Mobile apps make the world a much smaller place, for you and for Internet criminals.
Mobile App Privacy Issues Concern Us All
The joy of mobile is that it’s mobile. The ability to take a device anywhere, just about everywhere, and be able to connect to the World Wide Web offers unparalleled freedom. The advantages are obvious, instantaneous communication globally. You can chat with friends, talk to family, play games online, use social media, conduct business, manage finances, share pictures, control remote devices and on and on. The disadvantages are not so obvious and begin with the connection you make. At home you have the luxury of using a privately owned and set up system with firewalls, anti-virus and anti-malware protection. In the wild, when you are out and about, you are at the mercy of whatever cell tower or Wi-Fi connection is nearby
What Are Mobile Apps Security Issues
What aren’t mobile phone security issues is more like it. Every aspect of your mobile device from its software to the hardware, the phone connection, Internet connection and most importantly the apps you use provide an avenue for security threats. When it comes to apps, the Internet and the Internet connection there are two types of threats: user generated threats and external threats. User generated threats include how you connect, where you connect, what you do when you are connected and ultimately who you connect with. External threats include things like viruses, malware, surveillance, lost data and more.
- According to sources the average smart phone user has 26 apps installed and that virtually all of them have some form of security issue. Apps typically need to use data from your device to function, this means granting them permissions to access it. The biggest problem is that many, if not most apps, are granted permissions they shouldn’t have and putting you at risk. Does a game really need to access your contacts? Or send email?
The connections you make with your mobile devices are almost 100% wireless. It is the rare occasion indeed when a phone or tablet is connected directly to the Internet or even a computer for that matter. Whether it is through the phone towers, Wi-Fi or Bluetooth these connections can be monitored, traced and hacked. They provide a means of entry for viruses, malware and unwanted invasion of your privacy. These connections are not safe for sensitive use of the Internet and are pathways through which hackers, ISPs and governments can monitor you, or invade your device. Since most apps don’t include a security feature, or are not securable, this means that they are accessible to whoever has the savvy to do it.
- Not all Internet connections are the same. In the old days there was only HTTP. This stands for hypertext transfer protocol and is the means by which information, your data, is sent across the Internet. This connection is not secure and completely wide open to intercept, monitoring, tracking, hacking and theft. Now there is a new protocol, HTTPS. This stands for hypertext transfer protocol secured and also known by the names HTTPS.
Where you connect can also play a big role in the security of yourself, your device and your personal data. Cyber cafes, public Wi-Fi connections and other non-secure methods of accessing the Internet are NOT SECURE. These resources, while a boon for society, are often unprotected and a hunting ground for all things bad. Viruses and malware can easily target these connections looking for unprotected devices, hackers can use the connections to access your device, steal your data or worse. Compounding the issue is the apps on your phone. These bits of software often connect to the web when you aren’t aware of it sending all kinds of data about you and your location across the Internet.
What you do when you are connected can mean the difference between years of hassle free Internet use and a lifetime untangling the after effects of identity theft, fraud and other crimes perpetrated over the net. Keeping your traffic restricted to safe sites and only using the most trusted apps means less virus attacks, less malware installed on your computer, less collection of data and less chance of data loss. Some types of sites that might be good to avoid include low profile gambling, get rich quick schemes and certain chat rooms.
- The National Security Institute says that 97% of all apps studied have some sort of privacy issue. In terms of security, 86% lacked even the most basic forms and 75% failed to encrypt collected data. All it takes is one bit of information about you. A black hat can use that bit to mine other databases to build a complete profile. Databases are available across the net via legitimate and not so legitimate sources.
Who you connect with may not seem like such a bid deal until you start reading about all the people who’ve been robbed, stalked, attacked, raped and killed after meeting someone on the Internet or through a social media app. The Internet is a place where anyone can meet anyone at just about any time of the day, and do it in a largely unregulated and unaccountable way.
The rise of social media has only made it easier for criminals to find, target and prey on the innocent. Weak, immature, young and susceptible minds can be easily led astray and that does not take into account the sophistication of today’s Internet crime.
View our list of the most dangerous social media apps that children are using. Trust me when I say you too can be duped into giving money to a fraud.
