The history of the Internet is a long list of solutions and problems created by those solutions. So while we know when the technology that created the net was developed, we need to know these issues before we can decide when did the internet start for real.
Internet security is one of the main metrics on how we can measure the development of the world web. On the one side, we want to communicate and share. On the other, we don’t want to be harassed or hacked or our private information to be stolen.
When it comes to cybersecurity, there are three measures that we need to take to decide what is needed and when:
- Protection against digital theft
- Private information protection
- Denial of access attacks
Depending on what you do, you would need different things. Private users are usually not concerned with DDoS attacks on their own devices. But, we are concerned with protecting private information.
At the moment when did the internet start, such protection needed to be done basically manually. Now, we have premium VPN providers like Le VPN that offer protection on multiple devices in real-time with just an app.
Thankfully, those responsible for the Internet, such as Vinton Vint Cerf, are still around to see how their solutions got even better solutions in time.
The History of Internet Security
The origin of Internet privacy issues dates to before the Internet was even launched. Nevertheless, the Internet, a protocol for addressing device locations and their connections over a public communications line, is the number one threat humankind has ever faced to personal privacy.
It facilitates communication and the exchange of information in a way that puts that information, the connections over which it is communicated, and the parties involved at risk of theft, damage, and worse.
When you enter it, connect to it, you send ripples across that alert others to your presence. Unfortunately, because the net is part of the public domain, anyone can use it for any purpose they wish, and in all too many cases, this means no good.
To fully appreciate the Internet and the risks it poses to your safety, let’s talk a bit about its origin and what it was meant to do. First, the Internet is not a physical thing.
Yes, it encompasses our computers, devices, servers, routers, and other network infrastructure but these things all existed before the Internet came into being. The Internet is how computers and computer networks find and talk to each other.
Before the Internet, there were computer networks run by the government, the military, private corporations, and any other organization with the resources to run one.
When did the Internet Start to Have Privacy Issues?
To access one of those early networks, you had to either be logged into a device on the network or gain access remotely through a modem. Of course, in those days, this wasn’t like it is today, where you just enter a web address in your browser and get taken there automatically.
No, in those days, users would have to dial each network directly from their phone, wait for the confirming squeal of the connection, and then access it slowly. And if they wanted to go to a different network, the process would have to be repeated each time.
The TCP/IP solved problems faced by early computer network users. It provided the means by which computers could identify each other and how to find each other. This is done through IP (Internet Protocol) addresses, one of which is assigned to each device on the web.
To find other devices, the IP addresses have to be visible for others to see, which raises one of the very first privacy issues: how can you stay private if everyone can see who and where you are?
Convenience vs. Risk
Because this was such a big issue, lots of people were working on it. But, at heart, there were two issues. The first is that IP addresses are visible, which makes connections visible, traceable, and hackable.
The second is that the data itself was at risk; even if connections could be secured, there is still a risk of loss. The final solution is a combination of fixes from the private sector, and government sources called a virtual private network. A virtual private network, VPN, is a means of securing Internet connections when using a public network that solves both issues.
The first, visibility, was solved with the Tunneling Protocol. This protocol is a means of forming connections that mask IP addresses and bypasses local ISP servers in favor of dedicated VPN servers.
The VPN servers were run by whichever local network operator had the resources to set one up. The second problem, data integrity, was solved with encryption. All data that is transmitted across enabled VPN networks is encrypted so that if intercepted, it won’t be usable.
Needless to say, the average Internet user did not have access to a VPN in the early days of the web. These left them open to many forms of fraud and sparked the industry that we know today as Internet Security.
