Proxy connections are at a strange point where they are both overvalued and undervalued, depending on who you ask. While some argue that you should hide proxy connections and either use a VPN or nothing, others believe that they can be just as good.
To determine this, we need to know what is a proxy connection and how to use it. Generally, proxy connections do four things:
- Connect through a different device
- Mask the IP address with one of the proxy computers
- Receives all of the internet data through a proxy
- All devices connected to the proxy share bandwidth
Here we can see that the only thing separating a good proxy connection from a terrible one is trust. Technically speaking, a proxy server can be as secure and capable as any VPN server. But, the price and maintenance involved, as well as a diminished bandwidth, usually means that it won’t be as good for long.
And, if the proxy is bad, you will literally be giving all of your information to a hacker. Here, you won’t have any control over what you are sending or receiving.
Especially now, when premium VPN providers like Le VPN offer security for multiple devices for relatively cheap, it might be a better option to hide proxy connections and just use a dedicated and encrypted server.
What is a Proxy?
Before we can know what is a proxy and what can be the benefits and risks of using one, we must first understand what an IP address is and how it is used on the Internet.
Your IP address, similar to your personal address, is a location you cite to other people, or in this case, a computer, so that they would know where to send the information you have requested.
You disclose your IP address to others so that they can send their web pages, emails, or software to your home PC, phone or tablet. Your IP address is given to you by your Internet Service Provider (ISP), and while its primary use is very beneficial, there are risks if too many people you don’t trust know your IP address.
Proxy means ”substitute”, and it is used as a substitute IP address for your computer in the case that you can’t access some website on your own, or if you want to keep an anonymous internet identity while browsing websites that you don’t trust with your home IP.
Benefits of Not Being Around
The best comparison, when discussing both risks and benefits of a proxy server, is a remote PO Box where you are receiving all the mail you don’t want to have in your home, and it is usually done for the same purposes.
Most proxy connections are used in countries where the state legislation forbids connections to specific websites and in places like China, where around 29% of the population is using a proxy server or a VPN to connect to the Internet.
While proxy servers are cheaper to use, they come with the risk of people on the proxy server collecting your information and knowing both your IP address and the information you were accessing.
Even with those risks, many are using the opportunity of a proxy connection to see something they would, in different cases, wouldn’t be allowed to see.
Should You Hide Proxy Connections or Make Them?
Creating a proxy connection is, in fact, quite easy. Either when you are trying to make a proxy server or if you are trying to connect to an existing one, both solutions have a wide range of apps that will make this task fast and easy. Many of those apps are built-in into your Operating System (OS).
This large set of additions that make proxy connections easier are mostly focused on business users and larger companies that prefer to have their connection going through a secure server with much stronger protection than would be possible on a regular computer.
Connecting to the Internet through a proxy computer is very similar to when using your modem, but instead of a direct connection, you are using a Local Area Network (LAN) connection through another computer, finally connecting to the Internet through that modem.
For computers using Windows, macOS, or Linux, this is a fairly straightforward task of entering your Internet Options, checking the use proxy server as LAN box, and entering the IP address of the computer you wish to connect to.
For using tablets and phones, it is required to use a third-party app and choose from a list of proxy servers that are set to reroute your connection and mask your original IP.
Once you are connected to a proxy server, that computer receives your requests and sends them to other websites and applications using its IP address.
Obviously, the problem with this is that all of the requests you are making are being recorded by the proxy server, but if you are confident in the privacy of the server, or if you don’t care about that party knowing your browser history through that proxy, this is the easiest way to go.
Different Types of Proxies
There are four types of proxy servers, which all differ by the level of anonymity and by what they are used for. These types include Anonymous Proxy Servers, High Anonymity Proxy Servers, Transparent Proxy Servers, and Reverse Proxy Servers.
Type 1: Anonymous Proxy
The most familiar type of proxy is the Anonymous Proxy that is used to mask the IP address of the original computer.
There is no way for the endpoint computer that is receiving your requests to find out which is your home IP and, if there is a need for even higher security, the connection between you and the proxy server may be encrypted. This is the way that most individual users connect via proxy.
