Cybersecurity is a vast field of not only research and theoretical knowledge, but also practical solutions and tools that help the average user protect their property, their data, and their very identity. One of the critical factors of cybersecurity is anonymity, as the best way to beat malicious entities such as hackers, various corporations, and even some governments, is to evade them entirely. The goal of anonymity is not to diminish your experience on the internet, but rather to externalize the cost and time consumption of the protection against hacking and data collection to a professional company that has the best possible tools to protect from this engagement while enabling your safe and anonymous browsing online.
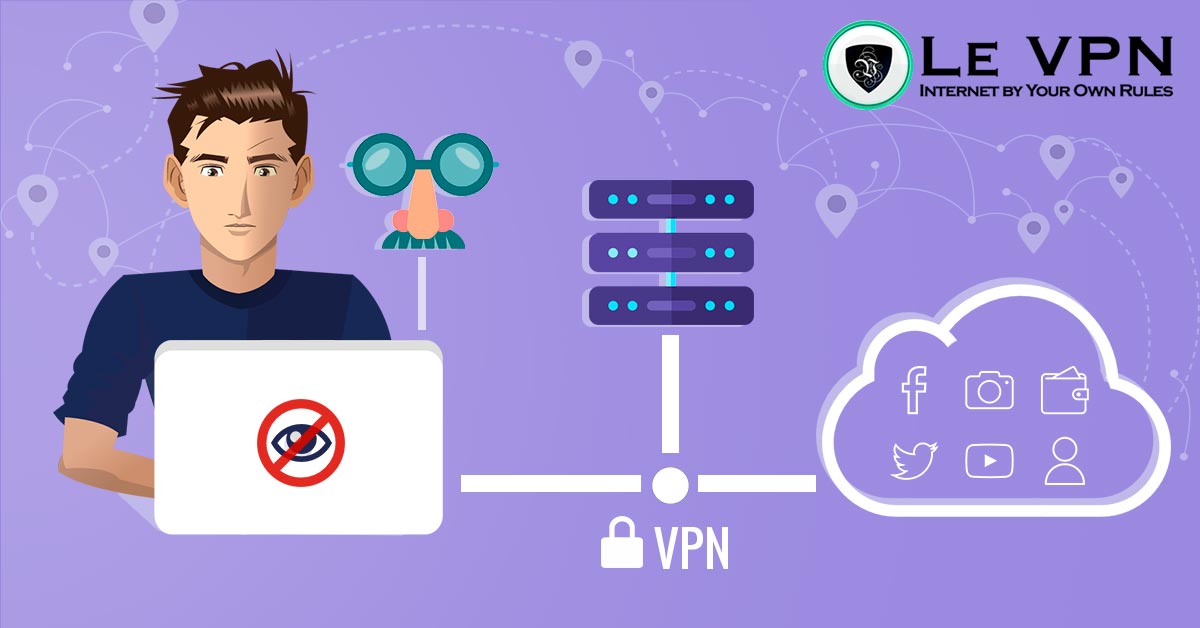
The main tool when trying to obtain internet anonymity is to have a virtual private network (VPN), and professional providers like Le VPN offer various other tools which will help with this goal. That being said, every user should know other solutions that can complement this type of defense. As internet anonymity comes in two forms, technical and personal, both approaches must be considered to ensure your safety and the ease of your browsing. While complete anonymity is virtually impossible, optimal anonymous surfing, where no entity will be able to determine your identity from the data they have is not only in your reach, but quite affordable.
Why Should You be Anonymous on the Internet?
Some experienced internet users might see this issue as further violence against the proverbial deceased horse, but it is of the utmost importance to remind ourselves about the basics again and again.
Knowledge is power, and humans like power, especially those incorporated into international businesses. Companies like Google or Apple are literally following your every move and recording your every transaction, while social media giants like Facebook (Instagram is a part of Facebook) are even using your images for computer learning protocols. For some people, this would be inevitable, but this should only include people who aim to profit from sharing this information. Even in those cases some data should never reach the internet and should be protected by all costs.
Aside from corporations, there are hackers, who will hold your data ransom, steal your identity, or sell your data to the corpos, there is an ever-looming danger of government overreach when it comes to private information. Some might think that living in the US excludes them from this last issue, but the NSA spies on most US citizens, and we should never forget that almost a hundred of our compatriots are currently on an all-expenses paid vacation in Cuba, in Guantanamo, courtesy of the NSA.
Not implying that you should directly fear the patriot act, but just not having to deal with any of these issues will make your stay on the internet, as well as your browsing activities, much easier.
How Safe is Your Privacy?
Some people have misconstrued that with the GDPR in power in the EU, and similar legislation brought in several US states will prevent the malicious entities of the internet endangering personal data and ensure online privacy. The thing is, data mismanagement and selling were already illegal, to begin with. This data is not placed on the market by legal means but is mostly traded in backroom deals and shady consulting fees.
