For as long as the internet has existed, there has been a need for protocols to keep data private and secure. The history of VPN (virtual private network) technology dates back to 1996, when a Microsoft employee developed the peer-to-peer tunneling protocol, or PPTP. Effectively the precursor to modern VPNs, PPTP creates a more secure and private connection between a computer and the internet.
As the internet took off, demand for more sophisticated security systems arose. Anti-virus and related software could be effective at preventing damage at the end-user level, but what was really needed was to improve the security of the connection itself. That’s where VPNs came in.
A VPN is a private connection over the internet. It’s a broad term that encompasses several different protocols, which will be explained in detail later. What they all have in common is the ability to connect remotely to a private network over a public connection.
Initially, VPNs were used almost exclusively in business. However, the rash of high-profile security breaches occurring in the early 2000s was a key moment in the history of VPN technology. With this, everyday internet users became aware of the true risks of working online, and began to look for more secure ways of doing so.
Today, VPNs are used to secure internet connections, prevent malware and hacking, ensure digital privacy, unlock geo-restricted content and hide users’ physical locations. Easier to use and more affordable than ever, a VPN is an essential tool for staying safe and secure online.
What is the Purpose of VPN?
- The VPN purpose is to create a private connection between multiple people and devices across the Internet. In effect it is an Internet within an Internet, secure private and encrypted from prying eyes, malware, hackers and anyone else who may wish to know where you surf, or where you are surfing from.
VPN Technology has been around for decades. Originally created for big business it was never intended for the many purposes to which it is used today. The need at the time was great. Businesses, organizations, governments and many others with sensitive information were at risk of hacking or other loss of data when using open Internet connections. They needed to make connections that were far more secure than the average so that remote users, satellite offices and field operatives could access and use company files without allowing their secrets to escape. The solution they derived is VPN.
VPN is like having a local network, a network in which devices are directly connected to each with no need for the internet, except using the internet to make the connections. Aside from tunneling protocols which set up secure connections hiding the originating source high level encryption standards ensure that even if data is lost, it will never be used by anyone not intended to have it. The benefits of VPN for individual internet users became clear right from the start and that spawned the modern rush to provide the best VPN technology. Over the years VPN advancement has been spurred by the encroachment of censors around the globe, and the never ending appeal for hackers to break into whatever devices and connections they can.
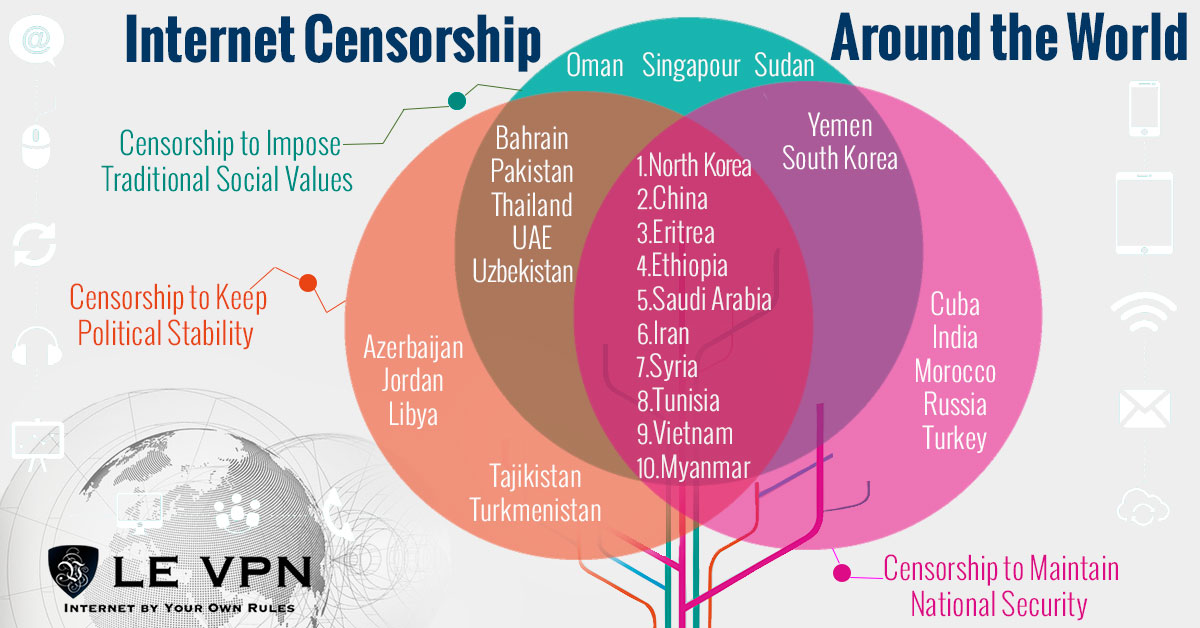
Censorship and geo-restriction is one of several issues plaguing the Internet and driving innovation in VPN technology. The history of censorship varies from case to case but includes things like blockages of social media, incomplete access to online media catalogs (note Netflix US catalog versus what is available to the rest of the world), tracking user activity, monitoring emails or outright denial of access to the Internet. The history of VPN has progressed right along side it, overcoming each issue as it arises and generating demand from the web-surfing public.