Type 2: HAP
The High Anonymity proxy provides even more anonymity than the regular connection as it doesn’t present itself as a proxy server but as a regular computer creating a one-way request to the Internet.
This way, the endpoint website or application refers to the proxy server as a client and not as a node point, preventing the restrictions that some websites and applications pose on proxy servers.
Type 3: Transparent Proxy
While this is not something that most personal users would even consider a proxy server, a transparent proxy is only used as a go-through server and presents the home IP as the computer making the request.
As there is no anonymity, this type of proxy server is not used for the same purposes as the first two but rather as a resource-sharing computer for some businesses.
This type of proxy is the base for many cloud-based systems, which use multiple proxy computers but are always showing the primary IP address.
Type 4: Reverse Proxy
The last type of proxy server is the reverse proxy, where the goal of the connection is not to shield you from accessing web pages and applications but to prevent others on the Internet from freely accessing your computer.
While this type of proxy has a personal application for people who store sensitive data on their hard drives, the usual application is with larger businesses that have company resources on individual computers.
And, by using a reverse proxy connection, they are preventing third-party connections to those computers, but rather to the server that can be protected with a large number of encryptions, firewalls, and other measures.
Why use a proxy?
Depending on the type of proxy connection, it can be used either by an individual, a small group, or a business. The two main reasons to use a proxy are to mask the requests to the Internet from your IP or to shield from other people on the Internet making requests to your IP directly.
These two categories further have multiple variations on where, how, and why people use a proxy connection.
The two main reasons why personal users connect to the Internet via a proxy connection is to combat two hurdles posed wither by governments, ISPs, or large corporations; such are restrictions and data collection.
Some countries, the most famous example being the People’s Republic of China, restrict access to a wide range of websites and applications, making it impossible for a user with a Chinese IP address (one provided by the Chinese ISP) to see the web content or use the application. See our list of the top 10 countries with the most heavily censored Internet.
This reason is also used for content restricted by the publisher for some reason, where it is banned from certain countries, which often happens with TV shows and online movies that are awaiting official publishing in some regions.
For example, some of the best video streaming services are only available in the US and are restricted to users outside of that region. Read on to find out how to unblock TV shows and online video streaming from anywhere in the world.
Data Collection
Users also use proxy connections when they want to prevent their ISPs, governments, or corporations from collecting data on their browsing habits.
Here, the most popular example is none other than the United States, where ISPs can sell your browsing metadata to both government agencies and retailers, who can then tailor your ads by your browsing history.
The two reasons business users use a proxy connection is either to share resources or to protect information. Using a company server as a proxy usually does both of these tasks in any larger company, and even many smaller ones that do a lot of their business online.
In this case, the main server computer can be set up to protect any incoming requests and also to store information that could then be accessible from all computers inside a network.
There are other reasons why people use a proxy connection, and new uses are made for this option every day, especially when we include the Internet of Things (IoT), but most users cite their reasons in these four groups.
Anonymity
Using a proxy connection can allow for a significant dose of anonymity, but it should be good to know that you are not anonymous from everyone when using it. While your IP address will be masked from the computer you are sending your internet request to, it will be known to the proxy server itself, even when your connection to that server is encrypted.
Anonymity, in the case of proxy connections, is more focused on the automated collection and recognition of data from your computer than the actual anonymity of specific persons that would want to track your movement and browsing.
In this case, your information is only as secure as are the protocols on the proxy server, and for larger servers that do a business of providing easy access to them and their services, the potential from hackers knowing your IP address may be quite high.
In general, you should regard your proxy connection as a way to mask your IP and not any security or anonymity measure, especially if you are a personal user using a proxy server service.
For optimal Internet security and anonymity, you need to use a VPN. Don’t leave your personal information around using a proxy, and always be sure that you have protected your computer with updated security systems.
Free Proxy List: our top list of proxy servers
While the actual number of proxy servers worldwide might be enormous, there is only a limited number of public proxy servers that offer this type of connection reliably and with a quick connection.
You should never use a public proxy service with a low rating (below 70) and should often monitor to see if the server you are using has fallen below that number.
Other factors when using a proxy server is the uptime of the server, as you don’t want to be disconnected from the proxy in the middle of your work, the access time the server is providing to you, as you may need more time to finish all requests, and finally, the country where the server is located as this might influence both the ping time and the restrictions you are trying to surpass.
