Do you know how to avoid the common mistakes made by Internet users today? How about the little tricks used by Internet experts? Read on to find out now!
Common Internet Security Mistakes And Tips To Avoid Them
The Internet. It is a part of our every day lives. It touches us in ways we don’t even know, a little disconcerting when you think about what that means. Devices, smart devices, the Internet of Things, digital marketing, eCommerce, governments, regulators, censors and just about every website you will encounter is out looking for you, for your information, so they can build their databases, tag their potential targets and then do… whatever is they have planned for you. In most cases this means enhancing your online experience by providing ads, content and other resources that you specifically are interested in. In the worst cases it may mean having a jack-booted storm-trooper come crashing into your home in a Kafkaesque breach of your personal security. Savvy Internet users don’t just sidle up to the web and log on. They take precautions to protect themselves, their equipment, their connections, their data and their digital presence. Do you know what it takes to surf the web with safety and security?
Using The Internet Like A Boss
One of the most common mistakes made on the Internet is understanding what it is. The Internet. It’s really a thing, it’s not some machine sitting out somewhere in a field that everybody connects to. The Internet is a method of connecting information networks together. In the old days, back when the Internet as it is known today first came into wide use, it was intended as a method of connecting already existing digital networks together using a system of addresses. In those days most large corporations and government agencies had some form of local network, usually proprietary to the organization, the Internet was a means of connecting those networks together for the purposes of sharing information.
It was, is, known as the Internet Protocol or IP and is the IP portion of TCP/IP. The addresses, IP Addresses, are the numbers that tell a router which computer in which location your device wants to connect to. It sends a signal, acknowledgments are made, a connection is set using whatever combination of telephone, coaxial, fiber optic and other wires are available between you and the end point. When you log on to your computer, using a browser such as Google Chrome or Firefox, you are blasting your address all across the internet to whichever computer, software or user chooses to receive it.
Nowadays just about everyone, every organization and every business on the planet has at least a device with which to connect if not a social media page, blog, eCommerce website or other online presence and most of them collect information about you and your interaction in some for or another. At last count there was an estimated 644 million active websites on the Internet. The average lifespan of a website is only about 3 months and new ones spring up every minute so it is hard to keep an accurate tally. The point is, there are a lot of potential security risks when it comes to the internet. The key points of focus are limiting your information and who has access to it, protecting your IP information from unwanted prying eyes, securing your connections and keeping it all safe with the added layer of encryption.
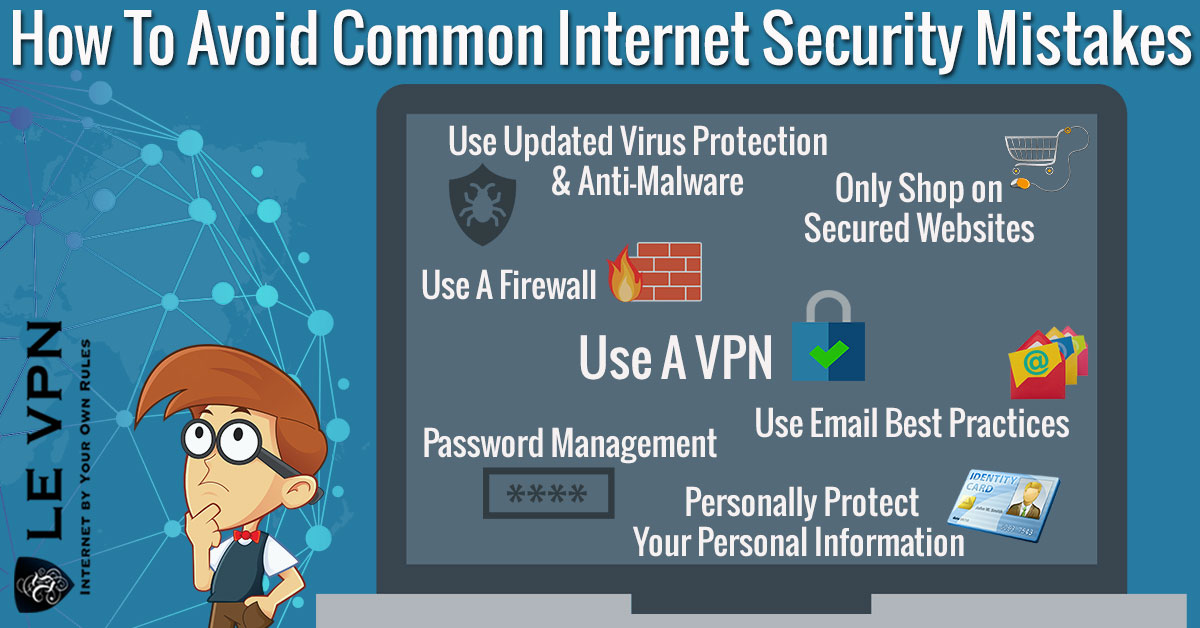
Savvy Tips & Tricks To Better Use The Internet
- Use/Update Virus Protection and Anti-Malware.
