Is your ISP watching you is not the question you should be asking, you should be asking what are they doing with the data they collect.
Do Internet Service Providers Monitor Your Traffic?
To ask the question do ISPs watch what you surf, or if they monitor your traffic is naive. Of course they do. It’s their business to monitor it and in some cases they are required by law to do it. What you should really be asking is what they are watching, what they are collecting, what they are doing with it and what you can do about it.
How do Internet service providers track your browser history? Easily. When you connect to the Internet you are doing so through a gateway provided by them. For the average user this means using a router and WiFi unit provided by them and a connection that is as plain for them to see as the nose on your face. Each user of the net is assigned an IP address that is tagged to their devices and blasted across the Internet for anyone to see. Without taking the proper precautions, precautions that most Internet users are oblivious to, your computer and routers are constantly sending information across the web and/or directly to the ISP that are tracked, logged and sold to the highest bidder.
- The worst part is that data collected by ISPs can be aggregated into files and dossiers that will eventually include names, addresses, financial history, medical records and even video clips and images. By default most Internet queries are routed through an ISP’s own DNS server. Because DNS queries are almost never encrypted this means the ISPs can see, log and track every website you visit. More about DNS leaks in this article.
Do ISPs sell your data?
They say they don’t but . . . In early spring 2017 US President Donald Trump signed new laws repealing protections on browsing data. With these protections no longer in place ISPs in the US are free to monitor, record and sell to their hearts content. The Catch-22 is that the new laws repeal laws that have not yet gone into place, if you can follow me on that. The Obama administration had passed laws set to go into effect late in 2017, the news laws stop them from being enacted which means nothing has really changed for US Internet users.
While intended to increase competitiveness among the smaller ISPs, critics say it was meant to do one thing and one thing only: to allow ISPs to profit from collected data. After all, data is big business. It is what drives Internet thieves to hack into the databases of retailers, corporations, health care facilities, financial institutions and governments. In most cases it’s not even illegal, a simple search online will turn up dozens if not hundreds of legitimate businesses selling databases of all variety. The value of data collected by an ISP is enormous. Where a single website can collect data about your usage of that site, the ISP can collect data about your usage of all Internet sites including the data you transmit to and from them.
The ISPs argue that they have to collect the data in order to be competitive. Websites like Google and Facebook are powerhouses of data collection and able to provide advertising targeted to your age, race, gender, sexuality, athletic ability and political associations. In order to provide the same value they need to be able to collect as much data as they can, and all at our expense.
Advocates of Internet privacy say this is an apples to oranges comparison since the ISPs are there to connect you to the Internet while the websites are there to provide content across it. When you use the websites you give them consent to collect and track you in exchange for their services. When you use an ISP you have to pay them to connect, and then they want to collect your data and make money on the back end too.
The largest telecom and ISP providers have been fighting the intended restrictions for some time. The basis of their argument is that the data is not sensitive data and therefore not subject to the same protections as social security numbers, bank accounts and passwords. The risk of course is not so much in the collection of the data but in how it is used. The data could be used for profiling by age, orientation or political views, or used by police or governments to target opposition.
- Not all of today’s websites are secure, even ones that collect and store sensitive information. If your ISP is collecting URLs associated with your name or other identifying information, the information could be used to backtrack your accounts and allow unwanted access.
The long term effects of ISPs monitoring browsing history on Internet are largely unknown but experts agree it could have a serious impact on some aspects of web use. Individuals may choose to reduce and temper their use of the net in order to protect their identities and possibly their reputations. A businessperson or a small business owner at risk of having browsing history revealed publicly is less likely to use the Internet than one who isn’t.
The largest ISPs including AT&T, Comcast, Verizon and others have all come out saying they will not sell data to third parties. It is in fact in their interests not to do so as it could adversely affect their reputations and businesses. What will likely happen is that the data sets will be used to help target ads in some form. A company could go to an ISP and say I want to advertise to demographic XYZ what can you do for me? Regardless the use a question remains, how are the ISPs going to deliver targeted ads to me unless they co-opt my connection and send a nasty little pop-up ad straight to my screen?
