal, 45 degrees and more, to ensure the most accurate resulting matches.
All facial recognition technology is no doubt faced with promises and challenges. It won’t be too long until such technologies would be so far evolved that they would not have any issues or concerns in terms of processing expressions, combating different angles and dealing with changes in facial appearance with facial hair, hats, sunglasses and such. Until that time, we can resort to staying at home or wearing a cap, strolling hooded or moving to the Middle East as some of the options.
Conclusion
While the adaptation of face-recognition technology is eminent with the further development of face-recognition software, there are things we can do to protect our biometric privacy. Primarily, keep your own devices out of reach of any malicious entity on the internet by practicing your privacy. If you use Le VPN as you VPN provider you will have privacy, at least from your own devices. Even still, you should keep your face away from social media, by simply using an avatar. Your friends will still know that it is you, but neither the government nor the hackers really need to have that info.
Finally, if you think that this is a major overreach by the government and the corporations you can always inquire if you can assist privacy advocates such are the American Civil Liberties Union and the Electronic Frontier Foundation that are fighting for privacy protection.
Stay Safe!
*Article Updated On February 20th, 2019.*
EXCLUSIVE DEAL
First 3 years for $2.22/mo
NO LOGS
100+ LOCATIONS
P2P ALLOWED
Easy To Use
30-Day Money Back
Friendly Support
Bitcoin Accepted
Ultra High Speeds




Written by Vuk Mujović @VukMujovic
Vuk Mujović is the founder of MacTíre Consulting, an analyst, data management expert, and a long-term writer on all things business & tech. He authored blogs, articles, and opinion pieces aimed to help both companies and individuals achieve growth without compromising their security. Vuk is a regular guest author to Le VPN Blog since January 2018, where he gives his expert opinion on the topics related to cybersecurity, privacy, online freedom, and personal data protection. He also often shares his tips and best practices in relation to internet security and digital safety of private individuals and small businesses, including some additional applications of using a VPN service.
Comments (1)
nice