- If you don’t think that internet security is a problem just look at websites like Wikileaks and whistle-blowers like Edward Snowden. They have shown how governments and individuals have flagrantly disrespected international law and personal privacy by spying over the Internet. In most cases websites that collect your data do so for innocent purposes but that is not always the case. Facebook is a notorious collector of personal data that it shares across its apps and uses to “enhance” the user experience.
- The Internet makes sharing information and content quick and easy. The problem is that as fast as Internet technology advances so to do efforts to control the flow of media, information and ideas. VPNs can unlock geo-restricted content from the BBC, ABC, Hulu, YouTube and many others while protecting your identity, your physical location and your devices. This service is particularly valuable in countries with strict control of the World Wide Web and the content their citizens are allowed to access.
- Even today’s best technology may be at risk. We know from the Snowden leaks that the NSA was actively working to undermine commercially available encryption, IT and networking technology and IPsec is believed to have been included. The work they accomplished made many of the VPNs at the time vulnerable to intercept and decoding, it also led to more advanced and secure VPN technology.
The Evolution Of Internet Privacy Technology
We know longer sling buzzwords like frame relay or packet switching but they remain relevant even today. These terms are the hallmark of remote connectivity technology and led to today’s point-to-point protocols and the creation of VPN. The Internet allows everything to be connected and within the broader fabric of global connectivity are smaller dedicated networks which provide heightened security. What they do is simple, VPN connects remote locations over a public network. Security comes in three layers, the tunneling protocol, authentication and encryption. The tunneling protocol creates the connection and then data is encrypted before being sent through to the end point to be authenticated and decrypted.
There are three basic types of VPN: IPsec, SSL and mobile. IPsec stands for Internet Protocol Security and is the standard type of VPN used to create connections between two networks and individual devices with networks. This traffic is encrypted and authenticated and, because it works at the IP layer, is the best general purpose VPN available, providing end to end security at all levels of connectivity. The only problem with IPsec is that implementation can vary from provider to provider causing difficulty when interconnecting. Using VPN from the same source, or having an IT professional on hand, is recommended.
SSL, Secure Socket Layer, is a form of VPN that most internet users have already employed and don’t even know it. This protocol is used for connecting a single user to a website portal such as ecommerce. It creates an encrypted VPN connection protecting transactions and loss of data. The SSL uses the web-browser for its interface making it easy for small and medium sized businesses to deploy. The downside are limitations with functionality that make the IPsec connection more practical for complex applications.
A Few Key Moments Of VPN History . . .