We Generate A Lot Of Data
To put things into perspective lets think for a minute about how much data we as individuals generate on a daily basis. The amount of data is directly proportional to the number of connected devices you have and how much you use them. The Internet of Things has supercharged data creation and it is only going to get worse. It’s been estimated that by 2020 there will be more than 50 billion connected devices, that’s more than 6 per person, and each one providing another opportunity for an ISP to track you.
Today’s average Internet user probably has 3 or 4 connected devices: a phone, a computer, a lap top, maybe a tablet, or a wearable, a TV or some other household object. We wake up in the morning using the alarm on our phones, check in with emails, social media, news, weather and go about our business. We carry our phones in our pocket all day long, with the GPS and Bluetooth turned on no doubt, and all the while the ISP is collecting data. They collect so much data, along with everyone else on the web, that there is a whole branch of computer science dedicated to it: Big Data and Data Mining.
Big Data and Data Mining are a combination of disciplines that seek to collect, store and utilize sets of data so big, complex or growing so rapidly traditional methods of analysis can’t make sense of them. It can be used to determine trends within a population, control the spread of infectious disease, spot criminal activity as it is happening as well as profiling individuals, tracking the spread of political ideology and connecting disparate bits of information into a virtual you complete with likes, dislikes and expected responses.
What exactly do they collect? For the most part is metadata, things like IP and port addresses for routing traffic through the Internet. It may also include the urls of websites that are being visited as well any data being sent across it, although that is more difficult and carries less value for the ISPs, there are, after all, limits to what they can collect. They aren’t allowed to actively collect personal or personally identifiable information or the content of messages and transmissions but that doesn’t matter. Researchers have found that over time metadata can be very revealing. A string of visits such as AbortionFacts.org, PlannedParenthood and GoogleMaps can be telling, when combined with other bits of data could be damming.
Can ISPs See HTTPS?
HTTPS or Hyper Text Transfer Protocol Secured is an upgraded evolution of Internet protocol that includes security. Its purpose is to force authentication of visited websites and the integrity of transmitted data. It works by authenticating the websites and associated servers in order to prevent man-in-the-middle attacks with the addition of encryption to protect from eavesdropping and data leakage. Many websites today have switched over to the new protocol but some have not and even those that have often times revert back to the old HTTP to improve connection speed.
The real problem when it comes to ISPs monitoring traffic is that the HTTPS doesn’t hide your connection from them. The ISP can still see the connection, where it is going and where it is coming from which is more than enough to be worthwhile. Encryption is even turning out to be a two-edged sword. While it protects the contents of transmissions data scientists have found a number of ways to exploit encrypted connections. By tracking the size, timing and destination of the packets it is possible to predict what those packets contain, otherwise known as side channel information. Governments that monitor and censor the Internet are able to disrupt connections based on this type of information.
A few possible uses of side channel information:
- Website fingerprinting
This is not a new technique and one that allows an ISP to identify websites based on their secondary characteristics. Each website is unique in how it operates. They send differing amounts of content, they load different third party applications and in different orders. An ISP can use this information to identify specific websites even when the content of transmission is encrypted. An early study showed that 60% of websites could be identified in this manner, since then some counter-measures have been created but it is still possible to accurately ID a site more than 50% of the time.
- Search Queries
Auto-suggest, you know what I’m talking about. That little feature on Google and Yahoo and all the other search engines that use the first characters that you type to predict and suggest websites you may be interested in. Researchers have shown that by analyzing the size of suggestions on the encrypted list of returns they can predict which letters were typed and eventually the entire search query.
- Side-channel IDs
Researchers have proven a number of times they can infer a user’s health or financial condition based on side-channel information even when a website’s use is completely encrypted.