If you haven’t done anything to protect your data, and you are using social media such as Facebook, web browsers such as Google Chrome, or accessing a web page with the IP address provided by your internet service provider (ISP), you are already marked. The fact that you do your web browsing using Chrome’s incognito mode just means that you are unable to see what you have browsed, but Google still remembers everything, from your browsing history to your passwords.
Who is Collecting Your Data?
Not to repeat ourselves, but Google still remembers everything, and so do Microsoft, Apple, Amazon, and many others. From individuals that deal with identity theft to companies and corporations, all up to national governments, everybody likes a good census.
While some of this data collection might be seen as benign, such are shopping services and coupons. Anonymous web browsing is the only way to be certain that none of the more malicious elements have access to your data.
Finally, the companies and governments have data leaks in regular intervals today, and even if they don’t plan to do anything bad with your data, they might leak it to someone who does.
Two Types of Internet Anonymity
Regardless of your browsing habits, there are two aspects to consider about anonymity online, and online privacy in general. On the one side, there is the technical anonymity, which applies to the visibility of your devices and the web pages you access from your IP address. Even if you have never stated your real name online, if you don’t have a VPN or a proxy connection, your web browsing will still be connected to your IP address, which is connected to your internet utility bill, which you pay with your credit card.
On the opposite side, there is no VPN in the world that will protect you from seeding your information in plain text over social media. To be honest, most ‘’hacks” are done by simply asking the person for their username and password, pretending to be someone else. This is why it is very important to adjust your browsing activities as to comply with cybersecurity etiquette and to mind your social media posting. You shouldn’t even have your real name online, let alone your personal address, phone number, or credit card data.
Staying Incognito: Top 10 Solutions for Anonymous Browsing
There are multiple solutions for safe and anonymous browsing, and while it would be ideal for every user to use all of the available tools to protect themselves, this is usually impossible due to time restraints. It is up to the individual user to determine which the optimal configuration is best for their browsing habits.
At the very least, every user should have an updated operating system, a premium VPN connection, a good anti-virus program, and an anti-spyware app that regularly cleans malicious software.
1. Assume a Persona
Probably the easiest way to reach personal anonymity is to assume a persona of an imaginary character. The people you know in real life will know your pseudonym and it will be easy for them to find you online, but you will be a mystery for all others. There are many ways to approach this subject, the common practice of your home street and your first pet might be problematic as those are some common security questions and should not be shared.
Our personal favorite is using names of secondary characters from English, Russian and French classical literature. Presenting as Eugene Rastignac will not only conceal your real name from any malicious entities but will also indicate on your social views to those who recognize the name. Additionally, borrowing a pen name is not a bad idea. Andrew Belis sounds like a common name, and there are even people who are called like this, but it is actually the pen name of Samuel Beckett, the author of ‘’Waiting for Godot’’.
2. Proxy Connections
On the other side of the spectrum, a proxy connection is something that will mask your home IP with the IP of the server you are connecting through. While not the ideal solution for everyday use, using an anonymous proxy server will prevent apps like uTorrent and Vuze from sharing your IP overtly over P2P connections. This way, your real IP address, the one provided by your ISP, will be substituted with the one from the proxy connection and will not be traced back to you.
3. The TOR Project
Aside from being one of the most interesting pieces of open source software that came out in the last decade, The Onion Router, for which TOR is an acronym, is like a proxy connection on steroids. The software will connect your TOR with other TOR browsers on the TOR network across the world, using multiple jumps and links to change your identity every time you open a new window or tab. Your original IP will still be out there, as other people will use your device as a proxy in the same way you are using theirs, so it is advisable to use a VPN regardless, but this is a perfect way to conceal both your digital identity and your physical identity.
As of late, there is a TOR browser for Android, as well as one for Apple’s iOS, meaning that you can be as safe when outside as you are in the sanctity of your home.
4. Using a VPN at Home
Using good VPN software is a cornerstone of personal cybersecurity. This is reserved only for either protected home-built anonymous VPN, which is rather expensive, and to reliable and professional VPN providers like Le VPN that provide protection for all of your home devices. Additionally, Le VPN has various protocols such as OpenVPN that allow for greater security even when connecting directly with other users via P2P. This doesn’t just include your PC, laptop, and console, but also any of your smart appliances and peripheries, like your printer, or even your fridge. As more and more devices around the home are getting an internet connection and send data to their manufacturers, investing in a VPN router might be a good idea at some point.
Using a VPN will delegate any attempts of hacking from your home to the VPN web servers, which are virtually impenetrable with current technology.
5. Using a VPN on Mobile Devices
Your VPN should not be relegated to your home, as most people do much of their shopping and browsing over their smartphones, while they are out of the house. Regardless of your data plan or the mobile browser you are using, you will still be sending personal information to the internet. Because of this, you will need to make sure that you have VPN enabled at all times, on all of your smartphones.