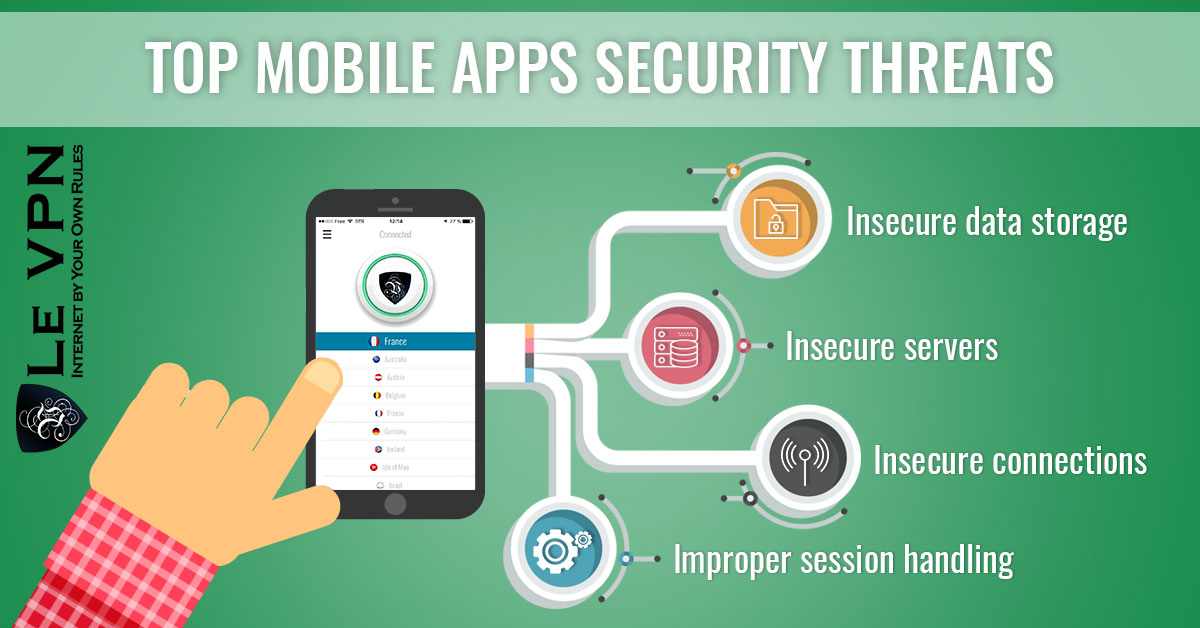
Top Mobile Apps Security Threats
- Insecure data storage.
This includes your personal data as well as authentication tokens, history, passwords, cookies, location data and more.
- Insecure servers.
The servers being used by today’s apps are getting better and better but this does not mean they are being secured properly. Server vulnerabilities allow hackers to access and steal data.
- Insecure connections.
Even if an app is set up to run in https that does not mean it is. All too often these connections will default back to an http connection in order to increase speed/decrease bandwidth. Non-secured connections mean that any data you transmit to, with or through an app is free to be viewed by anyone who would like to.
- Improper session handling.
Proper session handling means you get logged out after so many minutes of inactivity. Bad apps, most of them, will keep you logged in indefinitely, or until you log yourself out.
Social media app privacy is a big concern because we willingly give up so much information when we use them.
Facebook is by far the largest and most pressing security issue for mobile devices because it is the most widely used social media. It also is the largest social media platform with largest number of subsidiary apps and all available at the touch of the icon on your touch screen device. On top of all the apps available through Facebook and all the data it and those apps have been collecting and sharing about you, Facebook is fast becoming the preferred method of signing in to websites. Instead of having to sign up and log in to all those sites you can now let Facebook take care of it for you! And expose you to a whole new avenue of danger. To be clear, Facebook makes no effort to hide its collection of your data, the collection of your data by its subsidiary apps and their sharing it among themselves for the benefit of your “experience” and Facebook’s bottom line.
On the plus side, Facebook also has one of the toughest authentication programs so it is less likely to find predators using it. That being said it is not impossible to find fraud and scams on the platform. One type of fraud centers around binary options. Binary options are a “simplified” way of trading the financial markets, one that is largely unregulated and a favored tool of get-rich-quick scam artists. Targets befriend so-called trading gurus and are enticed to pay for private trade groups to get winning tips and to deposit money with scam brokers so the guru can earn a commission.
- Once you connect an app or a website to your Facebook or other social media – anonymity vanishes.
Google+ is Google’s failed attempt to enter mainstream social media. It is also the 2nd most popular method of signing into apps and websites without having to enter your account details, and a raging collector of data. While we can assume that Google is using state of the art cutting edge security technology it is not infallible and all this app access, data collection and storage is going on in the cloud so is especially vulnerable to loss. What makes Google and Google+ of particular interest is the App Store, a place where you can find an app to do anything and for a low price. Google takes some steps to monitor what’s going on but not nearly enough.
Glow and apps like it are intended to aid women track their health. The app requires you to input far too much personal data, tracks sexual activity and monthly cycles and come with far too few security features. When Glow first came on the market it was a target of a consumer watchdog who found members’ profiles could be accessed with only a few hours effort. Since then, security has been enhanced but vulnerabilities remain. Bottom line, if this site gets hacked or your connection is monitored some very sensitive information is going to be lost.
Novelty apps like Flashlight, Crack the Whip and Air Horn are fun when you first get your smart phone but soon lose their luster. Considering that these apps often have access to your contacts, browsing history, emails and photos you might wonder why they are downloaded in the first place. It’s because most app purchases/downloads are impulsive and the app makers know this. They use these apps to collect data and build databases to sell to the highest bidder.
