“Just because you’re paranoid
doesn’t mean they aren’t after you.”
― Joseph Heller, Catch-22
Even though most of us would consider out internet browsing as very mundane and don’t plan on researching WMDs or global terrorism for your next work project, that doesn’t mean that governments, corporations and malicious individuals aren’t interested in what you like to look at online. It is calculated that Google earns around ₵7 per user of their search engine per day, averaging to $6.7 quarterly, by selling your search data to other corporations. This information is then used to tailor the ads that you see and to push products that you may want or are just susceptible to, as we all are.
And in fact, corporations are the most benign of the people who might misuse your data once they know where you are. If you are a victim of malicious software or individuals, they might, through your IP address, find out your name and other information, leading to identity theft and account takeovers.
What is TOR?
The Onion Router, from which the acronym TOR comes from, was primarily developed for the use by the US military, predominantly Navy, as to mask their IP addresses which could lead to theft of sensitive data while gathering information on missions. Once the military passed to in-house high anonymity VPN systems, TOR was released as an open source free software, that is completely legal to use and possible to download from the TOR website.
So what is TOR? TOR is a multi-proxy network that doesn’t rely on specific proxy servers to process your data but uses the connections of multiple other TOR users to mask the IP of the original user. While this arrangement has the same risks of all other proxy connections, this risk is somewhat mitigated by the fact that there are over 3 million users sharing their IP addresses worldwide, making the exact pinpoint of the original internet request next to impossible.
The TOR Browser, that is the program used to access the internet over the TOR network, is relatively easy to install, and the program itself is coded in C, Python, and Rust. It works on all the major operating systems such are Windows, Linux, macOS, and Android.
How is TOR Used?
Now that you know what is TOR, let see why use TOR. The main use of TOR Browser is to mask the users IP. Similar to a proxy connection, this main function is used to either hide your browsing from malicious software, persons or governments infringing on your freedom, but also as a way to surpass the restrictions some companies put on their services based on their location such are for example HULU and Netflix, as well as other streaming services.
As of 2015, TOR project has also released the TOR messenger which is based on the Instantbird platform and will allow users to use encrypted communication which also masks their IP.
Even though all types of uses are available to all users, most people who have TOR are connecting through it as to mask their IP address, and because they have concerns with connecting over stationary proxy providers. While in more democratic and liberty-focused countries this is sometimes used for malicious purposes, in most places in the world it is used to surpass any chokehold on the flow of information between the user and the rest of the internet.
In many countries, like the People’s Republic of China, where the government closely monitors what people on the internet look at and restricts the ways users can utilize the internet this service can be of prime importance, as different aspects of the society can communicate, share and develop ideas that would be seen as unwanted by some parts of the official administration. It is wrong to think that this includes only political and partisan questions, as most users in the countries which impose restrictions mostly access the internet to look at YouTube, Wikipedia, Facebook or websites with adult content which are in some countries prohibited by the law.
The second most cited reason for using TOR is to prevent governments and corporations to collect metadata, and sometimes actual data, on their browsing habits and accessed websites. This reason is cited almost equally in all countries worldwide.
Repercussions of the government, Internet Service Providers (ISPs), search engines and other corporations and companies collecting the data on your browsing can vary greatly depending on who and what is being collected. The most common result for most users is the sale of their browsing data to market companies who further use that information to tailor the ads for specific persons and can become very aggressive in their promotion if they believe that you might be their perfect customer. The other, the much more severe problem is when governments, especially in the US, restrict passenger access to airplanes and airports to certain people because of their browsing. Sometimes there is even police involvement by investigating persons who were flagged by the system as possibly problematic.
This doesn’t sound as bad until you know that you might be flagged because you were feeding your fear of flying by researching how planes fall down, or were thinking of upping your agricultural production by researching fertilizer and bio-fuel.
Lastly, most of us use the internet in the ways that we would rather not disclose to the public in full, and thus we are wary of malicious persons, hackers, and identity thieves, having insight in our IP address and our browsing habits.
How does TOR Work?