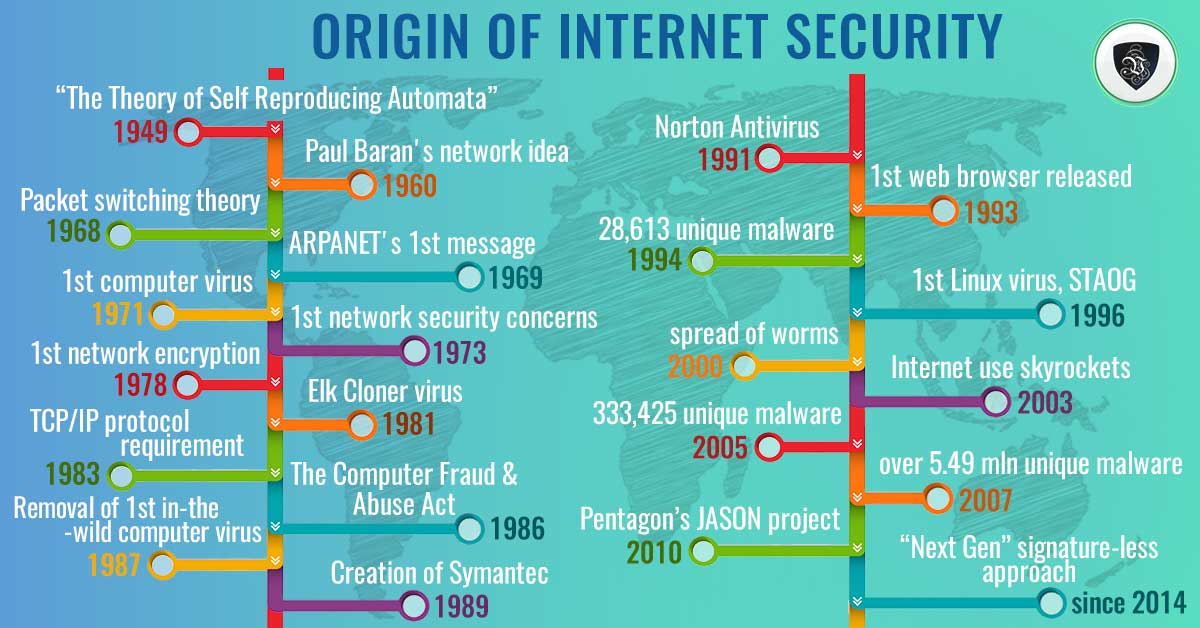
Origin Of Internet Security – A Timeline
1949
Hungarian scientist Jon von Neumann publishes “The Theory of Self Reproducing Automata,” the first foray into the world of computer network viruses. His work is later used by others to develop self-replicating software.
1960
Engineer Paul Baran has a new idea. He argues that a communications network could be set up so that multiple pathways could lead to the same destination instead of having direct connections as were in place at the time.
This solution would allow communication networks to operate even in the event a portion or portions of the network were damaged or destroyed.
1968
Packet switching theory comes into existence. It is a cornerstone of the modern Internet function. Donald Davies, a researcher with Britain’s National Physical Laboratory, argues that data can be chopped up into smaller pieces to make transmission easier.
One of the benefits of packet switching is that multiple users can access the same line making more efficient use of available resources.
1969
ARPANET sends its first message. ARPANET is one of the first packet switching networks and was developed under the auspices of the US Government. It is considered to be the first precursor to today’s Internet and a fundamental stepping stone of Internet theory.
1971
The first computer virus appears. It is called the Creeper Virus and infected the network of Digital Equipment Corporations PDP mainframes. Subsequently, the first antivirus was created to delete it from the system.
It was called the Reaper and was itself a virus targeted at sweeping Creeper out of the system. This marked the beginning of the history of cybercrime.
1973
Network security is already under fire. Robert Metcalfe, an engineer, working on ARPANET who founded 3Com, warns the group the network is too easy to access from outside.
He describes several known intrusions, one of which is attributed to high school students. However, in general, there was little attention paid to cyber security during the ’70s as Internet use and threats was minimal.
The most notable cases involve telecommunications fraud, phreaking, and other attempts at circumventing phone network protocols.
1978
Computer scientists attempt to incorporate encryption into the TCP/IP protocol suite but face many hurdles. One of which is the National Security Agency. The attempt was eventually given up. In hindsight, this is a key fork that could have altered the course of Internet security.
1981
The Elk Cloner virus appears. This is the first virus since the Creeper to appear in the wild. It attacked Apple II computers and was spread by floppy disks. The virus was created by Rich Skrenta, a 15-year-old high school student, as a joke.
