How long does data remain on the Internet? The answers, and what you can do about it, may surprise you.
How Long Is Personal Data Stored Online
How long does personal information stay on the Internet, how long can digital data last? These questions get asked everyday by individuals, businesses and organizations. The simple answer is a long time, indefinitely, forever. The reality however is often quite different because there are limitations to data, data storage and retrieval that often give digital information a lifespan. The real problem, when it comes to your data, its collection, storage and use by third parties is the transient nature of information. Data collected and stored in one place may have a lifespan in that specific location but if it is shared, lost or stolen to a new location that lifespan is extended.
- The length of time a bit of information is able to remain online is completely dependent on what it is and where it is being stored. A random bit of data with no lingering value may be erased from a memory and lost from the web very quickly. Intentionally uploaded material to a site such as YouTube, Facebook or other social media may be searchable forever.
Interesting in a philosophical sense the answers to these questions have a far reaching and long-lasting importance to us and to future users of the Internet. The push to online data storage, The Cloud, means that in most cases data you upload, access, store and use will at some point get used by, stored and saved on some third party server. In the future it could mean that no data is stored locally.
The Cloud is one of those things that is tricky to define. While it does include online data storage it also includes just about every other kind of SaaS and PaaS services available across the Internet. Basically a “cloud”, because there are more than one, is a network of servers set up to perform a function. The function is typically running an application or delivering a service across the Internet. Users do no have to download or install any software as all functions are performed by the cloud network. . . which is storing your data and data about you.
- The Cloud is not a thing, it’s a term referencing server based web applications delivered across the Internet, any server network set up in such a way is a “cloud”. The cost of storing data is low compared to it’s worth. So long as data has value it will be collected and stored.
- In December 2010 the Obama administration put forth the Cloud First policy encouraging businesses to take full advantage of cloud computing technology to enhance efficiency and boost output.
Many times you use the cloud without even knowing it, or having to approve it. Think about your phone. I know I never signed up for online photo storage but all my pictures have somehow ended up stored in the cloud. File-sharing services like Google Drive and Dropbox are also good examples. Facebook’s Timeline remembers things you did in the past and remembers them for you, all thanks to the Cloud.
How long can digital data last? Evernote, an online data storage, organization and sharing service guarantees customers 100 years of access to their data. To achieve the claim company execs set up a trust to ensure the operation of storage servers should the company go out of business or be taken over. Of course, this assumes that in 100 years we’ll still be using the same old servers and computers that we do today. The solution to changing technology is of course money. If they can make it financially worthwhile to have the data transferred to whatever the latest technology is, the company will be able to endure.
Telecommunications Data Retention Time Dictated By Law
In some cases data retention time is mandated by law. Australia has passed and enforced a data retention law which requires telcos and ISPs to log and store all users metadata for 2 years. The law, seen as a means of protecting the public, has caused a lot outcry in the country as it is also seen as a gross invasion of privacy. The data is slated for use by law enforcement agencies during investigations and court proceedings and effectively turns the telcos and ISPs into government spies. Digital Rights Watch declared the day the law passed as National Get A VPN Day because VPNs are the only means of ensuring anonymity on the web.
The real problem in Australia is that 2,500 separate offices have access and responsibility to monitor the data which means servers around the country will be sharing and storing it. Information being collected includes name of the account holder, the phone number/IP address, outgoing traffic, dates of calls, recipients and email details. Data miners could use the information to paint a very detailed picture about the specific individual lives of every Australian including their financial status, health and political views.
It may seem unusual to mention telecommunications data retention time in an article about online data storage but let me remind you of something. Today’s computers, computer networking and the Internet are off-shoots of the original telephone systems. Computers were developed to handle the traffic and routing of calls when the system became too complex for human operators to handle. In today’s world we rarely use what are now termed “land-line” phones but nevertheless our mobile, Wi-Fi and computer connections are still routed through the telephone system at some point in their travels. And they’re getting logged at every step of the way.
The legality of has been an issue for many countries. The EU passed a data retention law on the premise of fighting crime but was later declared invalid on the basis of violating basic human rights. The UK passed an amended law in the wake of the EU law’s invalidity but it too is coming under fire for violating human rights. It is labeled the “snooper’s charter” and is said to be an inroad for the government to spy on the populace, or at worst a source of information to be used for fraudulent and illegal purposes.
The US has failed to implement mandatory retention laws on ISPs and telecom companies but many private and commercial organizations actively collect data that can be coerced by the government. The FBI is able to secure data with a National Security Letter which in effect is a secret warrant issued without judicial oversight. The argument is that the data can be used to combat crimes and terrorism but it comes at the cost of privacy, civil liberty and basic human rights.
