When promising to ourselves that we will try to stay digitally safe in 2018 and follow the best network security practices, we have to recollect how 2017 was a very challenging year for cybersecurity: state-sponsored attacks, The Equafax breach, Russian manipulation of social media, WannaCry, NotPetya, GoldenEye, Uber, numerous ransomware attacks that were flooding newspaper headlines, and an overwhelming number of internet scams, including phishing scams, Tinder scams, and more.
There are many concerns, which are still growing with every passing year. Experts try to keep us up to date in order to provide a grasp on how to build a strong foundation for the new level of network security needed in our daily routine. The scope of cybersecurity evolves as fast as capacities of computing itself. When summarized, cybersecurity can be represented as a set of techniques to protect the security, availability, and integrity of your data. In this age when hackers are being more inventive than ever and with growing AI technologies, there is an evident risk with a greater variety of potential threats for anyone.
As experts predict that there will be more automated attacks with a non-targeted approach, it might be a good idea to keep yourself prepared for being exposed to network security risks, as to keep them down to a minimum.
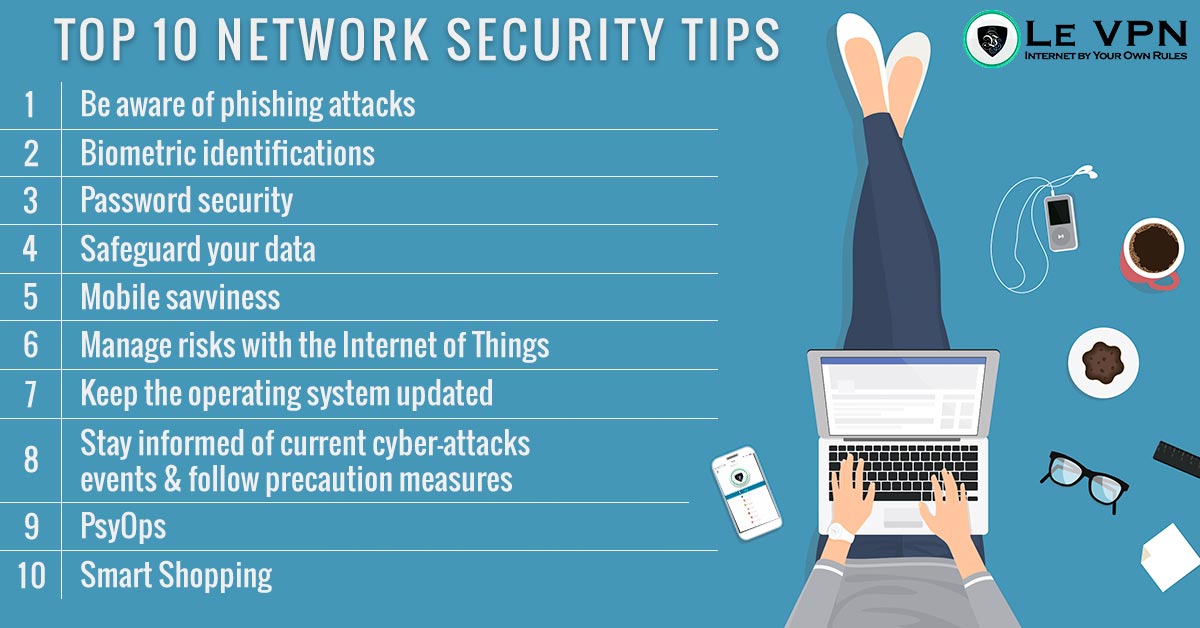
Top 10 Network Security Tips for 2018
1. Be aware of phishing attacks
If you want to keep your data safe, don’t be foolish and go on a phishing expedition. The invention of phishing scams is old as the inception of the internet, and these scams are not going anywhere soon. This is still a very popular tool to create profit for cybercriminals of today and they are being really creative and getting more innovative when developing new phishing techniques. When it comes to cyber safety on this issue it is best to stay tuned and informed as best as you can as new scam risk arise daily. Be wary where are you pointing your cursor when clicking. The next click might be fatal if you open links from unsolicited emails or direct messages. There are some telltale signs such as to hover over the link. If you want to check its validity, it should mirror the URL where it supposed to lead. In unfavorable cases, if you open an email that could be from a legitimate company, it can lead you to a page that looks similar to the real website. The site will require filling in your personal information but before you do that check to whom that email is intended to. Usually, the phishing email start with ‘’Dear customer’’ and not your name and this is the first sign that you should be on high alert.
Another form of phishing treats are pop-up windows and they can be concealed as a legitimate part of the site but instead, it is an attempt of phishing attack in disguise. It is important not to click on ‘’cancel’’ button as this is the gate-away to an untrusted link, just use the X button and close the window. These annoying attacks can be easily prevented by using pop-up blocker that can be installed as a plugin in many popular browsers and set a case-to-case rule.
Most importantly, install a good antivirus that can keep you protected from untrusted sites and update it regularly.
2. Biometric identifications
With raising technology requirements and potential threats, there are new and inventive ways on how to obtain personal information and keep the integrity of its owners as safe as possible.