Engaging in VPN online shopping will not influence your data consumption or your shopping experience, and it will protect you from any type of interception, or the possibility of your credit card details being stolen.
6. Using a VPN Hotspot App
Not only is using a VPN essential for your protection when connecting to unknown networks, such as a café, or at the park, but it can also be used to access some services that might be blocked from direct access. This is usually done while on a break at work, as you will probably need a VPN to unblock Facebook or other social media that are blocked by default. Obviously, you can unblock websites other than social media, but this is the most common example.
Using a good VPN hotspot app will prevent MITM attacks on your device, as you will be accessing the wi-fi network through an encryption tunnel, and not over the wireless router directly.
While there are multiple options when selecting a VPN hotspot app, if you already have Le VPN as your provider you will have access to their app, which works on all mobile platforms such as iOS, Android, or Windows Mobile.
7. Ensure Cybersecurity Stability
We should understand that not all cybersecurity tools are equal, and that there are some options that are available with some solutions that are unavailable with others. One of these aspects is the stability of your defenses. While ‘’cybersecurity stability’’ sounds like a complicated term, it is actually just the certainty that you will not be accessing the internet without your defenses being up.
The easiest way to go around this by using apps that already have a VPN kill switch. This little bit of security protocol ensures that your connection with the internet will be severed if there are any problems with the VPN connection. With this addition, you can be certain that your phone will not send data to its corporate master while in your pocket.
8. Limit Social Media
While this might sound like a repeat of the first point in this list, we are referring to the limits to the apps and web pages and not to your personal use of the services they provide. This point also includes every web browser, especially Google Chrome, as well as any other app that uses your personal data. Go into the settings and select that you don’t want to give your location, your microphone, and video access, as well as access to your browsing data to the service.
Additionally, try to limit public access to your profiles, your images, and any other information that you may have, as to avoid prying eyes from people whose services you are not using, and which you don’t know.
9. Remove Geo-tagging
The same reason why you should limit access to your physical web information from other people, you should prevent web-based services from identifying your location. Aside from being both a digital and real-life security risk, it is utterly creepy for Google to follow you over satellite. As almost every android device today needs to have a Google account to operate unless you use a VPN service on your phone and remove geo-tagging, you will be tracked to ten feet around your device, even in rural areas.
10. Clear Cookies
Most anti-spyware software apps will have this feature included, but you can clear cookies with your operating system as well. Almost expectedly, your device will bloat if it consumes too many cookies, as apparently there is such a thing as carbs for AI as well.
Clear this data regularly, even if you only browse through a virtual private network, as they will slow your device down and can pose a mild security risk. The best course of action is to make your operating system, or your anti-spyware clear this data on a regular basis.
When Should You Start?
Ideally, you should go back to 1994 and start then, and if that was possible, it already happened. String theory temporal paradoxes and jokes aside, there is no time like the present. Spend a day scrubbing your social media, enabling your VPNs, and updating your defense software. This is a rather small effort that will bring you’re a lot of security, as well as peace of mind when browsing and shopping online.
Always Go, Professional
Always remember the mantra of online security: ‘’If you are not paying for the service, you are the product.” Google, Facebook, and Twitter are free because they are getting your data and your marketing potential. Investing in cybersecurity doesn’t cost much even when considered nominally, and when you compare this with $90.000 which is the average cost of an identity theft case, the sum becomes truly ignorable.
Conclusion
Every time the subject of online security, data protection, and anonymity online comes up, we need to remember that no potential danger means that we should relinquish the positive aspects of the internet altogether. You should enjoy all of the advantages that web shopping, online communication, and modern entertainment have to offer. But, as with real life, everyone should take a few precautionary measures as to go around their business freely and without fear that someone will do them harm.
If you are using a premium VPN service such as Le VPN, and maybe add a few other solutions to your arsenal, you will be able to surf free and safe to your heart’s content. Cowabunga!
SUMMER SALE
First 3 years for $2.22/mo
NO LOGS
100+ LOCATIONS
P2P ALLOWED
Easy To Use
30-Day Money Back
Friendly Support
Bitcoin Accepted
Ultra High Speeds



Written by Vuk Mujović @VukMujovic
Vuk Mujović is the founder of MacTíre Consulting, an analyst, data management expert, and a long-term writer on all things business & tech. He authored blogs, articles, and opinion pieces aimed to help both companies and individuals achieve growth without compromising their security. Vuk is a regular guest author to Le VPN Blog since January 2018, where he gives his expert opinion on the topics related to cybersecurity, privacy, online freedom, and personal data protection. He also often shares his tips and best practices in relation to internet security and digital safety of private individuals and small businesses, including some additional applications of using a VPN service.