Believe it or not there are still people surfing the net without protection, or without updated protection. Believe me when I say this is the first line of defense any Internet user has and is one of the most important steps in any online security scheme. You never know when you will encounter a file, a website or a user who will want to infect your devices. Keeping malware up to date is the best way to protect against the latest threats, as they emerge. The good news there are lots of free anti-malware packages available for download and most will allow you to set up an automated schedule for updating the software and the list of threats.
- Use A Firewall
Simply using anti-malware isn’t enough though, the addition of a firewall is a must and no, they do not do the same thing. Anti-malware protects your devices from having suspicious, malicious or otherwise harmful and security breaching software installed on them. A firewall is more an all-purpose security precaution, like a doorman, that typically requires you to give permissions for outside access or for software to be downloaded, giving you final approval before changes are made to your computer. If a threat sneaks in through the firewall the anti-malware come into to act like the night club bouncer and remove it.
- Use Email Best Practices
Email, in this day of instant messaging, is still the top form of communication between internet users and for malicious internet behavior. Criminal activity ranges from the ridiculous Nigerian email fraud through delivery of highly infectious and damaging malware that in most cases, the receiver allowed to infect their device. Despite its widespread, rampant, use for fraud many still do not appreciate the need to use email best practices. These include only opening emails and files from trusted sources, only giving out your email address to trusted websites, not opening spam or junk mail and avoiding phishing scams. Phishing scams are those websites that offer something, if only you’ll send in your name, address and ID#.
- Password Management
Password management is crucial to digital security, and any form of security. I know, it is a real pain in the rear having to set up all those passwords. No website seems to want to accept the same inputs, all caps, one caps, no caps, case sensitive, not case sensitive, use x amount of digits, use letters, letters and number, letters/numbers and special characters and the variations go on and on. In effect, the Internet community is forcing you to do what you should be doing on your own; using different passwords everywhere you go and changing those passwords regularly. Think about this, a malicious hacker runs a program that scours the net looking for username/password combinations then matches them to every known email server. When he finds yours he get into your email account, if you have all the same passwords for all your other accounts he has access to them too… bank, credit cards, retirement accounts.
- Personally Protect Your Personal Information
Assuming that you’ve taken all precautions protecting your personal information comes down to how you yourself personally handle it. Like the old sayings go, Loose Lips Sinks Ships and Beware of Strangers With Candy. If you put up your every personal detail on social media in some other profile on some random website there is a chance that anyone could find it and use it. Be careful what you put on the internet and be careful who you share it with. You may think it OK for a site to ask for a name, a number, an account but ask yourself these things: Who is this asking for my information? What are they going to do with it once they have it? Why do they need it? How is my security going to be affected if this information gets out? Where are the potential leaks and threats? If you aren’t comfortable with the answers using that site and giving up that information may not be worth the risk.
- Only Shop/Use Secured Websites
All the security precautions in the world make no difference if you connect to an unsecured website. Once that connection is made you become vulnerable through them and could easily suffer loss of data or worse. The first thing to look for is the HTTPS heading in the web page address, the S at the end stands for security and is the enhanced version of the old HTTP. Other quick signs you are using a secure site are the padlock symbol alongside the web address or the TRUSTe emblem. Whenever transferring data or making a purchase, be sure that SSL encrypted connection is available.