For there to be VPN and Internet security there first has to be an Internet so let’s start there. There were computers and computer networks before the Internet but it was the work done on behalf of the Department of Defense that led to the Internet in use today. Research on an electronic method of communicating with remote locations began as early as the 1960’s by US military intelligence. They created a packet switching network called ARPANET (Advanced Research Projects Agency Network) and the first use of TCP/IP. TCP/IP stands for Transfer Control Protocol/Internet Protocol, the two functional units of the first network of networks.
The TCP/IP protocol suite set the standard for computer networking as we know it today; HTML, hyperlinks, the works. Eventually this research led to the institution of the Internet Protocol Suite as a standard of military communication, 1982, and to the later adoption of the standard by the commercial computer industry in 1985. Many of the large corporations such as IBM and AT&T adopted the new technology quickly even though their own internal networks were different because it made interconnectivity of disparate networks a reality, and easy.
The TCP/IP details how all information is packetized, addressed, transmitted and received across the Internet. It operates in 4 layers; link, internet, transport and application. The link layers is where devices within one network operate and where they are safest. The internet layer is where local networks and devices connect to other websites and the Internet at-large and where they are at the most risk. When data packets are sent from a local network to a destination network the packet is marked with information identifying where it originated and where it is going. The system works well but is flawed in that prying eyes can monitor traffic, intercept data and even follow the flow of data back to the source and identify it.
- IP Address – The IP address is a 32-bit number assigned to all devices connected to the Internet using the Internet Protocol Suite. It serves two important purposes but can be abused by hackers and malware. These are identification and addressing. The number identifies you to other networks which use it to address data packets in order for the router to send them to the correct places. The 32-bit system is known as IPv4 (Internet Protocol Version 4) but IPv6 is already in launch. The reason there are two systems is that the first, IPv4, has a limited number of possible addresses and they are running out fast.
- IP Packet – A set of data to be sent over the internet, known as the payload. It contains address headers and other identifying markers as well as the payload and is at risk when transmitted across the Internet. The Internet Assigned Numbers Authority is in charge of IP addresses and assigns them in blocks to ISP’s (Internet Service Providers) and others with need.

Obviously, by this point the need for network and Internet security was clear. Security technology was first researched in 1993 by John Ioannidis and his contemporaries in think tanks such as Columbia University and AT&T Bell Labs. His work led to the Software IP Encryption Protocol, also know as SWIPE, the earliest form of VPN. It was an experimental work which sought to provide confidentiality, integrity and authentication for network users.
Following this work Wei Xu began his own research in 1994, focused on IP security and enhanced IP protocols that eventually led to the development of the IPsec system. IPsec is an internet security protocol suite that authenticates and encrypts each packet of information shared across the Internet. As the technology was advancing so to did the speed of connection. IPSec and faster connection speeds, along with the development of the plug-and-play feature, is what made commercially available VPN a reality.
At the same time IPsec was created work at the NAVAL Research Library, under a grant from DARPA, created the Encapsulating Security Protocol. It is a security extension for SIPP later adapted for more advanced systems and another major break through for Internet security and VPN technology. Encapsulating Security Payload, ESP, provides authenticity, integrity and confidentiality protection for data packets. It will support encryption-only or authentication-only configurations but there are less secure than using both. This protocol is similar to but different from Authentication Headers and provides a second layer of security to Internet connections.
In 1995 the IPsec working group was created within the IETF. The IETF, Internet Engineering Task Force, is a global community of Internet engineers, developers, programmers, vendors and other interested individual concerned with the evolution of the Internet and its smooth operation. This task force has worked over the years to create a standardized set of freely available and vetted protocols addressing the components, extensions and implementation of IPsec.
The IPsec protocol utilizes three sub-protocols for implementation; Authentication Headers, Encapsulating Security Payloads and Security Associations.
- Authentication Headers provide connectionless data integrity and authentication for IP Packets as well as protection from certain types of network attacks. Authentication is important because it ensures that the data packets you send and receive are the ones you want, not malware or other potentially harmful attack. There are several versions with varying degree of protection at different levels. In all cases the IP Packet Payload, your data/content etc., is protected.