Here we have listed some of the popular proxy servers worldwide, with their relevant information listed:
| Domain | Rating | Country | Access Time |
Uptime % | |
| ooproxy.pw | 71 | United States | 0.6 | 97 | |
| steadyproxy.ga | 87 | Netherlands | 0.2 | 98 | |
| bananaproxy.eu | 81 | United States | 0.5 | 98 | |
| 789proxy.cf | 98 | France | 0.1 | 98 | |
| franceproxy.pw | 98 | France | 0.1 | 98 | |
| 3proxy.space | 72 | United States | 0.6 | 98 | |
| 678proxy.ml | 73 | United States | 0.6 | 98 | |
| popunderfreeproxy.eu | 80 | United States | 0.7 | 99 | |
| myproxysite.ga | 96 | Netherlands | 0.2 | 98 | |
| 55proxy.pw | 69 | United States | 0.6 | 98 | |
| proxyeuro.pw | 96 | France | 0.1 | 97 | |
| europroxy.pw | 100 | France | 0.1 | 98 | |
| iwaz.gq | 63 | United States | 0.8 | 97 | |
| applepieproxy.xyz | 98 | United States | 0.3 | 100 | |
| kproxy.com | 70 | Canada | 0.6 | 100 | |
| shinyproxy.com | 76 | United States | 0.5 | 97 | |
| proxy.tokyo | 83 | Japan | 2.0 | 100 | |
| steadyproxy.cf | 95 | Netherlands | 0.2 | 100 | |
| youtubeproxy.pw | 62 | United States | 0.9 | 100 | |
| 456proxy.ml | 65 | United States | 0.7 | 96 | |
| tomatoproxy.eu | 77 | United States | 0.6 | 97 | |
| helloproxy.science | 71 | United States | 0.6 | 98 | |
| proxyjapan.nu | 83 | Japan | 2.0 | 100 | |
| 0proxy.space | 66 | United States | 0.6 | 97 | |
| ghostproxy.eu | 81 | United States | 0.6 | 99 | |
| gowebsite.link | 78 | United States | 1.5 | 99 | |
| bvpn.win | 99 | France | 0.1 | 98 | |
| accessproxy.science | 74 | United States | 0.6 | 99 | |
| 8proxy.space | 91 | France | 0.1 | 97 | |
| buqd.xyz | 72 | United States | 0.6 | 98 | |
Risks when using a proxy
When using a public proxy, there are two main risks that you should be aware of, primarily as they are not within your reach, and you will not always know if you are being exposed or not.
The more common risk your computer might be exposed to when using a proxy is spyware that is usually downloaded as free software or pushed through malicious websites.
This is where the quality and protection protocols of your proxy connection server come to show as high-quality, trusted proxy providers will have advanced security protocols that will make any spyware docile, rendering it unusable even if it is installed on your computer.
Those servers that don’t have this kind of security will allow the malware to send your computer information, including your IP, through the server and disclose everything you are trying to hide, rendering the proxy service useless.
Taking Over Your Device
The other risk which is truly beyond your control is the ability of hackers to take over the proxy server and monitor, collect and change any data that comes through these servers.
This means that if you are using a proxy that has a low or unavailable rating, all of the information you are typing might be subject to collection, including your personal information such are your passwords, credit card information, and even your social security number.
A proxy connection should be used only for specific purposes and never as a substitute for regular security protocols when using your computer. While the kinds of server takeovers as mentioned above are rare and usually dealt with quickly, you will not have good oversight.
If for any reason you need to mask your IP address and to have more secure and encrypted protection that will be secured not only from the automatic process but also any person with malicious intent, it is much safer to go with a high-quality, professional, and trusted VPN provider than with a public proxy connection.
