Varenyky is a trojan horse which operates as a Spambot and it’s malicious software. If installed, it will record your screen when you visit an adult (pornography) website and/or when you search for any keywords related to adult content.
This threat appears to be targeting people who live in France especially customers of French ISP Orange SA but researchers said the malware may also target users on other ISPs or in other areas.
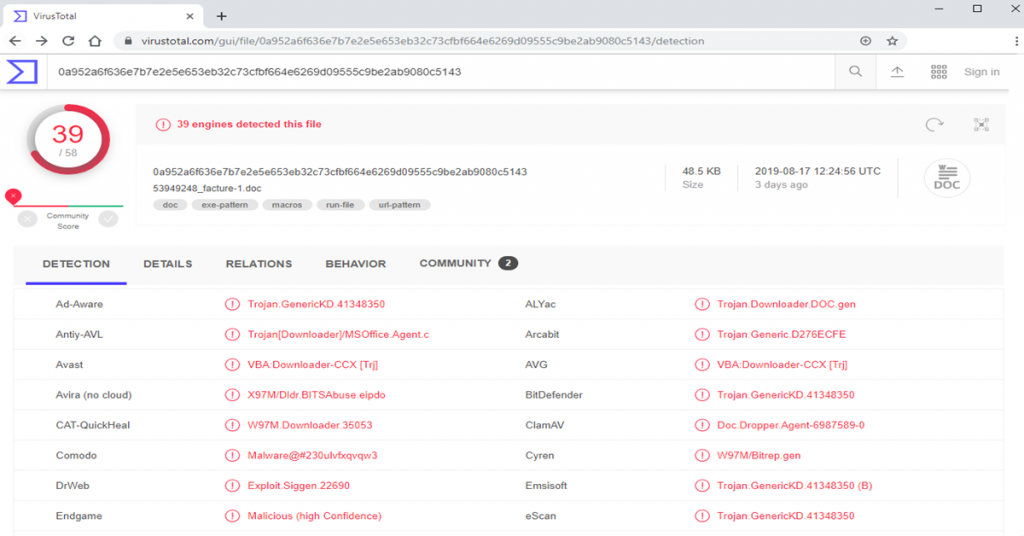
Test result on virustotal.com on Varenyky
Varenyky threat summary
Cyber criminals distribute Varenykky via spam Campaigns and they send emails with malicious files attached to them. One of the examples emails is as per below and the attached file is called 53949248_facture-1.doc.
Document ProtÈgÈ
Ce document est protÈgÈ par Microsoft Word et nÈcessite une verification humaine.
Veuillez suivre les Ètapes suivantes.
1. Naviguez vers le message ìMode protÈgÈî et cliquez sur ìActiver la modificationî.
2. Une fois cette Ètape faite cliquez ensuite sur ìActiver le contenuî dans la mÍme zone pour lire cedocument confidentiel, si vous ne voyez pas ce message cliquez sur “Activer les macros”.
As you can see, the email above looks legitimate and victims usually believe they’re opening a Microsoft protected document but in reality, if one clicked on the attached file, it will install malicious software on their computer and the cybercriminal would then send them another (threat) email after their screen been recorded, demanding for payment to be made in Bitcoin.
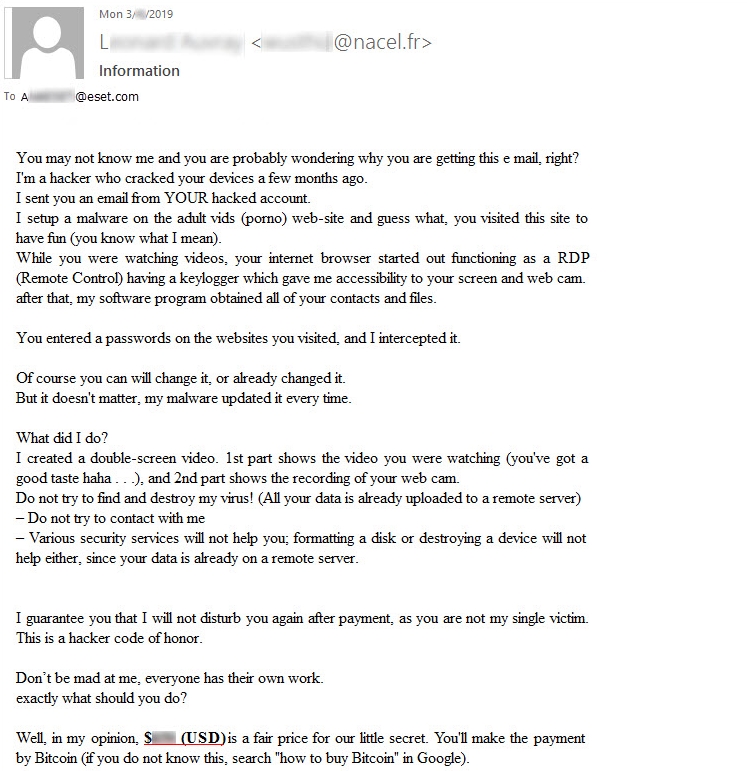
An English version of the threat email can be found below:
Conclusion
At the moment, Varenyky is not a Global threat yet and there is no proof of it successfully extorting anyone. According to ESET, the malware’s developers are tenacious. Many functions have been added and then quickly removed across many different versions in a short period of time (two months). This shows that the operators are actively working on their botnet and are inclined to experiment with new features that could bring a better monetization of their work.
Security experts say the best defense against malware is to keep your Operating System and antivirus software up to date, and avoid opening email attachments or downloading files unless you’re 100-percent certain they’re not dangerous. However, if you’ve already accidentally clicked on the attachment, you can follow the steps below to remove the malware.
• Start your computer in Safe Mode with Networking option.
• Run a full scan using your Anti-Virus software
• When the full scan is complete, remove the threats that are being detected.
• Restart your computer in normal mode.
Tips
By using a premium VPN, such as Le VPN, your cybersecurity is increased immensely, as the first line of defense. As a rule of thumb, don’t click on any links or attachments that is suspicious and if you received email from an unidentified sender, simply delete them.
SUMMER SALE
First 3 years for $2.22/mo
NO LOGS
100+ LOCATIONS
P2P ALLOWED
Easy To Use
30-Day Money Back
Friendly Support
Bitcoin Accepted
Ultra High Speeds