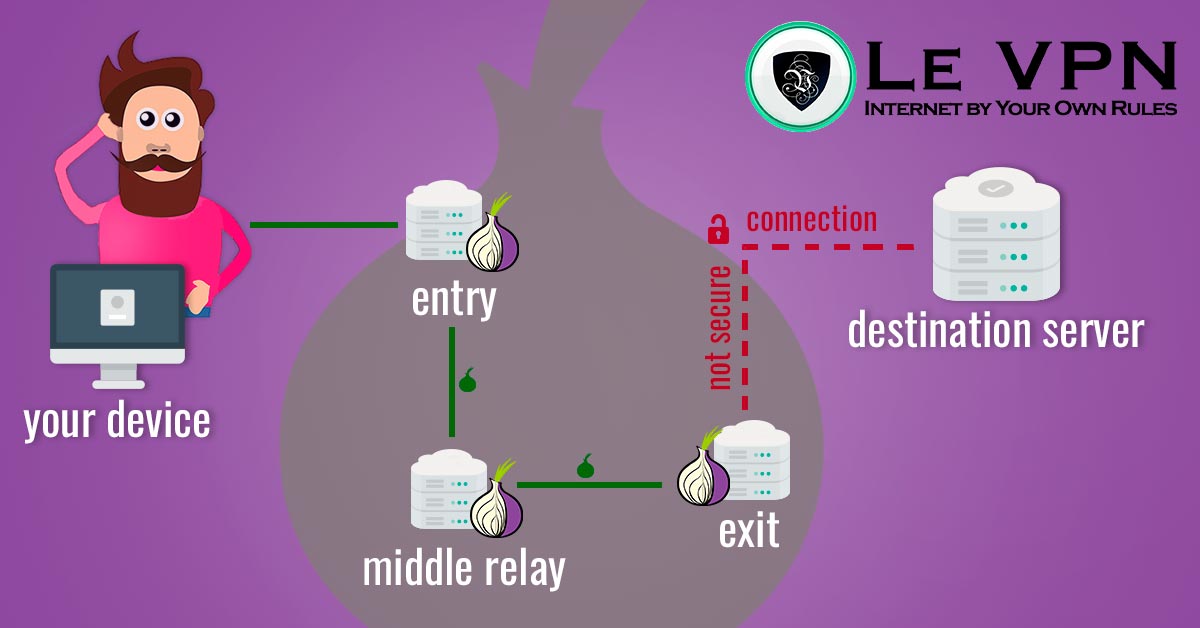
There are three main parts of the whole process behind the TOR project itself that can be viewed as separate steps between you and the data you are wanting to access with your IP address masked, those being you as user, the user network, and the request complier which is the website, server or user you are receiving the information from. The biggest part of the idea of TOR is that any user can be any of those steps, depending on the circumstance, making it impossible to pinpoint where the information is going and from whom if you are on the outside.
You as User
The main part of the interface of TOR is the TOR Browser, previously known as TBB or TOR Browser Bundle, which consists of a modified Mozilla Firefox ESR browser, TOR Launcher, the TOR Button, NoScript, HTTPS EFE and the TOR proxy. This is the whole program that installs all the parts beneath the browser automatically. Once you send your request, TOR browser will encrypt it and send it through
Especially when we know for what uses TOR Browser is used for, the unique feature that TOR has is that it can be installed and run from a removable drive, as it doesn’t interact with the system files of the computer. This is a very welcomed feature as it disables the possibility that someone can infect your copy of TOR browser and thus be able to find your exact browsing data no matter the IP address you are using.
After you close the TOR Browser, all of the data, cookies, and history is deleted from both your device and the network, leaving no traces of which IP address was accessing which information.
While you are browsing, you are not only a user but also a proxy for other people, who are using your IP address as a network node to mask their IP address. In this way, all the users are simultaneously contributing to the anonymity and security of the network. Even though this fact that TOR uses your computer as a proxy is one of the biggest risk factors of the project, the fact that all of the information requested by other users is both encrypted and fragmented makes the TOR browser capable of fulfilling its primary role of masking your IP.
The User Network
The TOR project doesn’t use any dedicated server and all the traffic that is conducted goes through its users, now numbering well over 3 million online at any given time, with that number sometimes passing 4 million. This is a very ingenious system as it removes the main weak points of a proxy connection and relies only on Peer-to-Peer (P2P) connections to mask the IP addresses.
It is also good to point out that TOR doesn’t actually hide your IP address from the internet or negates the connection that you have with your ISP, but rather creates a flooding effect where people who are on any point in the connection can’t be certain about the origin of the IP address that they are getting the request.
Once you send your request to the webpage or other service or application online, it will first bounce through several random connections worldwide before reaching the destination. In this case, even if the destination has any proxy scanning software, it will only find one of the computers in the network, which wouldn’t even have the connection logged, making the search for your personal data futile.
The Request Complier
This is the computer that has the information that you want to see and after it receives the request that originated from your computer sends it back through the last user that was online, again randomly jumping through TOR users, finally reaching you at your browser.
This way it is impossible to ping back all the IP addressed back to you, preventing some more tech-savvy companies from finding your address even through a proxy. In this way, TOR acts more like a VPN service that entirely shields the user from scanning software.
Legislation of TOR project
The TOR project, as well as all of its assisting software, could be best described as not illegal, as there is no legislation that explicitly forbids the use of this software or this type of software in the world. This may be because this is still a new technology from the perspective of any legislator, but even if we were to imagine why would TOR be banned there is nothing explicitly illegal in the software itself.
This being said, most governments, and especially those who have made a habit of restricting the communication between their citizens, have come up with some measures as to prevent people from using TOR.