- Use A VPN
A personal VPN service, Virtual Private Network, offers a complete security protocol that protects users from end to end, filling in the gaps left by firewalls, malware and best practices. First intended as a means for remote users to connect with a home network (mega corporations and government agencies) over the Internet they are now a commercially available product. The VPN creates a point-to-point connection that is protected by encryption and routed through remote servers. It provides a secure, anonymous connection (your IP address is masked and replaced when routed through the remote server) that begins with your device and ends at the destination address through which encrypted data is sent. This means that hackers and malware can’t find your connections to tamper with, and if they do happen to stumble upon you they won’t be able to read the data being transferred, or follow the connection back to your device. They are most commonly used to make secure connections through unsecured public WIFI access points, to unlock geo-restricted content on international websites and to provide point-to-point privacy, limiting the spread of personal information and anonymity for web surfing.
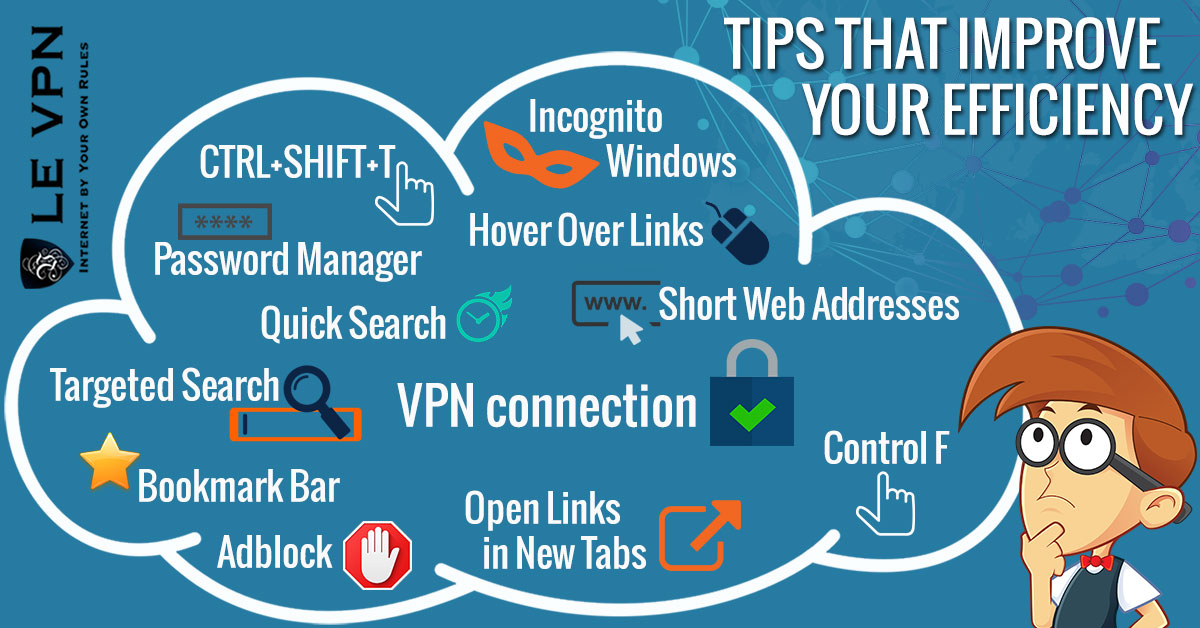
How to Improve Your Efficiency While Using The Web
How to be an internet professional is all about how you use the web, how to be proficient in using the web is all about short cuts. The true pro knows many smart ways to better use the Internet so their time is spent more efficiently as well as with more security. This is our list of tips, tricks and hacks to be more efficient on the Internet in every day usage.
- CTRL+SHIFT+T
Did you accidentally just close the wrong browser window and lose an important website? No problem just use this little short cut to instantly open whatever the last page was. If you are using Mac OS the short cut is Command+SHIFT+T.
- Use Incognito Windows To Your Advantage
Many of us use a variety of Google products, and a few of us have found it useful to have more than one Google account to use these products. Google makes it easy to log in to all their products with easy entry but what they don’t allow is for more than one user to be logged into Google in the same browser at the same time. You can get around this little problem by opening an Incognito Window. This little trick opens up a new browser window that is anonymous to the web that you can use to log into a second, or a third, Google account. The shortcut, to avoid having to go through the Google Settings Tab, is Control+Shift+N.
- Use A Password Manager
Tired of all those different passwords and want a better way to manage them? Try a password manager like StickyPassword and forget about trying to remember them all. These services will remember the passwords for all your important accounts and keep them safely stored away, ready to be used when you need them. Accounts are web based so passwords remembered on one computer can be recalled on another.