The first viruses were aimed primarily at replicating themselves and did not have targeted attacks built-in. Later, as more and more programmers become knowledgeable, viruses evolve to include all manner of destructive code, including the manipulation, theft, or destruction of data, software, or hardware.
Originally transferred by floppy disk, they eventually began to spread through email and across the Internet. The first antivirus were simple fixes to a problem; if a virus arose, someone created a fix. Then, if you got infected, you could buy, borrow or download the fix.
Later companies arose whose purpose was fighting viruses. As the number and types of cyber attacks grew, the services offered by antivirus companies grew to encompass “cyber security.”
1983
in 1983 the ARPANET required its users to communicate using the TCP/IP protocol. This standardized how networks communicated with each other and precipitated the rise of the World Wide Web.
While this was going on, Fred Cohen coins the word computer virus in one of the first-ever published academic papers on the subject. He uses the word to describe software that can alter another computer device with a copy and possibly evolved version of itself.
This definition is later modified by Péter Ször to “a code that recursively copies a possibly evolved version of itself.”
1986
As the Internet becomes widespread, its use begins to grow. As a result, the first computer clubs begin to pop up. These clubs are groups of like-minded computer enthusiasts with varying degrees of organization.
Some are nefarious and begin working on the first viruses as well as other forms of cyber attack. The first virus is called “Brain” and was released this year. The brain is the first IBM compatible virus to occur in the wild and the precursor to the exponential growth of virus and malware applications.
The Computer Fraud And Abuse Act was passed by Congress. This act is intended to curb data theft, unauthorized network access, and other computer-related crimes.
1987
This is an important year for cyber security. First, the first documented case of the removal of an in-the-wild computer virus is performed by Bernd Fix. Fix was a member of the Chaos Computer Club in Hamburg, Germany, and now a leading expert in digital security. Second, Andreas Lűning and Kai Figge launch G Data Software and market their first antivirus for the Atari platform.
Third, The Ultimate Virus Killer is released and becomes the standard in antivirus. Fourth, John McAfee forms the first antivirus company in the US, later bought and incorporated in Intel Security. Fifth, in Czechoslovakia, the NOD antivirus is developed. Last, towards the end of the year, the first heuristic antivirus is released, Flushpot and Anti4Us.
- In computer science, heuristic applications sacrifice accuracy and precision for speed and can be considered a shortcut to traditional methods.
1988/1989
The proliferation of antivirus companies continues. In addition, an email/chat group is started where new viruses and the possibilities for stopping them are discussed. Members include many of the top names in cyber security.
Symantec was launched in 1989. The 2.0 version, released in 1990, included the ability to update protection for newly discovered viruses not present at the time the software was written.
1991
Symantec releases the first version of Norton Antivirus. The European Institute for Antivirus Research is founded. F-Secure lays claims to be the first antivirus company to be established on the web.
1993
The 1990s saw the birth of the modern cyber security industry as Internet use becomes mainstream. This is the year the first web browser is released, which, along with web portals like AOL, made it easy for users to surf and be targeted for fraud.
Labeled Mosaic allows unskilled users to surf the World Wide Web with ease but was also susceptible to many forms of attack. Its release leads to the geometric growth of the Internet and the first attempts to commercialize it.
As the number of users grows, so does the number of online and digital threats. This is also the time we see the first web robots and the distributed denial of service attacks that they facilitate.
1994
AV-Test says there are 28,613 unique malware samples in their database. They’ve been collecting all known viruses for many years.
1996
The web gets sophisticated. A browser add-on like Flash expands on the ability of web browsers. These add-ons fuel animation, music, and many other features that enhance user experiences.
The downside is that they are also rife with flaws, bugs, and vulnerabilities that further degrade Internet security. As a result, experts recommend internet users not to use them.
Phishing also becomes a problem. Email allows anyone with an address to receive targeted correspondence aimed at stealing personal information and/or distributing malware and viruses. The first Linux virus, STAOG, is discovered.