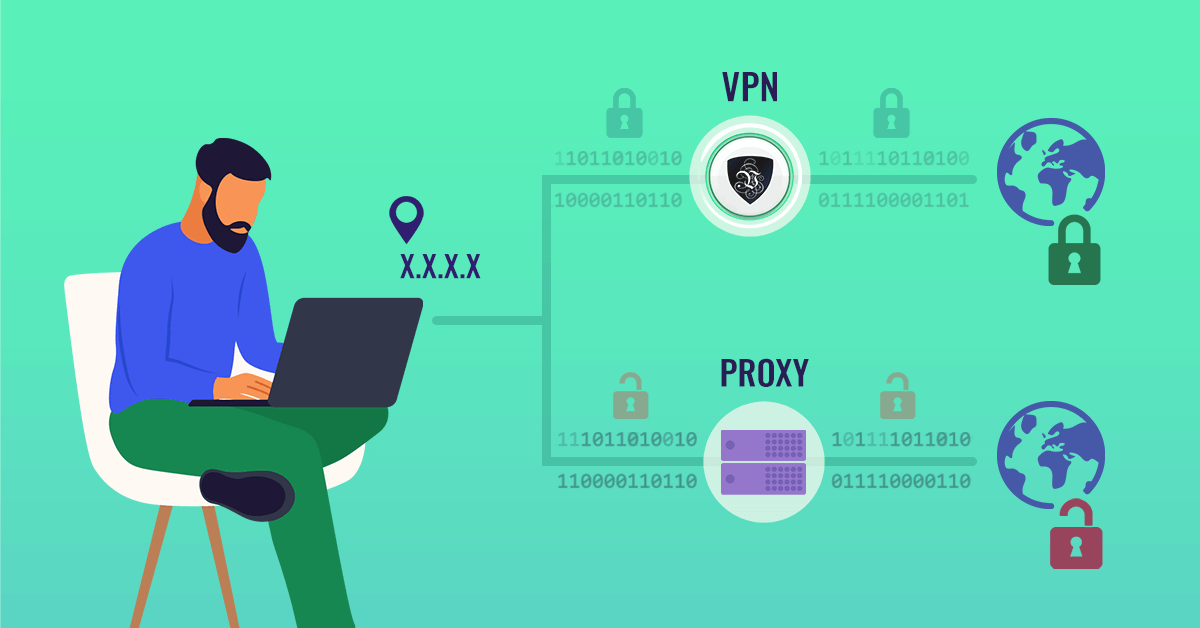
Difference between a Proxy and a VPN
A proxy should be regarded as a forwarding address for your computer. It usually uses only SOCKS and HTTP/HTTPS intermediary, which can be intercepted both by hackers and by malware.
A VPN connection scrambles all information between you and your VPN provider, making it next to impossible for third parties to intercept or see the information that is being transferred.
While a proxy will mask your IP address from the main log of the website or application that you are sending your request to, it will not prevent any application on your computer from sending your IP with its regular data.
This is usually visible when other appliances aside from your computer are connecting to the Internet, like your printer or some other smart device.
A VPN provider will provide you with the best aspects of a high anonymity proxy server, but with the added encryptions and safety protocols. As far as the Internet is concerned, your connection location is whatever the location of the VPN server is, and your security is as tough as is the VPN providers, which is usually quite a lot.
Conclusion
While you don’t need to hide proxy connections always, today, using a VPN is a far superior option. Not only is it safer, but the connections are much faster, and there is always the kill-switch if anything is compromised.
Le VPN is one of the oldest VPN providers on the market, offering custom-made software for Windows, Mac, Android, and iOS, different internet security protocols, high speeds of VPN connection, and a selection of IP addresses in 100+ locations.
SUMMER SALE
First 3 years for $2.22/mo
NO LOGS
100+ LOCATIONS
P2P ALLOWED
Easy To Use
30-Day Money Back
Friendly Support
Bitcoin Accepted
Ultra High Speeds



Written by Vuk Mujović @VukMujovic
Vuk Mujović is the founder of MacTíre Consulting, an analyst, data management expert, and a long-term writer on all things business & tech. He authored blogs, articles, and opinion pieces aimed to help both companies and individuals achieve growth without compromising their security. Vuk is a regular guest author to Le VPN Blog since January 2018, where he gives his expert opinion on the topics related to cybersecurity, privacy, online freedom, and personal data protection. He also often shares his tips and best practices in relation to internet security and digital safety of private individuals and small businesses, including some additional applications of using a VPN service.