In cybersecurity, integrity means that only authorized people should be able to access or read specific computer systems and data. Biometrics identifications systems are based on using biological characteristics of humans as a way for personal identification, as this is something uniquely distinctive for each individual.
Experts in this field are expanding and adopting new unique personal ID indicators to develop safe identity theft prevention systems to prevent issues related to this problem. Some of the most common are fingerprint recognition, and with the adoption of new AI technologies using eye iris and retina recognition, face recognition, hand recognition, and even gait as a behavioral biometric to recognize a person individual walking style or gait to determine identity. With this kind of safety measures being introduced in our everyday life like in airport security, building access, and cars, we are gradually being introduced to this technology on a more personal level.
As this is one of the core features in this area, it will be more and more introduced as a primary method of authentication for personal devices such as mobile phones. We already have on the market the newest Apple iPhone X and Huawei Honor 9 featuring fingerprint sensors and facial recognition, and this is being included in many other android phones on the market today.
These methods have been already implemented on the market for over a decade but now as growing AI technologies are being more reliable and accessible, they are on a good heading to overthrown the almighty password.
The Asian market has been working on iris scanners for a while now, and they currently have first smartphones emerging on the market using iris scanner as a primary method of identification.
We might not be aware how future is closer than ever and that we can be a part of this stage in technologic evolution just by taking the next step in precaution measures for our own, and our family’s safety on the network and using devices with access to it.
3. Password security
The new hackers are attacking almost everyone and defeating many systems in the process. Today, almost anyone can launch a DDOS attack or ransomware and, with new technologies rising, black hat organizations have faster tools with broader range for performing attacks. With raising AI technologies, we can expect to have wider spread instances of automated and non-targeted attacks.
If you are taking network security seriously and think of possible cyber-attacks as something that can happen event to you, it is imperative to take that into consideration and follow latest safety tips. But, with this risk in mind, how to be sure that your password is the safest possible that you can make, and remember afterward?
Basic tips should be already obvious and well known, for example not using the same password on multiple accounts, not using actual words, using upper and lower cases and symbols and not using personal information in the password. But with new trends, it is not easy to manage how to keeping up with the safest methods while still having an easy time remembering all the passwords you need.
Here are some easy Password security tips to follow:
-
Include numbers and characters.
To have a strong and complex password that will not be easily cracked, the password should include numbers, letters, and symbols. But the tactic that involves using numbers instead of letters like ‘’0” instead of ‘’O” is something that hackers already have a lead and have software to recognize them, and that goes for characters also. One way to go around that is to avoid using a capital letter at the begging of your password but to use a character instead.
-
Use 8-word phrase to generate a coded password.
When creating a strong password using all tips above it can be easy to come up with the password.
One easy way might be just bashing your hand on the keyboard to generate a unique password. And the result is 2oiu43t*deg&%j8u and with 16 mixed characters with numbers, symbols and letters it can be a perfect example of a really strong password. But a problem might arise and that would be how to memorize something you just smashed on your keyboard.
One way is to create a side story to remember to turn that around use a sentence to create a memorable secret code. For example: “The last house I ever lived in was 948 Fake Street. Rent was $900 per month.” When encrypting that to your password you should get TlhIeliw948FS.Rw$9pm. That seems like a fairly strong password with 21 characters and all you need to do is to remember those 2 sentences. This is just one of the techniques so feel free to be creative.
-
Lie when answering security questions.
It turns that in this case, it is very encouraging to lie. When nowadays portraying your life choices on the internet it can be easily found by simple google search your possible choices for security questions like the name of your dog or names of your family members.
-
Change your password regularly.
It is advisable to regularly change your password in about 90-120 days to keep your data safe from the hackers.
-
Use a password manager software.
To keep track of all of your passwords, it is the best choice to use a software for managing passwords like Dashline or LastPass.
4. Safeguard your data
With a number of ransomware scandals flooding the newspaper headlines, it can now present a serious threat to common individuals as it does to companies (read on about the 7 main reasons cyber threats target small businesses).
One of the safest investments is storing your sensitive information is to use external HDD drive separately from your computers you can always have a copy of your data and back up information kept safely. In past few years, many online storages based on cloud computing were promoting a safe way to store your data. A user who would practice using these services will have to know that data still can be threatened if the password is weak and data not encrypted with the latest security protocols. With predictions for 2018, some experts believe that hackers will be targeting cloud-based platforms for their data heists.
Some users don’t like to take any chances with cybercriminals and they will take network safety measures to the next level and that would include encrypting the data.
Many users won’t think that the encryption of the whole hard disk is necessary, just some specific files and sensitive information. For that purpose, the most well-known free encryption software is 7-Zip and it will offer a lightweight solution and with a simple interface. For full disk encryption, there are numerous encryption software solutions like VeraCrypt, Bit Locker, FileValut 2 and of course DiskCryptor.
Also, it is advisable to use a VPN service as to protect your IP address from being pinpointed where an automated hacking program can find everything about you individually and just preset it to a hacker. Using a reputable VPN provider such as Le VPN can erase this problem in its entirety.
5. Mobile savviness
With Android being most popular mobile platform investigations show that 97% of the mobile malware attack is targeting Android users.