Consumer loyalty apps are a popular way for merchants to add value for their customers. They are also a means of collecting sensitive data and can put your financial information at risk. Starbucks is one high-profile company busted for storing members bank card information including passwords. If the one of the world’s largest companies isn’t doing a good job with your data what can you expect from everyone else?
Every dating app, ever. Dating apps are one of those things where you have to enter a lot of personal data just to use them. While many of them are legitimately trying to hook you up with the person of your dreams they are all also collecting data and building databases. The worst will compile files and profiles to sell on the open market, the best will merely use it for internal use but in both cases that data is open to theft and loss. A study in the UK found that the top dating apps on the iOS app store were guilty of leaking data including Facebook profiles, photos, location and more.
Every fitness tracking app, ever. At first glance fitness tracking apps are a great thing, and they really are. They help us keep track of what we do and encourage us to be more active and lead healthier lives. To that end it is no surprise to find insurance companies promoting the use of these trackers until you think about this. The apps collect data and insurance companies love data. They use it to fill their actuarial tables in order to compute the best rates, and to compile files about us individually so they can apply those rates to us. At the same time these apps, including the Apple Watch, Fitbit and more, track our location through GPS and employ low level security features.
Pokémon Go. Yes, the world’s most popular game is putting you at risk. The game gets full access to your mobile device and not only tracks your location in real time allows other users to lure you in with the promise of Pokémon riches. Within days of the Pokémon Go app’s launch reports were popping up of misdeeds perpetrated by users abuse of the app.
Your car can put your mobile device at risk, and vice versa. It was found that many apps provided by automakers and the auto-industry have a fatal flaw… they don’t discount automatically when you sell your car. In fact, they don’t really disconnect at all. A study found that used cars, once sold to a 2nd or even 3rd owner, could still be accessed and controlled by the original user’s phone. The problem is that a device reset, of the phone or the car, does little to erase data that is stored offline on the cloud. This problem exists in other areas of the Internet of Things as well and could become a much larger issue in the future.
Smart homes, smart businesses and the Internet of Things at-large is vulnerable to this form of attack. Not only that, they tend to store the original owners data as well making them a potential inroad for abuse in either direction. Considering the value put on data, think about the value put on a decade of life in a smart-home, or years of driving a car that can be directly tied to you, your financial records, your health records and web-browsing history?
The Best Mobile Security App
While a VPN can not prevent you from giving up your valuable information, falling prey to the advances of an Internet predator or keep websites from logging your presence they can keep your privacy safe and your web use anonymous so that no one will know who you are unless you tell them. They do this by cloaking your ID, masking your computers digital markers and making you appear like a ghost drifting through the machine. VPN stands for virtual private network and it is the most advanced form of personal/business security you can use on the Internet.
It is a combination of software you download to your devices, including Android and iOS powered mobile devices, and a network of dedicated VPN servers. Once only available to big business, governments and those with the savvy and money to run a VPN network they are now available commercially. Le VPN just released the latest version of its Android VPN app and iOS VPN app, the most advanced technology available for fighting mobile phone security threats.
VPNs work using a combination of technologies. First, before your data is transmitted from your computer across the Internet it is repackaged into an anonymous form and encrypted so that it cannot be tracked back to your computer. Then the data is transmitted to the VPN server before moving on the Internet. When it does move on to the Internet, it carries a new IP address. This means that your connections are secure and your ID is completely masked so no outside influences can attack or affect your connections and the only websites/apps that will know who you are, are the ones that you tell yourself.
Smart phones and mobile devices are here to stay, that is a fact. This means we’re going to have to keep using apps regardless of their security risks, which leads to the need for VPN. If you are using a smart phone or a mobile device to access the Internet then you need a VPN. Don’t wait until it’s to late, go get Le VPN!
*Article Updated On October 26th, 2018.*
SUMMER SALE
First 3 years for $2.22/mo
NO LOGS
100+ LOCATIONS
P2P ALLOWED
Easy To Use
30-Day Money Back
Friendly Support
Bitcoin Accepted
Ultra High Speeds






Written by Vuk Mujović @VukMujovic
Vuk Mujović is the founder of MacTíre Consulting, an analyst, data management expert, and a long-term writer on all things business & tech. He authored blogs, articles, and opinion pieces aimed to help both companies and individuals achieve growth without compromising their security. Vuk is a regular guest author to Le VPN Blog since January 2018, where he gives his expert opinion on the topics related to cybersecurity, privacy, online freedom, and personal data protection. He also often shares his tips and best practices in relation to internet security and digital safety of private individuals and small businesses, including some additional applications of using a VPN service.
Comments (2)
How is Blender an unsafe app?! It’s basically just a free 3d software that everybody can use!!!
Hello! You’re totally right, we are talking about Blendr, a different app. More in our article here: https://www.le-vpn.com/dangerous-social-media-apps/