- Only Connect With VPN
Using VPN to make all your connections helps limit the chances that your information and data will be leaked. It will also help ensure that hackers and malware are not able to target your computer, adding an extra line of defense to your firewall and malware protection. VPN can also mask your physical location in order to avoid geo-restrictions or being tracked back to your location.
- Targeted Search
If you are looking for a specific page or content on a specific website you can tell Google to search only that site by using the heading site: and the webpage in the search bar before the search query. This is especially useful on sites that have lots of information, a large number of pages and/or has poor internal linking and structure where it may be difficult if not impossible to navigate back to certain pages. Searches can be further refined with keywords and phrases specific to the material in question.
- Manage Your Bookmark Bar
If you are like me there are dozens of important websites in your daily routine. Getting to them quick is easy using the Bookmark bar on your browser but this bar can easily become overcrowded and cumbersome to use. Avoid this by leaving the name blank when setting up the bar so that only the webpage’s icon is shown. Any sites with hard to read icons can still be named, just use short names and utilize the space efficiently.
- Use Adblock
One of the many hurdles to a pleasant Internet surfing experience is the incessant popping up of ads and other promotional materials. These can be blocked at the network level using plug-ins like AdBlocker to provide ad-free connections for every device on the LAN.
- Hover Over Links
Want to see where a link goes but are afraid to click on it? Don’t worry, lots of other people are too and there is reason. You can save yourself the hassle of a possible bad link or malware attack by hovering over the link in the page in which it appears. This will force the destination address to pop up in the lower left hand corner of your browser window for you to see. If the link is good and you want to follow it, click it, if it looks like it might be a big waste of time move on to the next one.
- Open Links In New Tabs
Savvy web masters will have links on their sites open in a new tab so that you don’t lose the original website, a big plus, but this is not always the case. If you want to open a link and don’t want to lose your page and are not sure if a new tab will open there is a solution for you. All you have to do is hold down the Control/Command button while you click the link, depending on MAC or PC usage, and the link will be opened in a new tab.
- Quick Search
The fun of surfing the web is when one page leads to another to another as you learn and are exposed to new things. Each thing you encounter leads to a new search and a new tack but can be cumbersome to do. Highlighting the words, opening a new tab, pasting and searching can all be avoided by the simple click of the mouse. While using Google, all you have to do is highlight the word, right click on it and then choose “search with Google” and the rest is done for you.
- Control F
Reading long, small, detailed or otherwise hard to read text? Need to find specific wording within a text fast? The shortcut is simple, CTRL+F opens a search box that will scan the text for your words.
- Full Web Addresses
Full web addresses, you don’t really need them. When typing the name of a website in the address bar you can skip the https part and the WWW. part and go right to the name of the site. For example, to go to Le VPN’s website type in le-vpn.com and hit enter, the rest will be done for you. Another trick is to enter the name, le-vpn, and then hit CTRL+Enter and the full web address will be automatically created.
The Internet, Use It Wisely For Best Effect
The Internet is a great thing. It connects the world together in ways that were unimaginable only a few years ago. However, along with all the benefits come at least as many risks. Users must be aware of these risks and know how to protect against them in order to a satisfactory and enjoyable web surfing experience. There are several steps the individual user of the Internet can take to protect themselves but the best, the one that brings the power of mega-corporations and government agencies directly to your fingertips, is VPN. VPN offers the only point-to-point security system to safeguard your data, connections and devices so why wait, get Le VPN now.
*Article updated on August 8th, 2018*
SPRING SALE
GET 3 YEARS FOR $79.99
NO LOGS
100+ LOCATIONS
P2P ALLOWED
Easy To Use
30-Day Money Back
Friendly Support
Bitcoin Accepted
Ultra High Speeds



Written by Vuk Mujović @VukMujovic
Vuk Mujović is the founder of MacTíre Consulting, an analyst, data management expert, and a long-term writer on all things business & tech. He authored blogs, articles, and opinion pieces aimed to help both companies and individuals achieve growth without compromising their security. Vuk is a regular guest author to Le VPN Blog since January 2018, where he gives his expert opinion on the topics related to cybersecurity, privacy, online freedom, and personal data protection. He also often shares his tips and best practices in relation to internet security and digital safety of private individuals and small businesses, including some additional applications of using a VPN service.