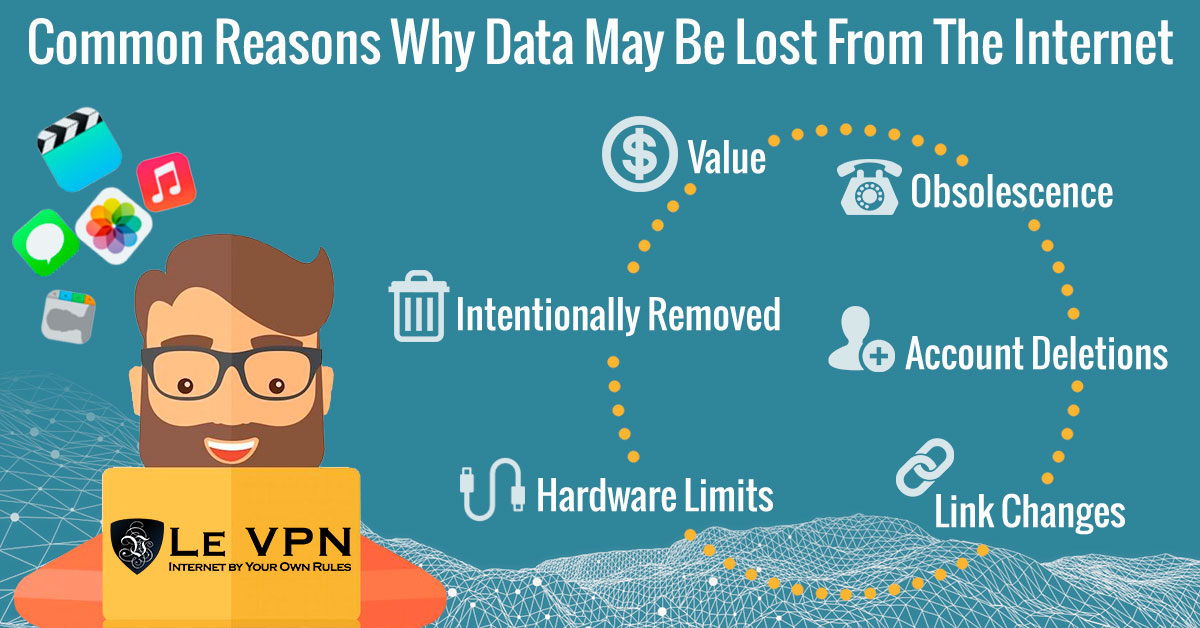
Some Common Reasons Why Data May Be Lost From The Internet
There are lots of reasons why data may be lost from the Internet. Here are a few of the limitations of online data storage.
- Hardware limits
As powerful as today’s computers are there are still limits to what they can do. Storage servers have capacity limits that may be reached triggering loss of older or less used information. They may also suffer power failure or reach the limit of their ability to function properly resulting in loss of data.
- Value
Data is stored because it has value. For the user stored data can include passwords, account information, health records, loans, financial information and other personally important and therefore valuable information. Businesses may store their records and information on the cloud. When the data loses value it is can be purged.
- Obsolescence
If data becomes obsolete or if its location, form of storage or supporting organization cease to be necessary the entire set can be lost forever. The risk for future generations, like most of us with closets full of CDs, is that we’ll move on to a new form of digital data storage and information stored by today’s methods will be lost.
- Account Deletions
A lot of data that is stored online is tied to an account. If you go looking for an article or picture and can’t find it, there’s a good chance the account was closed. This could have been done intentionally but is usually due to suspension for improper use.
- Intentionally Removed
Often times content is removed from the Internet intentionally and if it isn’t stored somewhere else it too is lost forever. The flip side of this problem is when you want to remove content. If it has gone viral or been disseminated in any way it may be hard to find all traces of the content.
- Link Changes
Sometimes content is lost because links change. If a link is changed and not fixed the location of the content may be hard or impossible to find and effectively lost to the Internet.
How Long Is Data Kept Online?
If you are asking yourself that question because you are worried about something you posted in the past rest assured it is likely still there. Think Before You Post remains the number one bit of advice for Internet users, keep your personal life private and you won’t have these headaches. That being said it may take a lot of work to remove all traces of an old life. Some professions teach their students not to post detailed information to social media for a reason, they can be stalked, and it is something that all students need to learn, and at an early age.
To attempt to go back and try to erase all evidence of past indiscretion is a monumental task and likely not every truly complete. Sure, you can delete a post from Facebook or Instagram but can you delete every trace of every person who ever liked, saved or shared it? When it comes to deleting information you have to contact every website owner who may have some and ask them to delete, and trust that they will get it all. The problem is that there is no way to know all the servers where your data may be stored, or all the things that are known about you on the Internet in order to track them down and “erase” yourself from the web.