Investigators from F-labs have been experimenting to get an idea how users are being fooled into installing bad apps and compromising the data from their mobile phones. Google Play store is the least possible place to get a malware-infected app being that Google is tirelessly working to prevent any of the apps in their store to be attacked by trojans. But beware that many apps that have adds in them can be an effective tactic for pushing malware content in mobile browsers and making the bandwidth being reduced, slowing down the system and compromising the device to be in control of the cybercriminal.
Best advice for keeping your mobile devices safe is to lock your phones and not download apps from unofficial stores and sites with adds that could put you at risk. It would also be wise to install a reputable anti-virus and a mobile-friendly VPN service on your mobile phone, reducing the chances of a digital infection of your device to a minimum.
The VPN provider that we use, Le VPN, is also available on Google Play and is one of the best VPN apps on the market today. It is especially important to use a VPN when you are connecting through a free Wi-Fi or to Wi-Fi hotspots, as this creates a number of security risks for your mobile device.
6. Manage risks with the Internet of Things (IoT)
In this age, there are more and more appliances that require a connection to the internet and with that, the concept of how to manage the risks of the Internet of Things (IoT) might be as vague as it is broad. This depends on what kinds of appliances are used and how they can be a potential threat. There have been some cases that hackers managed to hack into baby monitors and, for any parent, that might be the worst nightmare.
But this topic should be left open for future consideration when thinking about safety on the network. The key part is to make sure that devices are connected to a safe network, that they are using one port that is being protected and that, if you don’t trust your ISP, you will need to use a Virtual Private Network for your entire home.
7. Keep the operating system updated
As this is one of the most tedious actions you will need to take, even though it has been mentioned a thousand times, it still has not been adopted as one of the crucial safety measures for your information. New updates and builds offer more up to date performance and are aware of new attempts of hackers to endanger your data.
Microsoft, for example, will provide patch and updates to keep the hackers on their toes as they will relentlessly work on finding new ways to attack the system.
When developers are looking to invent new ways how to make the OS safer, they are also providing bug fixes and enhancements to prevent malicious malware exploiting the weakness of the operating system. Windows operating system can be updated automatically and consent is just a click away. Enter the settings for update performance for whichever time is the most convenient for you and you will not need to bother with the system updating at the worst possible time.
8. Stay informed of current cyber-attacks events and follow precaution measures
Prevention is the best cure and it is easy to prevent problems when you are being well informed and prepared. If you are reading this article then that is a perfect example of following this rule. But keep an eye on any events that might be a potential threat and present more interest in reading articles on similar topics.
When you are well informed, you are in a better position to protect your data and to keep your friends and family well informed by presenting an example how to put safety first.
9. PsyOps
Not to sound overly dramatic but, there are threats which most of us can’t even imagine and most commonly underestimated threats are that we can be exposed to by using social networks.
This is something that many of us failed to recognize as a treat and potential way to steal personal information and use it or sell to other companies for profit without our consent. This includes many types of tests and quizzes on Facebook that requires personal information from your friend list. This is usually a gateway for targeted marketing and ads but experts believe this is a one way to conceal a potential malicious treat to your device, and your friend’s devices as well. Check out our tips for a more secure Facebook account.
10. Smart Shopping
It might just well be that shoppers online are placed at most risk as their personal information can be easily connected with their credit cards and financial accounts and that’s what many cyber-attacks are direct to. Even though these systems are not that easy to hack, it is the most direct way for malicious entities to profit, and thus most hackers will focus directly on obtaining your personal data.
Users who like to order online usually need to put in their credit card account numbers that can be tracked down with their social security numbers and put them at most risk for identity theft. This might be the scenario that has been heard over and over again just to warn the user to take safety measures and think twice before leaving their sensitive information online.
This type of sites should offer safety measures like two-factor authentication or shortly 2FA or TFA as an acronym. Data breaches are occurring on daily basis and cybercriminals are always working on inviting new ways to have control over your accounts. But 2FA authentification method provides an extra layer of security. Sometimes this will involve SMS verification or email authentication or in some other cases, tokens can be used as a way to leave out the cybercriminals unable to connect your account to your information.
Also, you should use a VPN for safer online shopping from your home, as there are countless malicious software that will make a connection between your name, IP address and financial information, making identity theft an easy deal for any hacker.
SUMMER SALE
First 3 years for $2.22/mo
NO LOGS
100+ LOCATIONS
P2P ALLOWED
Easy To Use
30-Day Money Back
Friendly Support
Bitcoin Accepted
Ultra High Speeds




Written by Vuk Mujović @VukMujovic
Vuk Mujović is the founder of MacTíre Consulting, an analyst, data management expert, and a long-term writer on all things business & tech. He authored blogs, articles, and opinion pieces aimed to help both companies and individuals achieve growth without compromising their security. Vuk is a regular guest author to Le VPN Blog since January 2018, where he gives his expert opinion on the topics related to cybersecurity, privacy, online freedom, and personal data protection. He also often shares his tips and best practices in relation to internet security and digital safety of private individuals and small businesses, including some additional applications of using a VPN service.