- The Encapsulating Security Payload provides confidentiality for those packets as well as data origin integrity, safety from attacks and some security for traffic-flow. When used in Tunnel Mode provides security for the entire IP Packet.
- Security Associations are the algorithms and data that allow the AH and ESPs to function. Basically, data is encrypted into packets at the source and then transferred anonymously over the Internet to be received, authenticated and decrypted at the destination. Associations are created based on the Internet Security Association And Key Management Program (ISKAMP) using a series of numbers. If used within a group Association Keys can be modified per individual per security levels within the group.
- Two modes of operation are available: Transport Mode and Tunnel Mode. In Transport Mode only the IP Payload is typically encrypted, securing the data but leaving the originating information visible. In Tunnel Mode the entire IP Packet is encrypted and encapsulated, given a new Authentication Header, and then sent on. Tunnel Mode is the technology that drives today’s VPN.
The tunneling protocol, Tunnel Modes, is what allows VPNs to function as they do. It allows, among other things, a user to connect remotely to a network with an IP address that is not part of the local network. Tunneling works by altering the form of data, i.e. encrypting and encapsulating, which provides a third and highly sought after benefit: anonymity and privacy. The way it works is a little complex, the packets which contain the information that run the encryption and delivery service are held within the payload of the original message but operate at a higher level than the payload itself, creating a shield formed from within and safe from outside influence. The very best services will encrypt the entire packet, identifying marker and all, then re-encapsulates it with a new IP address and identifying mark for complete privacy.
The Future Of VPN Is Bright
The earliest VPN did the simple job they were first intended to do, allow remote access to a home network, but opened up a world of possibilities both good and bad. The earliest versions, while intending to provide safety and security, were often vulnerable to attacks which blocked or intercepted the flow of data. They were also very slow to transfer data so not as useful in real-time situations like they are today. Later versions have improved upon the original ideas, merging and advancing technologies along the way. Today’s modern VPNs are a versatile, adaptable and desirable tool for Internet users at all levels of the spectrum.
Benefits for the individual include secure connection to the Internet and websites on it, privacy/anonymity and safety/integrity of your data, personal information, business network etc. Benefits for business include seamless secure connection between branch offices, remote users and web surfing customers with the home network.
The need for VPN is clear. The Internet is not a safe place, it is in many ways a wild west of networks, devices, good users and bad users. Connections are at risk of hacking, websites may download malware, personal data is hunted and the flow of information is impeded. Even in places where the Internet is relatively safe you will encounter restrictive activity which blocks the free flow of information ranging from global news to the most popular US and British TV shows.
This means that the VPNs are as important to Internet security, and Internet use, as they ever were and that more people should be using them. VPN creation will continue to advance alongside the internet and as its benefits become more widely known, so will its use. If you don’t already use VPN there is no reason not to and every reason you should, why wait, get Le VPN now.
*Article Updated on August 17th, 2018*
SUMMER SALE
First 3 years for $2.22/mo
NO LOGS
100+ LOCATIONS
P2P ALLOWED
Easy To Use
30-Day Money Back
Friendly Support
Bitcoin Accepted
Ultra High Speeds





Written by Vuk Mujović @VukMujovic
Vuk Mujović is the founder of MacTíre Consulting, an analyst, data management expert, and a long-term writer on all things business & tech. He authored blogs, articles, and opinion pieces aimed to help both companies and individuals achieve growth without compromising their security. Vuk is a regular guest author to Le VPN Blog since January 2018, where he gives his expert opinion on the topics related to cybersecurity, privacy, online freedom, and personal data protection. He also often shares his tips and best practices in relation to internet security and digital safety of private individuals and small businesses, including some additional applications of using a VPN service.
Comments (1)
You’re missing USA on your list of countries that censor. The actual government might not technically be censoring, but large private companies are censoring the crap out of people with over half of the government totally on board or even potentially being the driving force behind it all.