As the program only masks the identity of the user but not the fact that they are using the TOR browser, some servers and ISPs have blocked those using TOR from accessing any of the information they may be storing. This prevents anyone with a TOR browser to request any data through that specific ISP.
Similarly, some companies deny access to anyone reaching them through TOR and prevent the use of their services with this browser.
All of these obstacles may be circumvented with adequate IT skills, but for most users that will be beyond their level of expertise.
Risks of using TOR
The whole TOR project has identified two weak points in the whole of their functions, primary being the network of users itself, as this makes the entrance to any attack quite obvious, and the other being the fact that TOR is an open source program, meaning that its source code is available to anyone wishing to see it.
There are several ways hackers have exploited these weaknesses in the past, with only some being patched completely and other only being mended for the time being. Most of these types of attack require considerable resources and are available only to larger corporations and organized groups of hackers.
When attacking, the attacker can either focus on some node (the user who is neither a primary nor the final destination of the data) or a group of nodes as to prevent them from processing any other requests but the ones they themselves are sending. Once blocked, the user stars showing their own browsing data as the program can’t process any more request but the ones being directly targeted through that node.
The other popular way of attacking the network is by infiltrating it and leaving malicious software embedded in some type of media that is used to hash out all the IP addresses it goes through, sending the information back, slowly mapping the pathways and the end users. This is basically a virus, made to spy only on your IP address and to send that information back to whoever made it.
One of the more comforting aspects of these risks is that most of them are found and mended by the community working on the TOR project itself, or on some of the third-party applications. This is the case with both of the previously mentioned attack types, as well as some quite ingenious ones, like mouseprint tracking; the idea that mouse movements on the screen recorded by JavaScript would be unique for every individual user. This was uncovered in March of 2016 by a researcher in Barcelona.
Improved Security
Because of the constant attacks, and probably even more because of the paranoid mindset of some TOR users, there have been evermore advanced updates to the program, its stability and its safety.
This is why even after the US government declared that 80% of TOR users will be de-anonymized swiftly at the beginning of 2013 after someone hacked the computer of then Secretary of State, Hillary Clinton. Even though, as most of us can imagine, the US government has a lot of resources at their disposal, no significant number of TOR users have been de-anonymized to this day.
If used correctly, the possibility of detection while using TOR is very low, but there are two ways the authorities try to find out who are the people using it. First of all, there are a lot of TOR opponents running poisonous nods that are made to damage the network around them and catch those not using all the safeguards of TOR to decrypt their information.
The last, and probably most successful way for anyone to find out your information is the most mundane and most pedestrian one: just asking.
In most cases when the authorities were trying to find personal information about an anonymous suspect, they have used chats and forums to ask the person about their information which they gave them, in plain text, directly, their name and the place where they live. While some people think that this could never happen to them, sometimes the person on the other side can be quite convincing, pretending to be something they are not, knowing all the jargon and topics, but in the end being malicious towards your personal data.
Choosing between TOR, Proxy, and a VPN?
There are visible differences between these three types of services. Roughly, they could be rated from the most basic, that being the proxy server connection, to the most advanced being the VPN provider. TOR is somewhere in the middle, providing much more privacy than a regular proxy connection for free, but requiring some technical knowledge to be used correctly.
As a recommendation, all users on the internet should use some kind of proxy at all times, provided that they trust the server if nothing as to be protected from ads and to have another layer of protection for their computer.
Those slightly more tech-savvy should try out the TOR browser as a free and interesting alternative, which is much safer and protects your anonymity much better.
Finally, all those who have a need for true anonymity who will be protected and monitored through a secured system supervised by professionals should opt for a VPN. High-quality VPNs are not free, but they have become quite accessible in the last few years and if you don’t want to learn how to code and cover your tracks going with a VPN is probably the best choice.
Le VPN offers an easy-to-use VPN software for all devices, available on a subscription-basis from $4.95/month, with additional free features of a SmartDNS service, a HybridVPN connection and access points to IPs in 100+ locations around the world. Try Le VPN now with a 7-day money-back guarantee.
*Article Updated On January 2nd, 2019.*
SUMMER SALE
First 3 years for $2.22/mo
NO LOGS
100+ LOCATIONS
P2P ALLOWED
Easy To Use
30-Day Money Back
Friendly Support
Bitcoin Accepted
Ultra High Speeds




Written by Vuk Mujović @VukMujovic
Vuk Mujović is the founder of MacTíre Consulting, an analyst, data management expert, and a long-term writer on all things business & tech. He authored blogs, articles, and opinion pieces aimed to help both companies and individuals achieve growth without compromising their security. Vuk is a regular guest author to Le VPN Blog since January 2018, where he gives his expert opinion on the topics related to cybersecurity, privacy, online freedom, and personal data protection. He also often shares his tips and best practices in relation to internet security and digital safety of private individuals and small businesses, including some additional applications of using a VPN service.