What You Can Do To Stop ISPs From Monitoring You
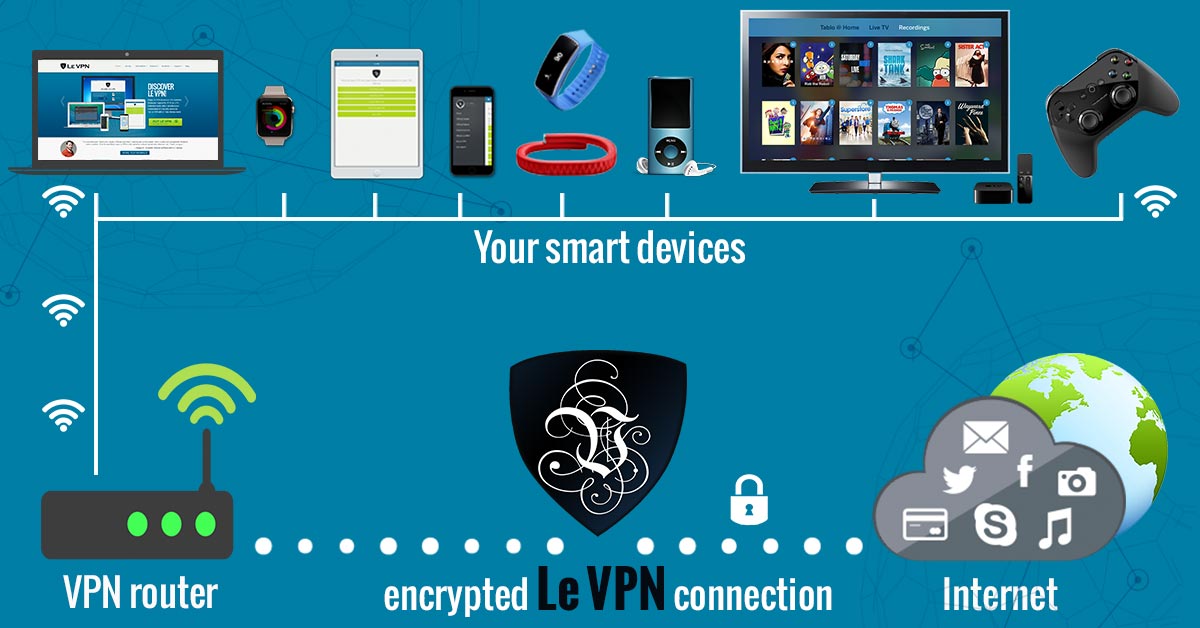
The first thing to do is the stop using routers and Wi-Fi provided by your ISP. It’s not a given but it is possible for them to install tracking software that will make anything else you do to prevent it useless. It is a simple task, routers can be easily purchased on Amazon, Google and dozens of other websites but be warned, your ISP may know what you are up to. Even better is to use a VPN router. More about VPNs later.
The next thing you can do is to use the TOR Network although it is not a foolproof method of anonymizing and protecting your use of the Internet. TOR, The Onion Router, is a non-profit project intended to help protect online privacy. It is a system of routers that like an onion have many layers. When you download and use the TOR web browser you connect to this network. When you search and travel to a destination website your signal is bounced through a series of browsers hiding your true identity and anonymizing yourself. The problem with TOR is two-fold. The first is that your connection to TOR and exiting from TOR are not protected so it is possible to be found, logged and tracked. The second is that TOR has found an unintended use as safe haven for all the nasty things the Internet has to hide. Scammers, drug dealers, child pornographers and fetishists of the most repulsive kind can be found if you know where to look so the mere use of TOR is of interest to the ISPs, the police, governments, etc..