2000
Got Worm? By this time, the spread of worms has become an epidemic. ILOVEYOU is only one of the thousands that exploited security flaws in major software and security practices of the time. If you haven’t had a worm by now, you are not likely using the Internet much.
In this decade, we also see the rise of major Internet crime. Cybercriminals or hackers have become sophisticated and have learned to hide their digital tracks. Adware and spyware become the tools of choice as it becomes clear that data, and in particular actionable data, is worth billions.
2003
Internet use skyrockets. The amount of data created on, with, or by the Internet in 2003 was more than all the data created in human history up to that point.
Internet use has become so entrenched it has begun to alter the face of commerce, business, communication, and the very basics of human interaction. As more users flock to the net, it attracts more crime.
Aggressively self-propagating malware spread from machine to machine, phishing attacks become mainstream, and the net’s worst threat, zero-day attacks, come onto the scene.
- A zero-day attack is an attack from a new source that goes unreported. These attacks are known hazards that are left free to damage Internet users up to and until their presence becomes widely known. Businesses and organizations that do not immediately report these threats are complicit in their spread.
AV-Test reports the number of unique malware has risen to 333,425, an 1100% increase over the course of 10 years.
2007
AV-Test reports the number of unique malware has risen to over 5.49 million for that year alone. In 2012 and 2013, malware firms reported there was 300,000 to 500,000 new malware detected EACH DAY.
Cloud-based antivirus scanning is created, leading to the next generation of cyber security products.
2010
A group of scientists working as part of the Pentagon’s JASON project concludes that the Internet is complex far beyond modern understanding. In their report, they state that many of the Internet’s behaviors cannot be explained well and went on to explain that to achieve major cybersecurity breakthroughs, a more fundamental understanding of the science behind cybersecurity was needed.
The Present
Since about 2014, the “Next Gen” approach has been to use a signature-less approach to help mitigate the zero-day risk as well as know malware attacks. There have been many methods, one of which is the white-label approach.
White label antivirus will only allow software from known trusted sources, so all others are blocked.
Also, with much of the computer networks are now actually mobile Internet and wireless Internet, there is a strong push to repeat all of the solutions that happened with PCs on our handheld devices.
How Has Internet Security Changed
Security has changed in many ways. The most noticeable is that cyber security and anti-malware companies have switched from reacting to threats and attacks to working out ways to prevent them from ever happening.
The sad truth is that a VPN can solve many of the problems cyber security companies are trying to fix. This is because the VPN connects to a secure network; you only connect to the trusted websites you know and love; no one else can see you, so they can’t attack you.
If only you could get one as a retail customer and not have to build and maintain a complicated network on your own…. wait, you can.
Conclusion
Real-time internet protection is easier than ever. With good online apps, you can connect to a secure network and prevent both websites and browsers like Internet Explorer (Edge) and Chrome from seeing what you are doing.
VPN services have become commercially available in the last decade and are the greatest asset to Internet security no one is talking about. Services like Le VPN cost only a few dollars per month, provide unlimited access to the Internet and protect your connections, data, and families with the same security the government uses to protect their connections.
SUMMER SALE
First 3 years for $2.22/mo
NO LOGS
100+ LOCATIONS
P2P ALLOWED
Easy To Use
30-Day Money Back
Friendly Support
Bitcoin Accepted
Ultra High Speeds



Written by Vuk Mujović @VukMujovic
Vuk Mujović is the founder of MacTíre Consulting, an analyst, data management expert, and a long-term writer on all things business & tech. He authored blogs, articles, and opinion pieces aimed to help both companies and individuals achieve growth without compromising their security. Vuk is a regular guest author to Le VPN Blog since January 2018, where he gives his expert opinion on the topics related to cybersecurity, privacy, online freedom, and personal data protection. He also often shares his tips and best practices in relation to internet security and digital safety of private individuals and small businesses, including some additional applications of using a VPN service.
Comments (1)
Just want to say your article is as amazing.
The clarity iin your submit is simply great and that i
could tink you are knowledgeable oon this subject. Fine along wijth your permission let me to take hold of
your RSS feed too stay up to date with coming near near post.
Thank you one million and please keep up the enjoyable work.