Advantages And Disadvantages Of Online Data Storage
Online data storage is a problem for the businesses and organizations who collect the data as it is for those whose data is collected. Once you begin collecting and storing data you must begin to take into consideration legal and business requirements with ethics, privacy and economic effect. Data retention and data retention policy are becoming buzzwords in the corporate world as managers hash out policy dictating need-to-know basis, retention times, archiving rules, storage formats, encryption and access. The goal of data retention is to uphold all legal, privacy and ethical concerns while preserving and organizing useful and necessary information for future use.
A crucial portion of any data retention policy is a protocol for “permanent deletion”. We all know that deleted content is never really deleted unless it is erased from the hard drive it is located on. A simple deletion may erase the pathway to where data is stored and free up space for new data but does not necessarily mean the data is lost. Savvy computer technicians can easily bypass operating systems and locate data stored on the drives so long as there has been no physical damage. A “permanent deletion” protocol may require that data be stored in an encrypted form. Thus, when deleted the file may be found but without the encryption key will never be opened. To further enhance this protocol the encryption keys should also be deleted to ensure the original and any errant copies will never be accessed again.
There are also physical limitations online data storage. Servers age and degrade and will need to be replaced. The huge server farms that drive the cloud generate a lot of heat and need massive fans and cooling systems for them to operate. Humidity is another problem, it can accelerate the oxidation process and speed up chemical degradation of the hardware as well as the digitally stored data which is nothing more than super-complex strings of magnetic 1’s and 0’s. These things require lots of labor as well as space and money.
An Argument And An Answer
Among the many arguments against mass retention of public data by telcos, ISPs and governments is that it is all too easy for terrorists and criminals to hide themselves while on the Internet, making the practice ineffective. Among the many tools a person can use to hide themselves on the Internet are cyber cafes, P2P file sharing services, the TOR network, digital dead-drops and anonymous proxies. The irony is that many of the solutions used by criminals are the same ones used by big businesses and governments to secure their connections, and the answer for individuals concerned with leaving digital traces of themselves across the web.
One of the most effective means of protecting your information and information about you from being collected and stored by third-party websites, individuals and organizations is a VPN. VPN, virtual private network, is a complex protocol of security features developed along side the creation of the Internet as we know it today. They combine IP masking technology with encryption to create secure connections that are hard to find, hard to hack and impossible to read. Originally available only to those with the money, resources or knowledge to deploy VPNs are now like everything else on the net, point-and-click and available commercially through a subscription service.
The average unsecured computer is broadcasting its IP address and the IP address of its router to the ISP servers and network servers around the Internet. This broadcast shines like a beacon for anyone with savvy enough to monitor Internet traffic and believe me it’s not that hard. This means that anyone from the ISP service on out can watch you, track you, record and save data about you and even follow you back to your home, figuratively and literally. The VPN solves all that.
VPNs digitally repackage your data and connection requests and send them to dedicated servers. This does two things. First it masks your original IP address with a new one that is assigned by the VPN server and anonymous. Second it bypasses your ISP’s servers by connecting directly with the dedicated VPN server, effectively hiding you from prying eyes. Now all connections are anonymous and hidden, with the extra-added benefit of encryption with certain protocols. This means that only websites you connect with will know you are on the net, they won’t know who you are and the only sensitive information they can collect is what you give to them directly.
Le VPN is the leading provider of VPN technology for consumers and small businesses. Unlike the free VPNs which collect, store and deal in as much data as any other website Le VPN’s paid service is guaranteed to provide the highest level of anonymity, security and safety as can be had while using the Internet. The service is remarkably inexpensive for what you get, less than $5 per month with 12 month contract gets access to 4 protocols and servers in more than 100+ locations. While VPN can’t do anything about data already stored it can drastically cut down on newly collected data and do it while enhancing your Internet security. Don’t wait until it’s too late to do anything about. Be careful what you post and where you post it and cover your digital tracks with Le VPN.
*Article Updated On September 26th, 2018.*
SUMMER SALE
First 3 years for $2.22/mo
NO LOGS
100+ LOCATIONS
P2P ALLOWED
Easy To Use
30-Day Money Back
Friendly Support
Bitcoin Accepted
Ultra High Speeds






Written by Vuk Mujović @VukMujovic
Vuk Mujović is the founder of MacTíre Consulting, an analyst, data management expert, and a long-term writer on all things business & tech. He authored blogs, articles, and opinion pieces aimed to help both companies and individuals achieve growth without compromising their security. Vuk is a regular guest author to Le VPN Blog since January 2018, where he gives his expert opinion on the topics related to cybersecurity, privacy, online freedom, and personal data protection. He also often shares his tips and best practices in relation to internet security and digital safety of private individuals and small businesses, including some additional applications of using a VPN service.
Comments (2)
generally Dynamic I.P. address is assigned to common people like me.
Do ISPs store who was using what IP address at a particular time?
Hi Himhar, thank you for reading our blog! You may find your answer here > https://www.le-vpn.com/ip-address-tracker/