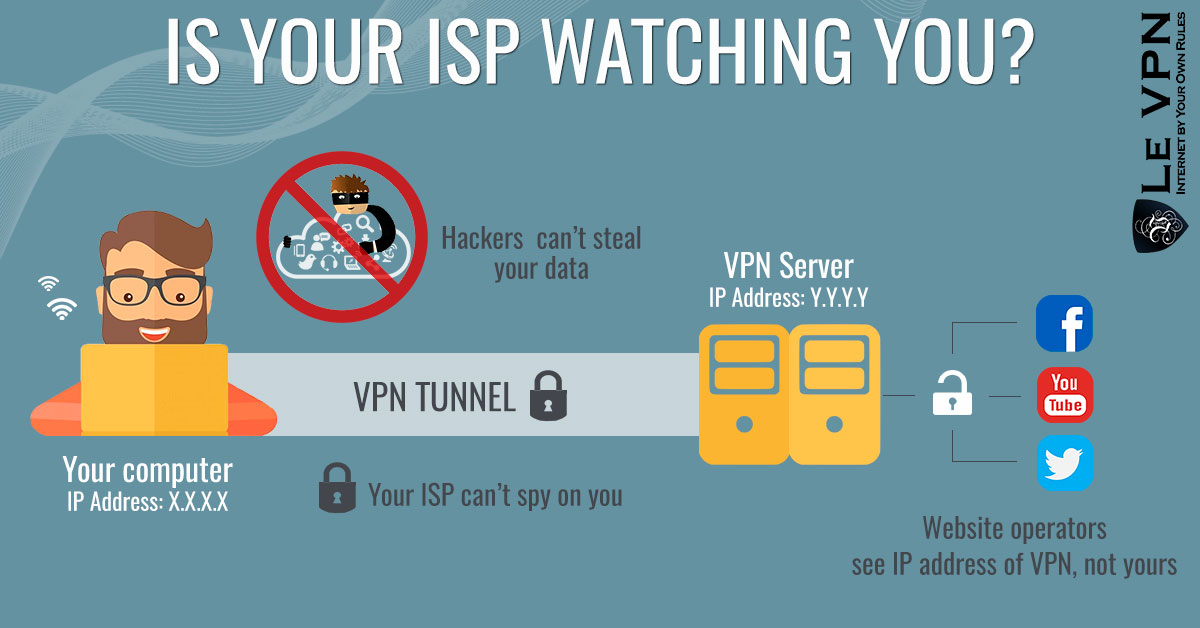
The best thing you can do for yourself is to use a VPN. Using a VPN means you don’t have to worry about your ISP’s devices and you don’t have to use TOR, not unless you just want to. It is a useful tool. VPN stands for virtual private network and it is the oldest buzzword in computer security you never heard of. Dating back to the very origins of the Internet as we know it, it is the very technology that the government uses to protect itself and technology they don’t really want you to be using. Why? Because if you did, they wouldn’t be able to find, track or monitor you if they wanted to and most of the world’s Internet security issues would disappear.
The VPN is actually a combination of technologies derived from ARPA and private sector research. When the Internet was created it was intended to connect two remote locations over public wires, which in those days were the phone lines. They needed a way to be sure their connections were as safe and secure as if they were made on a private network and that is where VPN comes in. It works on two fronts to anonymize, mask and secure connection in order to protect transmitted information as well as identity the user.
On the one hand the VPN software downloaded to your computer or device re-assembles the data packets into new, anonymous packets with no marks identifiable to you. These data packets are sent across the ISP’s Internet connection to a network of dedicated VPN servers. It is this network that makes VPNs hard for an individual to deploy and the real value in purchasing a VPN subscription. The data packets bypass the ISP’s servers in favor of the VPN servers creating an effectively invisible connection: the ISP may see the connection but they won’t know where it comes from or where it is going. To further secure the connection the data packets are authenticated by the VPN server to ensure proper transmission and avoid attack. The data may also be encrypted to ensure that it will never be used. Once your connection leaves the VPN server, it carries a new IP address, further anonymizing you, putting the final brick into place.
Top VPN provider Le VPN has a network of VPN servers in more than 100+ locations worldwide. These servers support 4 protocols to suit any web surfing need and come at a cost of only $4.95 per month with a 1-year plan. Each plan will support an unlimited number of devices with 2 connections active at any one time. For those wishing to secure a home or business, Le VPN has VPN enabled routers that will establish a master connection to the VPN network that any device within range can access. If you are scared of ISPs’ monitoring and you should be, you need to get Le VPN now.
*Article Updated On November 7th, 2018.*
SUMMER SALE
First 3 years for $2.22/mo
NO LOGS
100+ LOCATIONS
P2P ALLOWED
Easy To Use
30-Day Money Back
Friendly Support
Bitcoin Accepted
Ultra High Speeds





Written by Vuk Mujović @VukMujovic
Vuk Mujović is the founder of MacTíre Consulting, an analyst, data management expert, and a long-term writer on all things business & tech. He authored blogs, articles, and opinion pieces aimed to help both companies and individuals achieve growth without compromising their security. Vuk is a regular guest author to Le VPN Blog since January 2018, where he gives his expert opinion on the topics related to cybersecurity, privacy, online freedom, and personal data protection. He also often shares his tips and best practices in relation to internet security and digital safety of private individuals and small businesses, including some additional applications of using a VPN service.